Additional details have emerged about a security feature bypass vulnerability in Windows NT LAN Manager (NTLM) that was dealt with by Microsoft as section of its regular Patch Tuesday updates earlier this thirty day period.
The flaw, tracked as CVE-2021-1678 (CVSS score 4.3), was described as a “remotely exploitable” flaw identified in a vulnerable part certain to the network stack, despite the fact that specific aspects of the flaw remained unfamiliar.
Now in accordance to researchers from Crowdstrike, the security bug, if still left unpatched, could let a poor actor to realize remote code execution by way of an NTLM relay.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

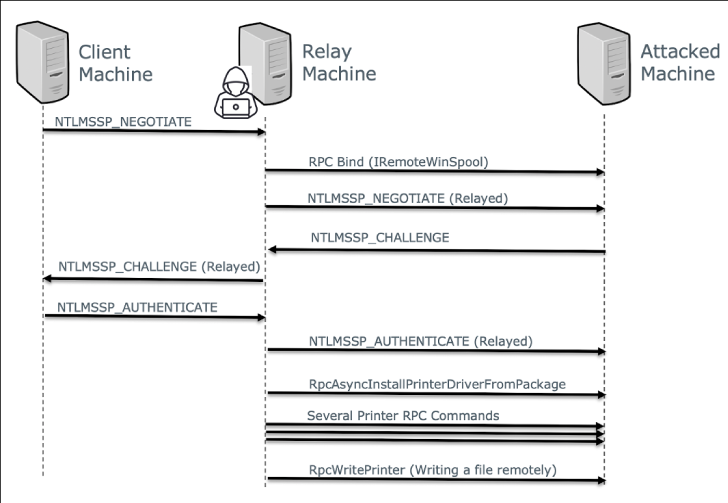
“This vulnerability permits an attacker to relay NTLM authentication sessions to an attacked machine, and use a printer spooler MSRPC interface to remotely execute code on the attacked device,” the researchers reported in a Friday advisory.
NTLM relay attacks are a type of person-in-the-center (MitM) attacks that ordinarily allow attackers with accessibility to a network to intercept reputable authentication visitors among a customer and a server and relay these validated authentication requests in purchase to access network companies.
Productive exploits could also allow for an adversary to remotely run code on a Windows equipment or shift laterally on the network to critical units such as servers hosting domain controllers by reusing the NTLM credentials directed at the compromised server.
Whilst this sort of attacks can be thwarted by SMB and LDAP signing and turning on Increased Defense for Authentication (EPA), CVE-2021-1678 exploits a weak spot in MSRPC (Microsoft Remote Method Get in touch with) that makes it vulnerable to a relay attack.
Exclusively, the scientists discovered that IRemoteWinspool — an RPC interface for distant printer spooler administration — could be leveraged to execute a series of RPC operations and publish arbitrary data files on a target machine applying an intercepted NTLM session.
Microsoft, in a aid doc, mentioned it addressed the vulnerability by “rising the RPC authentication stage and introducing a new policy and registry key to enable shoppers to disable or help Enforcement mode on the server-aspect to improve the authentication level.”
In addition to putting in the January 12 Windows update, the firm has urged organizations to turn on Enforcement mode on the print server, a placing which it says will be enabled on all Windows gadgets by default starting up June 8, 2021.
Discovered this posting interesting? Stick to THN on Fb, Twitter and LinkedIn to browse additional exceptional content material we article.
Some parts of this post are sourced from:
thehackernews.com


 Beware! Fully-Functional Released Online for SAP Solution Manager Flaw
Beware! Fully-Functional Released Online for SAP Solution Manager Flaw