Security researchers are warning of “a trove of delicate data” leaking by urlscan.io, a internet site scanner for suspicious and malicious URLs.
“Sensitive URLs to shared files, password reset internet pages, staff invitations, payment invoices and extra are publicly detailed and searchable,” Favourable Security co-founder, Fabian Bräunlein, explained in a report posted on November 2, 2022.
The Berlin-based cybersecurity firm explained it begun an investigation in the aftermath of a notification despatched by GitHub in February 2022 to an unidentified variety of end users about sharing their usernames and personal repository names (i.e., GitHub Web pages URLs) to urlscan.io for metadata investigation as aspect of an automatic approach.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
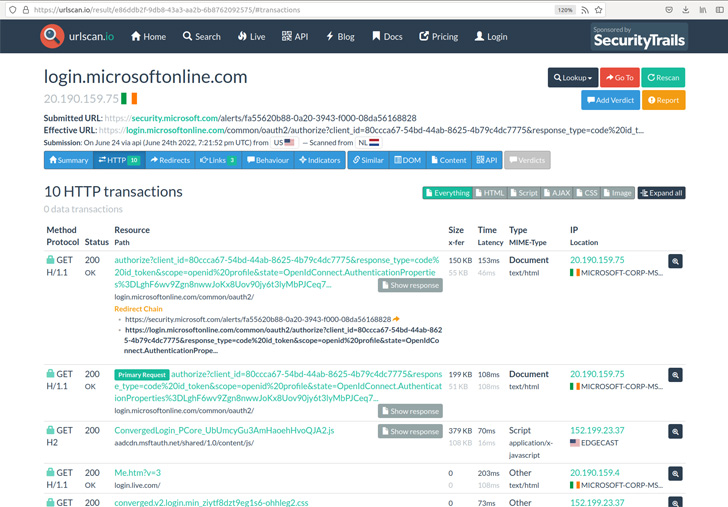
Urlscan.io, which has been described as a sandbox for the web, is integrated into several security answers by way of its API.
“With the form of integration of this API (for instance by means of a security resource that scans just about every incoming email and performs a urlscan on all inbound links), and the total of facts in the databases, there is a extensive variety of sensitive info that can be searched for and retrieved by an nameless consumer,” Bräunlein pointed out.
This incorporated password reset one-way links, email unsubscribe links, account creation URLs, API keys, details about Telegram bots, DocuSign signing requests, shared Google Push one-way links, Dropbox file transfers, invite one-way links to services like SharePoint, Discord, Zoom, PayPal invoices, Cisco Webex meeting recordings, and even URLs for bundle tracking.
Bräunlein pointed out that an original research in February unveiled “juicy URLs” belonging to Apple domains, some of which also consisted of publicly-shared inbound links to iCloud files and calendar invite responses, and have considering that been taken out.
Apple is reported to have requested an exclusion of its domains from the URL scans such that results matching selected predefined principles are periodically deleted.
Favourable Security more extra that it reached out to a quantity of individuals leaked email addresses, receiving one response from an unnamed organization that traced the leak of a DocuSign function agreement backlink to a misconfiguration of its Security Orchestration, Automation, and Reaction (SOAR) remedy, which was currently being integrated with urlscan.io.
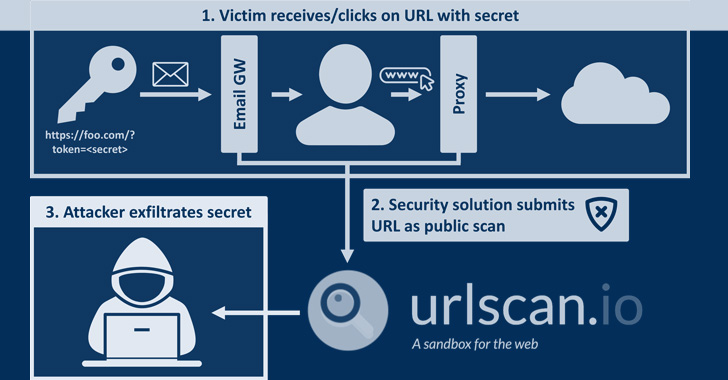
On top rated of that, the examination has also found that misconfigured security tools are submitting any url gained by using mail as a public scan to urlscan.io.

This could have serious consequences whereby a malicious actor can result in password reset back links for the affected email addresses and exploit the scan benefits to seize the URLs and get in excess of the accounts by resetting to a password of the attacker’s alternative.
To maximize the efficiency of such an attack, the adversary can lookup information breach notification internet sites like Have I Been Pwned to ascertain the exact expert services that were registered using the email addresses in query.

Urlscan.io, next dependable disclosure from Beneficial Security in July 2022, has urged users to “recognize the various scan visibilities, overview your have scans for non-community info, assessment your automated submission workflows, [and] implement a maximum scan visibility for your account.”
It has also added deletion regulations to routinely purge delete previous and foreseeable future scans matching the search patterns, stating it has area and URL pattern blocklists in location to protect against scanning of distinct web-sites.
“This information could be applied by spammers to acquire email addresses and other personal details,” Bräunlein stated. “It could be applied by cyber criminals to take about accounts and run plausible phishing strategies.”
Located this posting appealing? Abide by THN on Facebook, Twitter and LinkedIn to read far more exclusive articles we put up.
Some components of this short article are sourced from:
thehackernews.com

 ICO: Department for Education Should Have Been Fined £10m
ICO: Department for Education Should Have Been Fined £10m