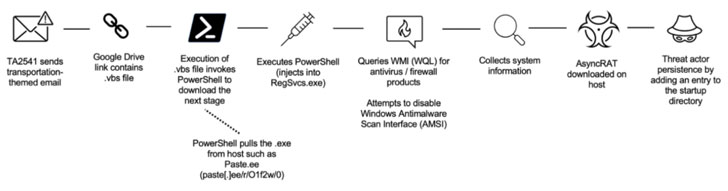
Entities in the aviation, aerospace, transportation, manufacturing, and protection industries have been focused by a persistent menace team considering the fact that at the very least 2017 as component of a string of spear-phishing strategies mounted to provide a wide variety of remote accessibility trojans (RATs) on compromised systems.
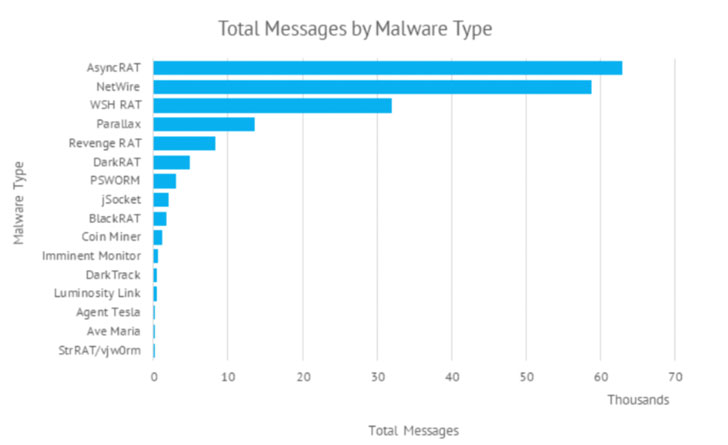
The use of commodity malware these kinds of as AsyncRAT and NetWire, among the others, has led organization security organization Proofpoint to a “cybercriminal menace actor” codenamed TA2541 that employs “wide concentrating on with superior volume messages.” The best objective of the intrusions is unidentified as nevertheless.
Social engineering lures utilised by the team does not count on topical themes but relatively leverages decoy messages associated to aviation, logistics, transportation, and travel. That said, TA2541 did briefly pivot to COVID-19-themed lures in the spring of 2020, distributing e-mail relating to cargo shipments of private protective products (PPE) or testing kits.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Although TA2541 is steady in some behaviors, these types of as using emails masquerading as aviation corporations to distribute remote accessibility trojans, other strategies such as supply strategy, attachments, URLs, infrastructure, and malware type have transformed,” Sherrod DeGrippo, vice president of menace study and detection at Proofpoint, instructed The Hacker News.
While before variations of the marketing campaign used macro-laden Microsoft Phrase attachments to drop the RAT payload, new attacks involve back links to cloud expert services hosting the malware. The phishing attacks are stated to strike hundreds of corporations globally, with recurring targets observed in North The usa, Europe, and the Center East.
The recurring use of the exact themes aside, select infection chains have also involved the use of Discord app URLs that place to compressed information containing AgentTesla or Imminent Watch malware, indicative of the malicious use of written content shipping and delivery networks to distribute details collecting implants for remotely controlling compromised equipment.
“Mitigating threats hosted on reputable companies proceeds to be a complicated vector to protect against as it most likely entails implementation of a robust detection stack or policy-dependent blocking of expert services which may well be company-related,” DeGrippo mentioned.
Other techniques of curiosity utilized by TA2541 incorporate the use of Virtual Non-public Servers (VPS) for their email sending infrastructure and dynamic DNS for command-and-control (C2) pursuits.
With Microsoft saying plans to change off macros by default for internet-downloaded documents starting April 2022, the shift is predicted to cause menace actors to action up and change to other strategies ought to macros grow to be an inefficient technique of shipping.
“While macro-laden Office files are amongst the most frequently applied methods primary to down load and execution of destructive payloads, abuse of reputable hosting expert services is also by now popular,” DeGrippo explained.
“Further more, we regularly observe actors ‘containerize’ payloads, using archive and picture documents (e.g., .ZIP, .ISO, and so forth.) which also can impact skill to detect and assess in some environments. As often, danger actors will pivot to use what is powerful.”
Uncovered this report exciting? Follow THN on Fb, Twitter and LinkedIn to examine a lot more exclusive content material we publish.
Some parts of this short article are sourced from:
thehackernews.com




 New MyloBot Malware Variant Sends Sextortion Emails Demanding $2,732 in Bitcoin
New MyloBot Malware Variant Sends Sextortion Emails Demanding $2,732 in Bitcoin