Two stage-of-sale (PoS) malware variants have been set to use by a threat actor to steal facts linked to more than 167,000 credit score cards from payment terminals.
According to Singapore-headquartered cybersecurity organization Team-IB, the stolen information dumps could net the operators as much as $3.34 million by marketing them on underground forums.
When a substantial proportion of attacks aimed at collecting payment details rely on JavaScript sniffers (aka web skimmers) stealthily inserted on e-commerce internet websites, PoS malware carries on to be an ongoing, if fewer well-liked, danger.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Just past thirty day period, Kaspersky in-depth new strategies adopted by a Brazilian threat actor identified as Prilex to steal dollars by suggests of fraudulent transactions.
“Almost all POS malware strains have a comparable card dump extraction operation, but various methods for maintaining persistence on infected units, information exfiltration and processing,” scientists Nikolay Shelekhov and Reported Khamchiev stated.
Treasure Hunter and its sophisticated successor MajikPOS are alike in that they are built to brute-drive their way into a PoS terminal, or alternatively purchase preliminary accessibility from other parties acknowledged as preliminary obtain brokers, adopted by extracting payment card data from the system’s memory, and forwarding it to a remote server.
It can be worthy of noting that MajikPOS very first came to mild in early 2017, mainly affecting enterprises across the U.S. and Canada. Treasure Hunter (aka TREASUREHUNT), on the other hand, has been chronicled given that 2014, with its resource code struggling a leak in 2018.
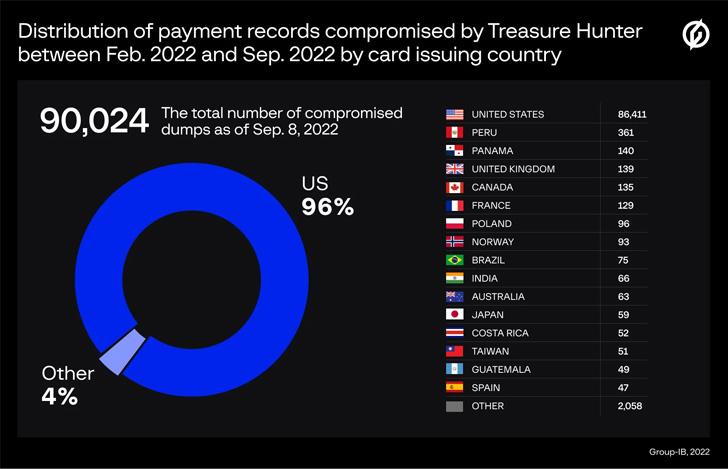
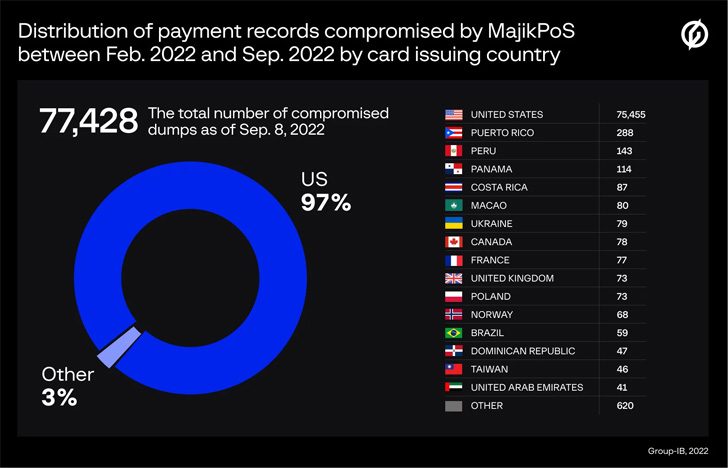
Group-IB, which discovered the command-and-management (C2) servers, associated with the two PoS malware, mentioned 77,428 and 90,024 distinctive payment data have been compromised by MajikPOS and Treasure Hunter concerning February and September 2022.
Most of the stolen cards are reported to have been issued by banking companies in the U.S., Puerto Rico, Peru, Panama, the U.K., Canada, France, Poland, Norway, and Costa Rica.

The identification of the prison actors guiding the scheme is not known, and it can be at this time not obvious if the pilfered data has now been bought for financial gains by the team.
This can have severe effects must the card-issuing banks not implement adequate defense mechanisms, efficiently enabling bad actors to use cloned cards to illicitly withdraw money and make unauthorized transactions.
“PoS malware has come to be a lot less appealing for threat actors in modern many years thanks to some of its constraints and the security measures applied within the card payment sector,” the researchers claimed.
“Yet, […] it continues to be a sizeable risk to the payment business as a complete and to independent companies that have not but carried out the most current security practices. It is as well early to write off PoS malware.”
Discovered this write-up fascinating? Adhere to THN on Facebook, Twitter and LinkedIn to study additional exceptional content we post.
Some areas of this short article are sourced from:
thehackernews.com


 2022 Strategic roadmap for data security platform convergence
2022 Strategic roadmap for data security platform convergence