The China-centered menace actor recognized as Mustang Panda has been observed refining and retooling its strategies and malware to strike entities located in Asia, the European Union, Russia, and the U.S.
“Mustang Panda is a really enthusiastic APT group relying primarily on the use of topical lures and social engineering to trick victims into infecting them selves,” Cisco Talos reported in a new report detailing the group’s evolving modus operandi.
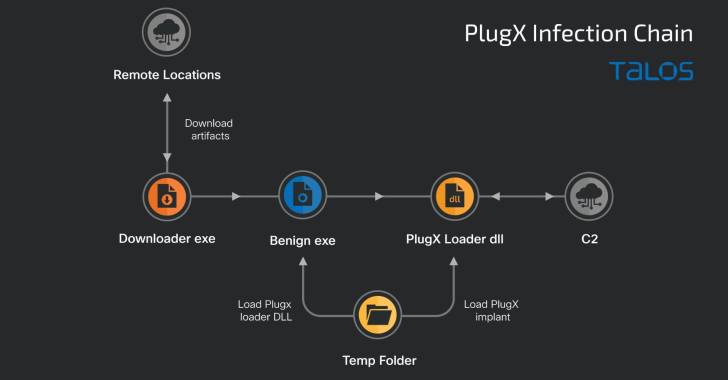
The group is regarded to have focused a huge selection of corporations because at minimum 2012, with the actor largely relying on email-dependent social engineering to gain first access to fall PlugX, a backdoor predominantly deployed for extended-phrase entry.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Phishing messages attributed to the campaign contain destructive lures masquerading as official European Union reviews on the ongoing conflict in Ukraine or Ukrainian authorities experiences, both equally of which download malware onto compromised equipment.
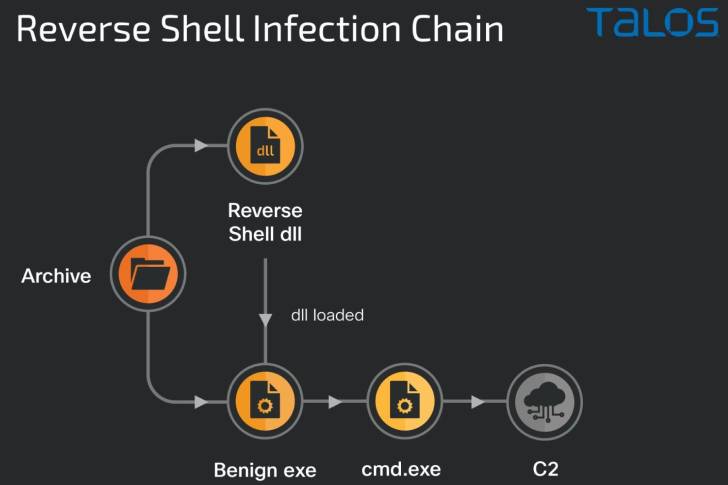
Also noticed are phishing messages tailor-made to concentrate on several entities in the U.S. and many Asian international locations like Myanmar, Hong Kong, Japan, and Taiwan.
The conclusions observe a current report from Secureworks that the team may well have been targeting Russian government officers applying a decoy containing PlugX that disguised itself as a report on the border detachment to Blagoveshchensk.
But related attacks detected toward the close of March 2022 clearly show that the actors are updating their strategies by decreasing the distant URLs made use of to acquire diverse factors of the an infection chain.
Other than PlugX, an infection chains utilized by the APT group have associated the deployment of tailor made stagers, reverse shells, Meterpreter-based mostly shellcode, and Cobalt Strike, all of which are applied to set up distant access to their targets with the intention of conducting espionage and facts theft.
“By employing summit- and meeting-themed lures in Asia and Europe, this attacker aims to achieve as much extended-time period accessibility as possible to conduct espionage and information and facts theft,” Talos researchers reported.
Identified this write-up interesting? Observe THN on Facebook, Twitter and LinkedIn to read extra exclusive written content we write-up.
Some sections of this write-up are sourced from:
thehackernews.com

 Google Releases Android Update to Patch Actively Exploited Vulnerability
Google Releases Android Update to Patch Actively Exploited Vulnerability