Suspected Russian menace actors have been concentrating on Jap European buyers in the crypto field with faux task prospects as bait to install info-stealing malware on compromised hosts.
The attackers “use various hugely obfuscated and beneath-progress custom made loaders in buy to infect those associated in the cryptocurrency business with Enigma stealer,” Development Micro scientists Aliakbar Zahravi and Peter Girnus claimed in a report this week.
Enigma is reported to be an altered model of Stealerium, an open up source C#-dependent malware that functions as a stealer, clipper, and keylogger.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
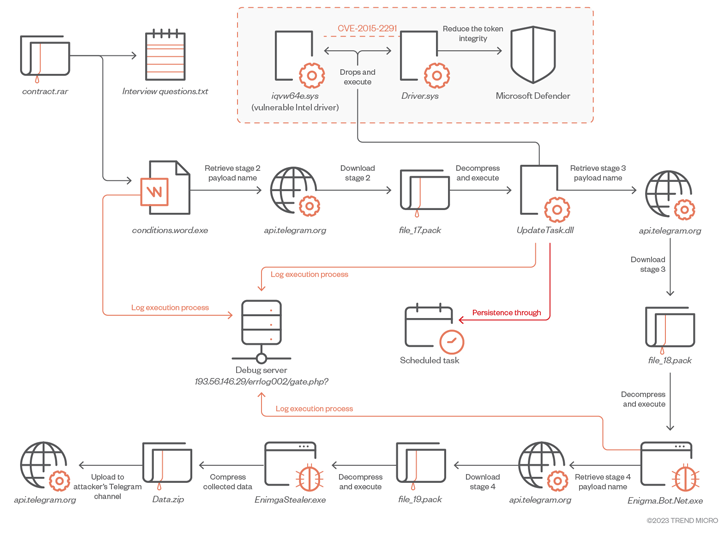
The intricate infection journey commences with a rogue RAR archive file which is distributed by using phishing or social media platforms. It is made up of two documents, a person of which is a .TXT file that includes a established of sample job interview thoughts associated to cryptocurrency.
The second file is a Microsoft Term doc that, though serving as a decoy, is tasked with launching the to start with-stage Enigma loader, which, in transform, downloads and executes an obfuscated secondary-stage payload as a result of Telegram.
“To obtain the up coming stage payload, the malware initial sends a ask for to the attacker-managed Telegram channel […] to get hold of the file route,” the researchers reported. “This tactic will allow the attacker to continuously update and removes reliance on preset file names.”
The 2nd-phase downloader, which is executed with elevated privileges, is created to disable Microsoft Defender and put in a third-phase by deploying a legitimately signed kernel manner Intel driver which is vulnerable to CVE-2015-2291 in a approach identified as Carry Your Have Vulnerable Driver (BYOVD).
It really is worth noting that the U.S. Cybersecurity and Infrastructure Security Company (CISA) included the vulnerability to its Identified Exploited Vulnerabilities (KEV) catalog, citing evidence of energetic exploitation in the wild.
The third-phase payload in the end paves the way for downloading Enigma Stealer from an actor-managed Telegram channel. The malware, like other stealers, will come with characteristics to harvest sensitive info, document keystrokes, and capture screenshots, all of which is exfiltrated back by implies of Telegram.
Bogus work presents are a attempted-and-analyzed tactic utilized by North Korea-backed Lazarus Group in its attacks concentrating on the crypto sector. The adoption of this modus operandi by Russian danger actors “demonstrates a persistent and lucrative attack vector.”
The conclusions appear as Uptycs produced facts of an attack marketing campaign that leverages the Stealerium malware to siphon personal information, including qualifications for cryptocurrency wallets these kinds of as Armory, Atomic Wallet, Coinomi, Electrum, Exodus, Guarda, Jaxx Liberty, and Zcash, amongst other individuals.
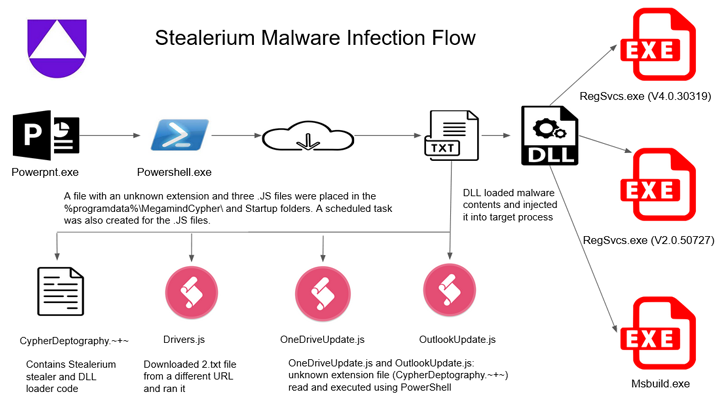
Signing up for Enigma Stealer and Stealerium in concentrating on cryptocurrency wallets is but a further malware dubbed Vector Stealer that also arrives with capabilities to steal .RDP documents, enabling the threat actors to carry out RDP hijacking for remote obtain, Cyble mentioned in a specialized generate-up.
Attack chains documented by the cybersecurity firms present that the malware family members are delivered by Microsoft Office attachments containing malicious macros, suggesting that miscreants are nonetheless relying on the method regardless of Microsoft’s makes an attempt to close the loophole.
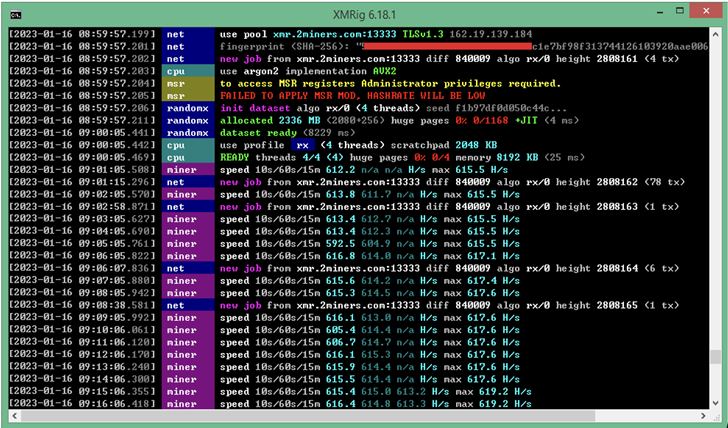
A identical technique has also been put to use to deploy a Monero crypto miner versus the backdrop of a cryptojacking and phishing campaign aimed at Spanish buyers, according to Fortinet FortiGuard Labs.
The growth is also the latest in a prolonged listing of attacks that are aimed at thieving victims’ cryptocurrency assets across platforms.
This includes a “quickly evolving” Android banking trojan referred to as TgToxic, which plunders credentials and money from crypto wallets as effectively as lender and finance apps. The ongoing malware marketing campaign, energetic given that July 2022, is directed from cell consumers in Taiwan, Thailand, and Indonesia.
“When the target downloads the phony app from the web page provided by the threat actor, or if sufferer attempts to mail a direct message to the menace actor by way of messaging applications these types of as WhatsApp or Viber, the cybercriminal deceives the consumer into registering, putting in the malware, and enabling the permissions it requirements,” Craze Micro explained.
The rogue apps, besides abusing Android’s accessibility providers to carry out the unauthorized fund transfers, is also notable for abusing legitimate automation frameworks like Easyclick and Car.js to carry out clicks and gestures, producing it the second Android malware just after PixPirate to include such workflow IDEs.
But social engineering strategies have also absent beyond social media phishing and smishing by placing up convincing landing webpages that imitate well known crypto products and services with the purpose of transferring Ethereum and NFTs from the hacked wallets.
This, in accordance to Recorded Upcoming, is realized by injecting a crypto drainer script into the phishing page which lures victims into connecting their wallets with valuable provides to mint non-fungible tokens (NFTs).
Such completely ready-produced phishing web pages are staying offered on darknet community forums as aspect of what is actually referred to as a phishing-as-a-assistance (PhaaS), permitting other actors to lease out these packages and swiftly enact malicious operations at scale.
“‘Crypto drainers’ are malicious scripts that purpose like e-skimmers and are deployed with phishing tactics to steal victims’ crypto assets,” the organization explained in a report published final week, describing the frauds as successful and rising in reputation.
“The use of legit companies on crypto drainer phishing web pages may perhaps enhance the probability that the phishing web site will go an in any other case savvy user’s ‘scam litmus exam.’ When crypto wallets have been compromised, no safeguards exist to protect against the illicit transfer of assets to attackers’ wallets.”
The assaults occur at a time when legal teams have stolen a record-breaking $3.8 billion from crypto companies in 2022, with significantly of the spike attributed to North Korean state-sponsored hacking crews.
Uncovered this write-up appealing? Comply with us on Twitter and LinkedIn to examine extra exclusive material we submit.
Some parts of this report are sourced from:
thehackernews.com


 CISA Warns of Active Attacks Exploiting Fortra MFT, TerraMaster NAS, and Intel Driver Flaws
CISA Warns of Active Attacks Exploiting Fortra MFT, TerraMaster NAS, and Intel Driver Flaws