Apple lately mounted a security vulnerability in the macOS operating program that could be most likely exploited by a menace actor to “trivially and reliably” bypass a “myriad of foundational macOS security mechanisms” and run arbitrary code.
Security researcher Patrick Wardle specific the discovery in a series of tweets on Thursday. Tracked as CVE-2021-30853 (CVSS score: 5.5), the issue relates to a situation exactly where a rogue macOS app may well circumvent Gatekeeper checks, which be certain that only dependable applications can be operate and that they have handed an automated process termed “app notarization.”
The iPhone maker, crediting Gordon Very long of Box with reporting the flaw, said it addressed the weak spot with enhanced checks as component of macOS 11.6 updates officially produced on September 20, 2021.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“This kind of bugs are frequently specifically impactful to day to day macOS customers as they supply a implies for adware and malware authors to sidestep macOS security mechanisms, …mechanisms that normally would thwart an infection attempts,” Wardle explained in a complex write-up of the flaw.
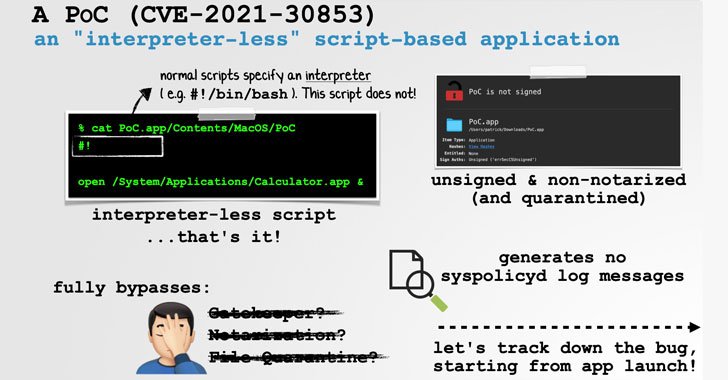
Precisely, the bug not only receives all over Gatekeeper, but also File Quarantine and macOS’s notarization necessities, correctly enabling a seemingly innocuous PDF file to compromise the complete process basically by opening it. In accordance to Wardle, the issue is rooted in the actuality that an unsigned, non-notarized script-primarily based software can not explicitly specify an interpreter, resulting in a comprehensive bypass.
It is really worth noting that a shebang interpreter directive — e.g. #!/bin/sh or #!/bin/bash — is typically utilised to parse and interpret a shell plan. But in this edge-scenario attack, an adversary can craft an software these types of that the shebang line is integrated with no supplying an interpreter (i.e., #!) and nonetheless get the underlying running program to launch the script without elevating any notify.
This is so because “macOS will (re)attempt to execute the failed [‘interpreter-less’ script-based app] through the shell (‘/bin/sh’)” soon after the preliminary lack of good results, Wardle discussed.
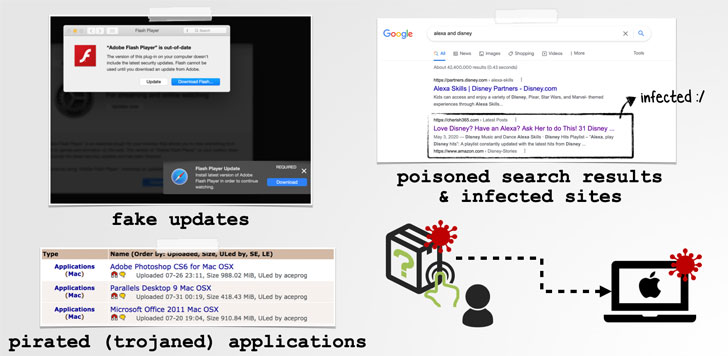
In other text, menace actors can exploit this flaw by tricking their targets into opening a rogue app that can be camouflaged as Adobe Flash Player updates or trojanized variations of authentic apps like Microsoft Business office, which, in switch, can be sent through a technique referred to as look for poisoning the place attackers artificially maximize the lookup motor rating of internet websites hosting their malware to lure probable victims.
This is not the 1st time flaws have been identified in the Gatekeeper process. Previously this April, Apple moved to swiftly patch a then actively exploited zero-working day flaw (CVE-2021-30657) that could circumvent all security protections, thus permitting unapproved program to be operate on Macs.
Then in Oct, Microsoft disclosed a vulnerability dubbed “Shrootless” (CVE-2021-30892), which could be leveraged to accomplish arbitrary functions, elevate privileges to root, and install rootkits on compromised equipment. Apple stated it remediated the problem with additional restrictions as portion of security updates pushed on Oct 26, 2021.
Found this short article exciting? Adhere to THN on Fb, Twitter and LinkedIn to read through more exclusive written content we post.
Some parts of this report are sourced from:
thehackernews.com


 Former Uber CSO Faces New Charge for 2016 Breach
Former Uber CSO Faces New Charge for 2016 Breach