A not too long ago discovered malware builder known as Quantum Builder is staying employed to produce the Agent Tesla distant entry trojan (RAT).
“This marketing campaign characteristics enhancements and a shift toward LNK (Windows shortcut) information when as opposed to equivalent attacks in the previous,” Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar claimed in a Tuesday generate-up.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Marketed on the dark web for €189 a thirty day period, Quantum Builder is a customizable device for making malicious shortcut data files as effectively as HTA, ISO, and PowerShell payloads to supply following-phase malware on the specific equipment, in this scenario Agent Tesla.
The multi-stage attack chain commences with a spear-phishing made up of a GZIP archive attachment that consists of a shortcut designed to execute PowerShell code liable for launching a remote HTML application (HTA) utilizing MSHTA.
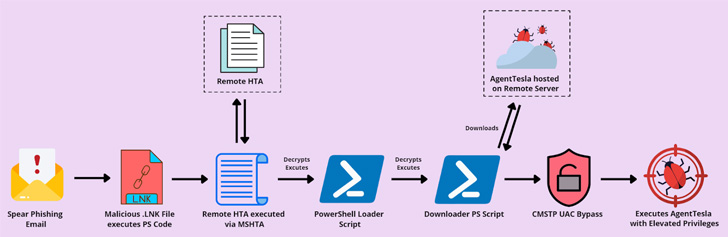
The phishing email messages purport to be an get confirmation message from a Chinese supplier of lump and rock sugar, with the LNK file masquerading as a PDF doc.
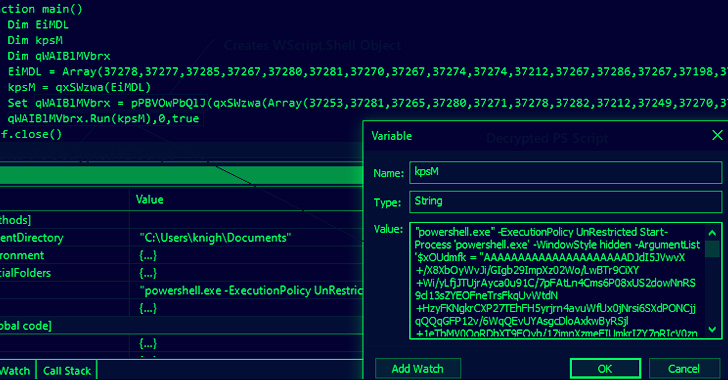
The HTA file, in transform, decrypts and executes a further PowerShell loader script, which acts as a downloader for fetching the Agent Tesla malware and executing it with administrative privileges.
In a 2nd variant of the an infection sequence, the GZIP archive is replaced by a ZIP file, although also adopting further obfuscation techniques to camouflage the destructive exercise.

Quantum Builder has witnessed a surge in use in new months, with risk actors using it to distribute a variety of malware, these types of as RedLine Stealer, IcedID, GuLoader, RemcosRAT, and AsyncRAT.
“Threat actors are consistently evolving their techniques and producing use of malware builders marketed on the cybercrime marketplace,” the researchers said.
“This Agent Tesla marketing campaign is the latest in a string of attacks in which Quantum Builder has been utilized to produce malicious payloads in strategies from numerous corporations.”
Uncovered this short article exciting? Adhere to THN on Fb, Twitter and LinkedIn to go through additional exceptional material we write-up.
Some areas of this write-up are sourced from:
thehackernews.com

 Improve your security posture with Wazuh, a free and open source XDR
Improve your security posture with Wazuh, a free and open source XDR