Information have been shared about a security vulnerability in Dahua’s Open up Network Video Interface Forum (ONVIF) normal implementation, which, when exploited, can lead to seizing handle of IP cameras.
Tracked as CVE-2022-30563 (CVSS score: 7.4), the “vulnerability could be abused by attackers to compromise network cameras by sniffing a preceding unencrypted ONVIF interaction and replaying the qualifications in a new request to the digicam,” Nozomi Networks stated in a Thursday report.
The issue, which was resolved in a patch unveiled on June 28, 2022, impacts the adhering to products and solutions –

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
- Dahua ASI7XXX: Variations prior to v1.000.0000009..R.220620
- Dahua IPC-HDBW2XXX: Variations prior to v2.820.0000000.48.R.220614
- Dahua IPC-HX2XXX: Variations prior to v2.820.0000000.48.R.220614
ONVIF governs the development and use of an open up standard for how IP-based mostly bodily security products these as online video surveillance cameras and access regulate systems can connect with a person one more in a vendor-agnostic fashion.

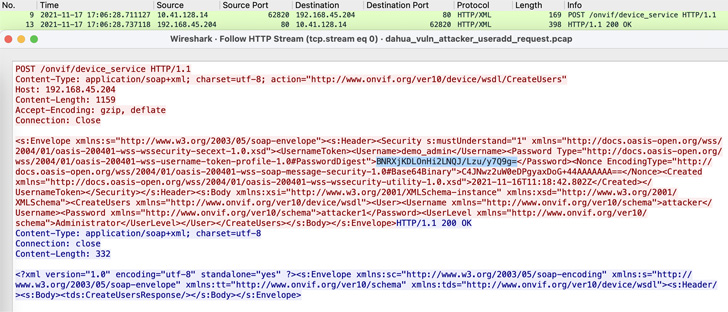
The bug discovered by Nozomi Networks resides in what is identified as the “WS-UsernameToken” authentication system implemented in sure IP cameras developed by Chinese firm Dahua, making it possible for attackers to compromise the cameras by replaying the credentials.
In other text, effective exploitation of the flaw could allow an adversary to covertly add a destructive administrator account and exploit it to acquire unrestricted accessibility to an impacted system with the best privileges, such as viewing reside camera feeds.
All a risk actor requires to mount this attack is to be ready to seize one unencrypted ONVIF ask for authenticated with the WS-UsernameToken schema, which is then made use of to send out a forged ask for with the identical authentication data to trick the system into making the admin account.
This disclosure follows the discovery of identical flaws in Reolink, ThroughTek, Annke, and Axis products, underscoring the prospective hazards posed by IoT security camera techniques provided their deployment in critical infrastructure facilities.
“Risk actors, nation-point out menace groups in distinct, could be interested in hacking IP cameras to help assemble intel on the tools or generation procedures of the target organization,” the scientists explained.
“This information could help in reconnaissance done prior to launching a cyberattack. With additional awareness of the goal setting, risk actors could craft custom made attacks that can physically disrupt output processes in critical infrastructure.”

In a linked improvement, researchers from NCC Team documented 11 vulnerabilities impacting Nuki good lock goods that could be weaponized to get arbitrary code execution and open up doorways or trigger a denial-of-company (DoS) issue.
Also noteworthy is an industrial control method (ICS) advisory issued by the U.S. Cybersecurity and Infrastructure Security Agency this 7 days, warning of two severe security flaws in MOXA NPort 5110 servers managing firmware edition 2.10.
“Successful exploitation of these vulnerabilities could enable an attacker to modify memory values and/or result in the system to turn into unresponsive,” the agency explained.
Discovered this report fascinating? Abide by THN on Fb, Twitter and LinkedIn to read extra distinctive written content we put up.
Some areas of this posting are sourced from:
thehackernews.com


 Researchers Warns of Increase in Phishing Attacks Using Decentralized IPFS Network
Researchers Warns of Increase in Phishing Attacks Using Decentralized IPFS Network