Shutterstock
The normal ransomware payment has risen 71% this 12 months and is shut to achieving $1 million, specialists have explained.
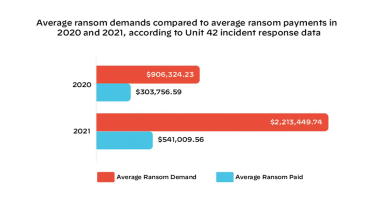
In ransomware cases that have been assisted by incident responders at cyber security enterprise Unit 42 of Palo Alto Networks, the normal ransom paid was $925,162 in the initial 5 months of 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This signifies a steep and “startling” increase from figures of prior yrs when regular ransom payments were $541,009 and $303,756 in 2021 and 2020 respectively, explained Ryan Olson, vice president of menace intelligence at Device 42 in a website post.
As a short while ago as 2016, the company’s incident responders were looking at payments of just $500, and the increase of double extortion styles has put extra stress on organisations to pay ransom demands.
Device 42
Double extortion ransomware has grow to be a popular operational design in new years as firms are significantly vigilant to ransomware attacks and are holding greater backups to steer clear of acquiring to shell out ransom needs.
The product sees attackers infecting a company network with ransomware, locking people out of equipment as typical, but exfiltrates sensitive info in advance of the an infection chain starts, threatening to leak the details if the ransom isn’t paid.
This areas extra pressure on businesses to retain their track record with customers and from a regulatory standpoint for companies certain by stringent knowledge safety regulations like GDPR.
“Details of about 7 new victims on regular are posted each and every working day on the dark web leak internet sites that ransomware gangs use to coerce victims into spending ransoms,” explained Olson. “The amount of double extortion we have observed interprets into a single new victim every single 3 to four hours.
“The cyber extortion disaster carries on since cybercriminals have been relentless in their introduction of progressively subtle attack applications, extortion methods and marketing and advertising campaigns that have fueled this unparalleled, world digital crime spree,” he additional. “Their ransomware-as-a-services (RaaS) business product has at the similar time reduced the specialized bar for entry by building these strong tools available to wannabe cyber extortionists with easy-to-use interfaces and on the web aid.”
Device 42 has noticed two cases of multi-million-greenback ransoms being compensated this calendar year, pushed by the achievements of the Quantum Locker and LockBit 2. ransomware operations.
Firms that could be place out of enterprise if they do not fork out the ransom will keep on to be specific, the researcher stated, and it is in these situations wherever the massive ransom demands will again be issued.
Olson cited Costa Rica as an instance of how devastating ransomware can nevertheless be in 2022, five years on from WannaCry and six several years after the normal ransom desire was in the location of $500 – a pittance in today’s danger landscape.
The region has declared a condition of crisis soon after it sustained an attack from the Conti ransomware and has given that experienced a next ransomware gang targeting the country, this time concentrating on its overall health service.
In accordance to a independent report from Digital Shadows, the to start with quarter of 2022 noticed a 25% lower in ransomware exercise when compared to the previous quarter.
The firm reported the lessen in activity could be a end result of a less popular threat of the larger sized, far more organised ransomware groups that have shuttered in modern months, these types of as REvil and BlackMatter.
Some areas of this report are sourced from:
www.itpro.co.uk


 Black Basta Ransomware Teams Up with Malware Stalwart Qbot
Black Basta Ransomware Teams Up with Malware Stalwart Qbot