Cybersecurity researchers on Tuesday disclosed “distinctive” methods, tactics, and procedures (TTPs) adopted by operators of Hades ransomware that established it aside from the relaxation of the pack, attributing it to a financially determined danger team called GOLD Winter.
“In numerous methods, the GOLD Wintertime risk group is a typical submit-intrusion ransomware threat team that pursues significant-value targets to increase how substantially money it can extort from its victims,” scientists from SecureWorks Counter Danger Unit (CTU) said in an assessment shared with The Hacker News. “Nonetheless, GOLD WINTER’s functions have quirks that distinguish it from other teams.”
The conclusions appear from a research of incident response efforts the Atlanta-based cybersecurity business engaged in the initial quarter of 2021.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Because first rising in the threat landscape in December 2020, Hades has been classified as INDRIK SPIDER’s successor to WastedLocker ransomware with “supplemental code obfuscation and slight attribute alterations,” per Crowdstrike. INDRIK SPIDER, also recognized as GOLD DRAKE and Evil Corp, is a refined eCrime team infamous for running a banking trojan identified as Dridex as properly as distributing BitPaymer ransomware amongst 2017 and 2020.
The WastedLocker-derived ransomware strain has been discovered to have impacted at minimum three victims as of late March 2021, according to investigation by Accenture’s Cyber Investigation and Forensic Response (CIFR) and Cyber Threat Intelligence (ACTI) groups, including a U.S. transportation and logistics firm, a U.S. client items firm, and a world wide manufacturing corporation. Trucking big Forward Air was disclosed to be a target back again in December 2020.
Then a subsequent evaluation printed by Awake Security raised the chance that an sophisticated threat actor could be functioning below the guise of Hades, citing a Hafnium area that was determined as an indicator of compromise inside of the timeline of the Hades attack. Hafnium is the title assigned by Microsoft to a Chinese nation-point out actor that the corporation has said is at the rear of the ProxyLogon attacks on vulnerable Exchange Servers previously this 12 months.
Stating that the risk team works by using TTPs not linked with other ransomware operators, Secureworks mentioned the absence of Hades from underground boards and marketplaces could suggest that Hades is operated as personal ransomware instead than ransomware-as-a-services (RaaS).
GOLD Winter targets digital non-public networks and remote desktop protocols to acquire an original foothold and sustain obtain to sufferer environments, working with it to realize persistence by way of applications these as Cobalt Strike. In one particular occasion, the adversary disguised the Cobalt Strike executable as a CorelDRAW graphics editor software to mask the genuine nature of the file, the scientists stated.

In a next situation, Hades was located to leverage SocGholish malware — generally affiliated with the GOLD DRAKE team — as an original obtain vector. SocGholish refers to a push-by attack in which a user is tricked into browsing an contaminated web page employing social engineering themes that impersonate browser updates to bring about a destructive down load with no person intervention.
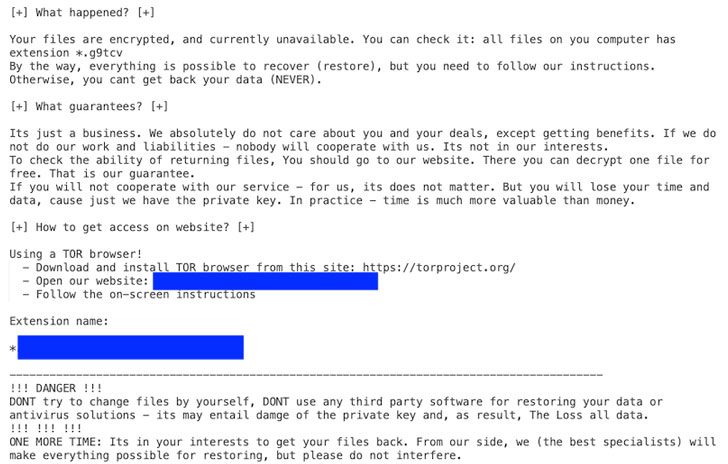
Apparently, in what seems to be an attempt to mislead attribution or “shell out homage to admired ransomware people,” Hades has exhibited a pattern of duplicating ransom notes from other rival teams like REvil and Conti.
An additional novel method consists of the use of Tox immediate messaging assistance for communications, not to mention the use of Tor-dependent internet sites tailor-made to each sufferer as opposed to utilizing a centralized leak web page to expose knowledge stolen from its victims. “Every single web page incorporates a target-particular Tox chat ID for communications,” the scientists stated.
“Ransomware groups are normally opportunistic: they goal any corporation that could be inclined to extortion and will possible pay the ransom,” the scientists famous. “However, GOLD WINTER’s attacks on big North The us-dependent producers indicates that the team is a ‘big game hunter’ that specially seeks large-worth targets.”
Discovered this report attention-grabbing? Adhere to THN on Facebook, Twitter and LinkedIn to read through much more exclusive material we write-up.
Some components of this write-up are sourced from:
thehackernews.com


 Apple Hurries Patches for Safari Bugs Under Active Attack
Apple Hurries Patches for Safari Bugs Under Active Attack