The Keksec menace actor has been joined to a formerly undocumented malware pressure, which has been noticed in the wild masquerading as an extension for Chromium-based mostly web browsers to enslave compromised equipment into a botnet.
Termed Cloud9 by security agency Zimperium, the destructive browser add-on comes with a extensive selection of attributes that allows it to siphon cookies, log keystrokes, inject arbitrary JavaScript code, mine crypto, and even enlist the host to have out DDoS attacks.
The extension “not only steals the details offered through the browser session but can also set up malware on a user’s product and subsequently assume regulate of the full machine,” Zimperium researcher Nipun Gupta reported in a new report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
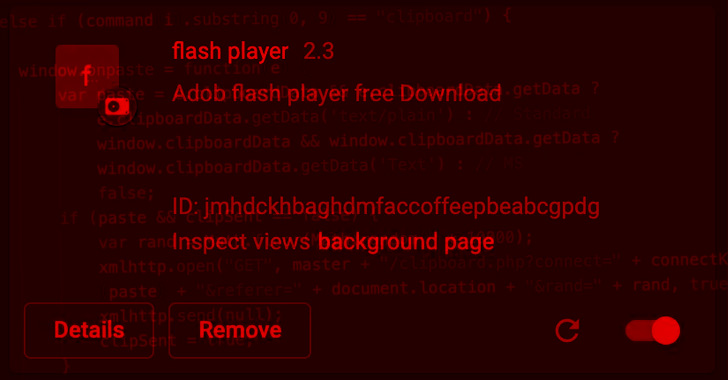
The JavaScript botnet just isn’t distributed by way of Chrome Web Retailer or Microsoft Edge Add-ons, but rather by means of phony executables and rogue internet sites disguised as Adobe Flash Player updates.
At the time put in, the extension is intended to inject a JavaScript file termed “marketing campaign.js” on all webpages, indicating the malware could also operate as a standalone piece of code on any internet site, legit or normally, possibly leading watering hole attacks.
The JavaScript code usually takes accountability for cryptojacking functions, abusing the victim’s computing resources to illicitly mine cryptocurrencies, as very well as inject a 2nd script named “cthulhu.js.”
This attack chain, in change, exploits flaws in web browsers such as Mozilla Firefox (CVE-2019-11708, CVE-2019-9810), Internet Explorer (CVE-2014-6332, CVE-2016-0189), and Edge (CVE-2016-7200) to escape the browser sandbox and deploy malware on the process.
The script even more functions as a keylogger and a conduit for launching extra instructions acquired from a remote server, letting it to steal clipboard facts, browser cookies, and launching layer 7 DDoS attacks towards any domain.
Zimperium attributed the malware to a menace actor tracked as Keksec (aka Kek Security, Necro, and FreakOut), which has a record of creating a extensive variety of botnet malware, which includes EnemyBot, for crypto mining and DDoS operations.
The connection to Keksec arrives from overlaps in the domains that were being formerly identified as employed by the malware team.

The point that Cloud9 is JavaScript-based and is presented either for cost-free or a tiny price on hacker forums makes it doable for less-experienced cybercriminals to get simple obtain to lower-value solutions for launching attacks targeting different browsers and working methods.
The disclosure comes around a few months soon after Zimperium identified a malicious browser insert-on dubbed ABCsoup that posed as a Google Translate device to strike Russian people of Google Chrome, Opera, and Mozilla Firefox browsers.
“Customers should be properly trained on the threats affiliated with browser extensions outside the house of official repositories, and enterprises ought to contemplate what security controls they have in position for these hazards,” Gupta mentioned.
Found this posting appealing? Observe THN on Fb, Twitter and LinkedIn to study more exclusive articles we put up.
Some areas of this short article are sourced from:
thehackernews.com

 Top 5 API Security Myths That Are Crushing Your Business
Top 5 API Security Myths That Are Crushing Your Business