Cybersecurity scientists have shed a lot more gentle on a destructive loader that operates as a server and executes received modules in memory, laying bare the framework of an “innovative multi-layered digital equipment” made use of by the malware to fly less than the radar.
Wslink, as the destructive loader is known as, was initially documented by Slovak cybersecurity business ESET in Oct 2021, with incredibly couple of telemetry hits detected in the past two decades spanning Central Europe, North The usa, and the Center East.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Investigation of the malware samples have yielded tiny to no clues about the initial compromise vector used and no code, features or operational similarities have been uncovered to advise that this is a software from a earlier recognized menace actor.
Packed with a file compression utility named NsPack, Wslink tends to make use of what’s known as a approach digital machine (VM), a mechanism to operate an application in a system-independent way that abstracts the fundamental components or running procedure, as an obfuscation strategy but with a very important distinction.
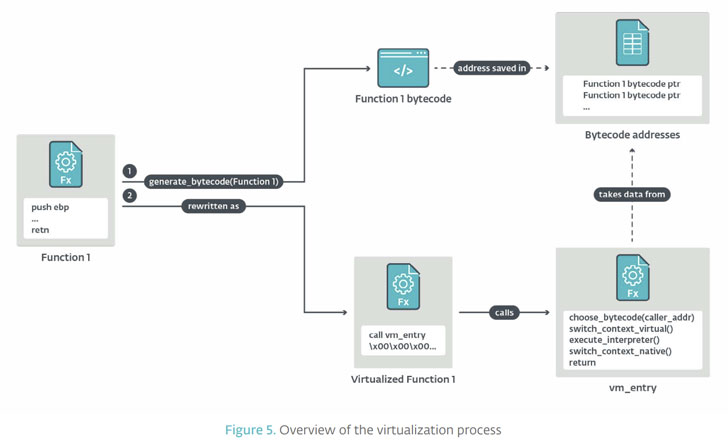
“Digital devices made use of as obfuscation engines […] are not intended to run cross-platform apps and they typically just take device code compiled or assembled for a identified ISA [instruction set architecture], disassemble it, and translate that to their personal digital ISA,” ESET malware analyst Vladislav Hrčka said.
“The strength of this obfuscation strategy resides in the truth that the ISA of the VM is unfamiliar to any future reverse engineer – a comprehensive analysis of the VM, which can be pretty time-consuming, is essential to fully grasp the meaning of the virtual recommendations and other structures of the VM.”
What is more, the virtualized Wslink malware deal will come with a various arsenal of tactics to hamper reverse engineering, which includes junk code, encoding of digital operands, merging of digital recommendations, and the use of a nested virtual device.
“Obfuscation techniques are a form of application safety intended to make code difficult to understand and that’s why conceal its objectives obfuscating digital device methods have turn into widely misused for illicit needs this kind of as obfuscation of malware samples, due to the fact they hinder both of those investigation and detection,” Hrčka stated.
Located this post interesting? Adhere to THN on Facebook, Twitter and LinkedIn to examine a lot more distinctive information we post.
Some pieces of this report are sourced from:
thehackernews.com



 A Large-Scale Supply Chain Attack Distributed Over 800 Malicious NPM Packages
A Large-Scale Supply Chain Attack Distributed Over 800 Malicious NPM Packages