An ongoing cyber-espionage procedure with suspected ties to China has been located focusing on a Southeast Asian governing administration to deploy spy ware on Windows units though being beneath the radar for extra than 3 years.
“In this marketing campaign, the attackers used the set of Microsoft Workplace exploits and loaders with anti-assessment and anti-debugging procedures to set up a beforehand unfamiliar backdoor on victim’s machines,” researchers from Check out Stage Investigation reported in a report released right now.
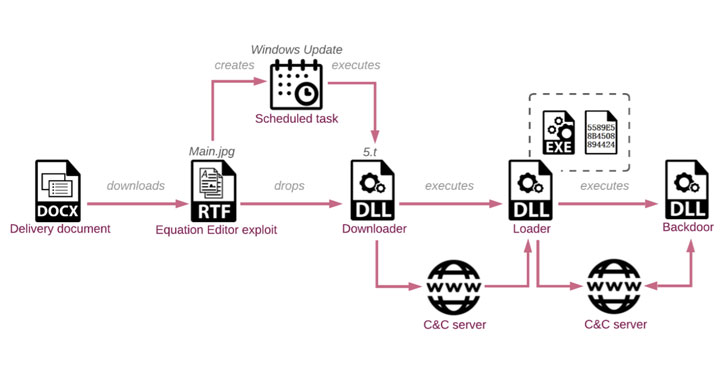
The an infection chain works by sending decoy files, impersonating other entities inside the government, to multiple users of the Ministry of Overseas Affairs, which, when opened, retrieves a following-phase payload from the attacker’s server that has an encrypted downloader. The downloader, in change, gathers and exfiltrates method details to a remote server that subsequently responds back again with a shellcode loader.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The use of weaponized copies of legitimate-wanting official paperwork also suggests that “the attackers initial experienced to attack a different office within the focused point out, thieving and weaponizing documents for use from the Ministry of International Affairs,” claimed Lotem Finkelsteen, head of risk intelligence at Examine Level.
The very last website link in the attack involves the loader developing a relationship with the remote server to obtain, decrypt, and execute an implant dubbed “VictoryDll_x86.dll” that is capable of carrying out file functions, seize screenshots, make and terminate processes, and even shut down the contaminated equipment.
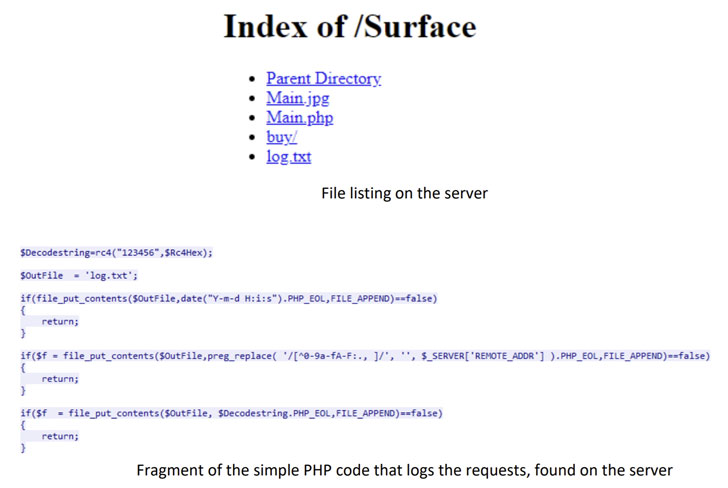
Verify Place explained the adversary put substantial work into hiding their action by transforming its infrastructure numerous instances considering the fact that its growth in 2017, with the backdoor acquiring its possess truthful share of revisions to make it much more resilient to examination and lessen the detection prices at each individual phase.
The very long-running marketing campaign has been joined with “medium to significant self esteem” to a Chinese superior persistent threat (APT) group it calls “SharpPanda” based mostly on exam variations of the backdoor relationship back to 2018 that were being uploaded to VirusTotal from China and the actor’s use of Royal Road RTF weaponizer, a software that been used in strategies attributed to properly-recognized Chinese danger teams because late 2018.
A number of other clues point to this summary, like the point that the command-and-manage (C2) servers returned payloads only concerning 01:00 and 08:00 UTC, which the scientists suspect are the doing work hrs in the attackers’ nation, and that no payloads ended up returned by the C2 servers involving Might 1 and 5 — even throughout doing work hours — which coincides with the Labor Day holidays in China.
The growth is nonetheless a further indicator that multiple cyberthreat teams believed to be doing the job in guidance of China’s long-time period financial interests are continuing to hammer away at networks belonging to governments and companies, although at the same time paying out a excellent offer of time refining the applications in their arsenal in buy to disguise their intrusions.
“All the proof details to the point that we are dealing with a highly-structured procedure that positioned considerable energy into remaining underneath the radar,” Finkelsteen said. “All in all, the attackers, who we consider to be a Chinese danger team, were really systematic in their method.”
“The attackers are not only fascinated in cold data, but also what is going on on a target’s own personal computer at any moment, resulting in are living espionage. While we ended up ready to block the surveillance procedure for the Southeast Asian govt explained, it is really achievable that the danger group is utilizing its new cyber espionage weapon on other targets all over the world,” he included.
Located this post intriguing? Stick to THN on Facebook, Twitter and LinkedIn to read more unique content we submit.
Some parts of this short article are sourced from:
thehackernews.com

 Three-Quarters of Security Leaders Report Increase in Cyber-Attacks in Past Year
Three-Quarters of Security Leaders Report Increase in Cyber-Attacks in Past Year