Cybersecurity scientists have found out the serious-environment id of the menace actor guiding Golden Chickens malware-as-a-company, who goes by the on the net persona “badbullzvenom.”
eSentire’s Threat Reaction Unit (TRU), in an exhaustive report printed pursuing a 16-month-lengthy investigation, reported it “discovered numerous mentions of the badbullzvenom account being shared in between two persons.”
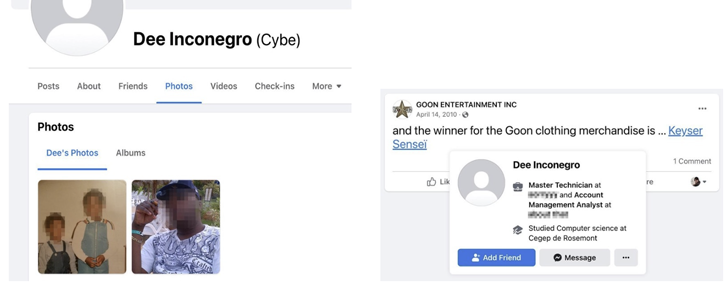
The next risk actor, regarded as Frapstar, is said to discover on their own as “Chuck from Montreal,” enabling the cybersecurity organization to piece collectively the legal actor’s electronic footprint.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This features his actual identify, photographs, house deal with, the names of his dad and mom, siblings, and mates, along with his social media accounts and his passions. He is also reported to be the sole proprietor of a tiny small business that’s run from his own house.
Golden Chickens, also recognized as Venom Spider, is a malware-as-a-assistance (MaaS) company that’s joined to a range of tools these as Taurus Builder, software to produce destructive paperwork and Additional_eggs, a JavaScript downloader that is employed to provide further payloads.
The menace actor’s cyber arsenal has been set to use by other well known cybercriminal teams like Cobalt Group (aka Cobalt Gang), Evilnum, and FIN6, all of which are estimated to have collectively caused losses totaling $1.5 billion.
Earlier More_eggs strategies, some courting back to 2017, have involved spear-phishing small business industry experts on LinkedIn with bogus job features that give menace actors distant regulate about the victim’s machine, leveraging it to harvest details or deploy extra malware.
Previous 12 months, in a reversal of kinds, the identical techniques had been used to strike corporate using the services of supervisors with resumes laden with malware as an infection vector.
The earliest documented document of Frapster’s activity goes again to May possibly 2015, when Development Micro described the personal as a “lone legal” and a luxury vehicle enthusiast.
“‘Chuck,’ who employs many aliases for his underground forum, social media, and Jabber accounts, and the menace actor professing to be from Moldova, have gone to terrific lengths to disguise on their own,” eSentire scientists Joe Stewart and Keegan Keplinger reported.
“They have also taken good pains to obfuscate the Golden Chickens malware, attempting to make it undetectable by most AV companies, and restricting shoppers to making use of Golden Chickens for ONLY focused attacks.”
It is really suspected that Chuck is one particular of the two risk actors functioning the badbullzvenom account on the Exploit.in underground discussion board, with the other party probably found in Moldova or Romania, eSentire mentioned.
The Canadian cybersecurity firm said it further uncovered a new attack marketing campaign targeting e-commerce corporations, tricking recruiters into downloading a rogue Windows shortcut file from a web-site that masquerades as a resume.
The shortcut, a malware dubbed VenomLNK, serves as an initial access vector to drop Far more_eggs or TerraLoader, which subsequently functions as a conduit to deploy various modules, particularly TerraRecon (for sufferer profiling), TerraStealer (for information and facts theft), and TerraCrypt (for ransomware extortion).
“The malware suite is continue to actively currently being produced and is remaining and marketed to other danger actors,” the scientists concluded, urging corporations to be on the lookout for probable phishing attempts.
Located this posting interesting? Comply with us on Twitter and LinkedIn to browse a lot more unique information we post.
Some areas of this short article are sourced from:
thehackernews.com


 The IT Pro Podcast: The problem with APIs
The IT Pro Podcast: The problem with APIs