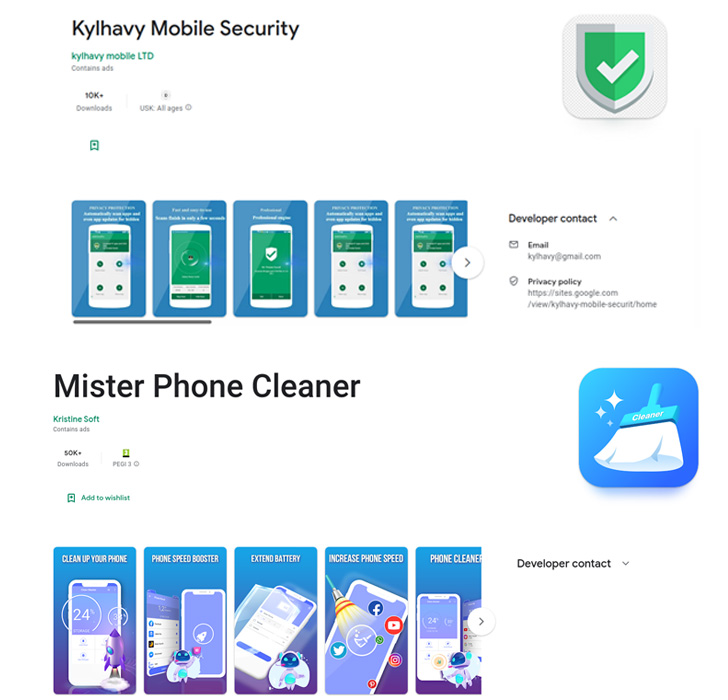
The notorious Android banking trojan regarded as SharkBot has as soon as once more built an overall look on the Google Participate in Keep by masquerading as antivirus and cleaner apps.
“This new dropper doesn’t depend on Accessibility permissions to automatically complete the set up of the dropper Sharkbot malware,” NCC Group’s Fox-IT mentioned in a report. “Instead, this new version asks the target to install the malware as a fake update for the antivirus to stay secured in opposition to threats.”
The applications in problem, Mister Phone Cleaner and Kylhavy Cellular Security, have in excess of 60,000 installations between them and are developed to focus on customers in Spain, Australia, Poland, Germany, the U.S., and Austria –

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

- Mister Phone Cleaner (com.mbkristine8.cleanmaster, 50,000+ downloads)
- Kylhavy Mobile Security (com.kylhavy.antivirus, 10,000+ downloads)
The droppers are built to drop a new edition of SharkBot, dubbed V2 by Dutch security agency ThreatFabric, which capabilities an current command-and-regulate (C2) communication mechanism, a area generation algorithm (DGA), and a completely refactored codebase.
Fox-IT mentioned it identified a newer version 2.25 on August 22, 2022, that introduces a operate to siphon cookies when victims log in to their bank accounts, although also eliminating the means to instantly reply to incoming messages with one-way links to the malware for propagation.
By eschewing the Accessibility permissions for putting in SharkBot, the progress highlights that the operators are actively tweaking their strategies to stay clear of detection, not to point out find alternative approaches in the confront of Google’s freshly imposed restrictions to curtail the abuse of the APIs.

Other notable information stealing abilities contain injecting bogus overlays to harvest bank account credentials, logging keystrokes, intercepting SMS messages, and carrying out fraudulent fund transfers making use of the Automated Transfer Technique (ATS).
It can be no shock that malware poses an evolving and omnipresent menace, and despite ongoing endeavours on the section of Apple and Google, app merchants are susceptible to unknowingly being abused for distribution, with the builders of these apps making an attempt every single trick in the e-book to dodge security checks.
“Until finally now, SharkBot’s builders appear to have been focusing on the dropper in get to preserve utilizing Google Play Retail store to distribute their malware in the newest campaigns,” researchers Alberto Segura and Mike Stokkel reported.
Uncovered this posting intriguing? Abide by THN on Fb, Twitter and LinkedIn to read through far more exceptional content material we publish.
Some parts of this write-up are sourced from:
thehackernews.com

 Samsung Admits Data Breach that Exposed Details of Some U.S. Customers
Samsung Admits Data Breach that Exposed Details of Some U.S. Customers