The infamous Emotet botnet has been connected to a new wave of malspam strategies that choose gain of password-shielded archive files to fall CoinMiner and Quasar RAT on compromised techniques.
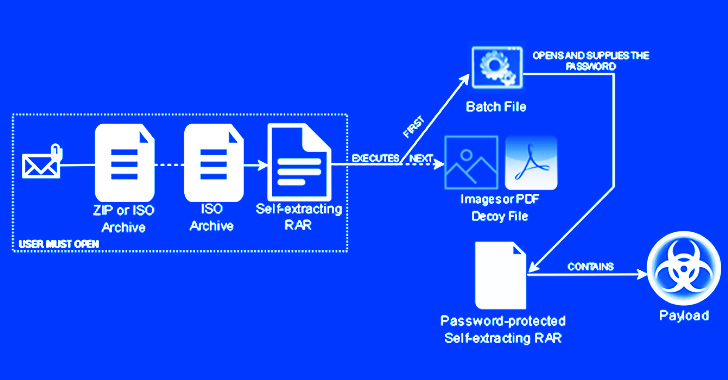
In an attack chain detected by Trustwave SpiderLabs scientists, an invoice-themed ZIP file lure was located to comprise a nested self-extracting (SFX) archive, the initial archive performing as a conduit to start the next.
Whilst phishing attacks like these usually demand persuading the target into opening the attachment, the cybersecurity company said the campaign sidesteps this hurdle by building use of a batch file to immediately source the password to unlock the payload.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The initially SFX archive file even more helps make use of both a PDF or Excel icon to make it surface legit, when, in actuality, it has three parts: the password-secured next SFX RAR file, the aforementioned batch script which launches the archive, and a decoy PDF or graphic.
“The execution of the batch file leads to the installation of the malware lurking within the password-protected RARsfx [self-extracting RAR archive],” researchers Bernard Bautista and Diana Lopera mentioned in a Thursday create-up.
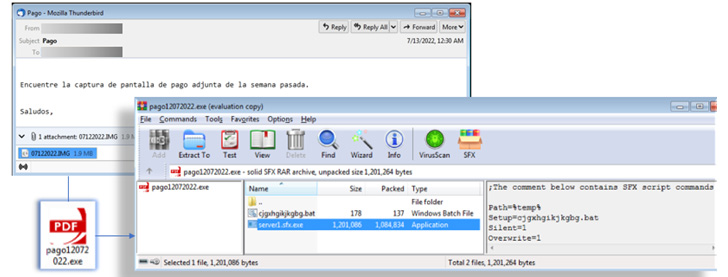
The batch script achieves this by specifying the archive’s password and the location folder to which the payload will be extracted, in addition to launching a command to exhibit the entice document in an attempt to conceal the destructive activity.
Last of all, the an infection culminates in the execution of CoinMiner, a cryptocurrency miner that can also double up as a credential stealer, or Quasar RAT, an open up resource .NET-based mostly distant accessibility trojan, based on the payload packed in the archive.

The a person-simply click attack strategy is also noteworthy in that it properly jumps earlier the password hurdle, enabling destructive actors to carry out a large assortment of steps this sort of as cryptojacking, details exfiltration, and ransomware.
Trustwave mentioned it has determined an raise in threats packaged in password-safeguarded ZIP files, with about 96% of these becoming distributed by the Emotet botnet.
“The self-extracting archive has been all-around for a lengthy time and eases file distribution among conclude customers,” the scientists reported. “Nevertheless, it poses a security risk considering the fact that the file contents are not quickly verifiable, and it can operate instructions and executables silently.”
Identified this post fascinating? Stick to THN on Fb, Twitter and LinkedIn to examine more special content material we put up.
Some components of this write-up are sourced from:
thehackernews.com

 Google Unveils Open Source Project to Improve Software Supply Chain Security
Google Unveils Open Source Project to Improve Software Supply Chain Security