In a substantial sting operation, the U.S. Federal Bureau of Investigation (FBI) and Australian Federal Law enforcement (AFP) ran an “encrypted chat” provider identified as ANoM for just about 3 years to intercept 27 million messages in between prison gang members globally.
Dubbed Procedure Ironside (AFP), Procedure Greenlight (Europol), and Procedure Trojan Protect (FBI), the extensive-expression covert probe into transnational and serious arranged criminal offense culminated in the arrests of 224 offenders on 526 fees in Australia, with 55 luxury automobiles, 8 tons of cocaine, 22 tons of cannabis and hashish resin, 250 firearms, and more than $48 million in a variety of currencies and cryptocurrencies seized in raids close to the environment.
A complete of extra than 800 arrests have been documented throughout 18 nations around the world, such as New Zealand, Germany, and Sweden. Europol named it the “most significant ever legislation enforcement procedure from encrypted communication.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The communications allegedly concerned plots to eliminate, mass drug trafficking, and gun distribution, in accordance to the AFP. Entry to these encrypted messages was obtained lawfully through utilizing the Telecommunications and Other Legislation Modification (Help and Access) Act 2018, the agency included.
“For pretty much 3 several years, the AFP and the FBI have monitored criminals’ encrypted communications in excess of a Devoted Encrypted Communications Platform,” AFP reported. “The AFP created a functionality that permitted regulation enforcement to access, decrypt and browse communications on the platform. The AFP and FBI were equipped to capture all the information sent amongst gadgets making use of the system.”
The encryption obstacles have been surmounted by inserting a grasp essential into ANoM’s encryption technique that was stealthily attached to each information, therefore enabling the regulation enforcement to execute a man-in-the-middle (MitM) plan to decrypt and retrieve the messages as they ended up transmitted. For gadgets located outside of the U.S., an encrypted “BCC” duplicate of the messages was forwarded to a server exterior of the U.S., from the place it was forwarded to a next FBI-owned server for subsequent decryption.

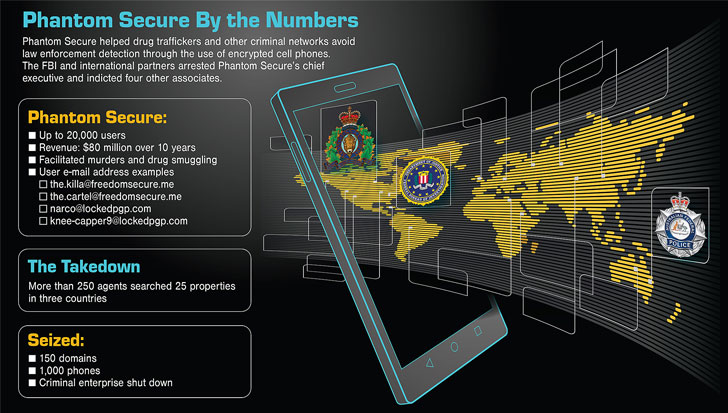
ANoM (aka Anøm) is mentioned to have been intentionally made to fill the vacuum remaining by Phantom Protected, yet another encrypted phone support dismantled by the FBI in 2018, therefore allowing for the businesses to check the conversations devoid of the criminals’ awareness. In a transfer echoing the latter, criminals essential to be aspect of a closed network to get maintain of a phone on which ANoM came preinstalled, whilst the products on their own were being stripped of all other operation.

Amid some of the characteristics of the application involved —
- Deliver encrypted text and voice messages
- Make safe voice phone calls
- Share photos, movies, animated GIFs, places, drawings and a lot more.
- Send out documents of any type
In addition, phone homeowners can also confirm their contacts by way of a QR code, develop distribution lists, and chat fully anonymously without even demanding a phone number, in accordance to a listing from the now taken down anom.io internet site.

Procedure Ironside follows similar law enforcement steps that involved infiltrating encrypted chat system EncroChat to observe millions of encrypted messages sent by arranged criminal offense networks via the system. Previously this year, a coordinated physical exercise below the identify “Procedure Argus” staged important interventions against Sky ECC, primary to nearly 275 raids and the arrest of 91 suspects, moreover seizing 17 tonnes of cocaine and €1.2 million.
The FBI used a private human resource, who experienced beforehand marketed phones from equally Phantom Secure and Sky Worldwide to criminal organizations and had “invested a significant volume of dollars into the enhancement of a new hardened encrypted unit” (i.e., ANoM), to distribute the units to felony networks.
“The products organically circulated and grew in popularity between criminals, who were being assured of the legitimacy of the application due to the fact high-profile organised crime figures vouched for its integrity,” the AFP stated. By Could 2021, the telephones, which were procured from the black market place, experienced improved to 11,800 in range, of which about 9,000 are in lively use, spanning more than 300 felony syndicates working in extra than 100 nations around the world.
The top five nations wherever Anom units are at this time employed are Germany, the Netherlands, Spain, Australia, and Serbia, unsealed court files demonstrate, with its consumer base possessing developed noticeably in the aftermath of Sky ECC’s disruption.
“Immediately after the takedown of Sky ECC in March 2021, a lot of organised criminal offense networks sought a brief encrypted alternative for a communication platform that would allow them to evade law enforcement detection,” Europol claimed. “This was a deliberate and strategic aspect of OTF Greenlight / Procedure Trojan Protect ensuing in the migration of some of the prison Sky ECC client foundation to the FBI-managed system ANoM.”
The global coalition that participated in the joint procedure consisted of Australia, Austria, Canada, Denmark, Estonia, Finland, Germany, Hungary, Lithuania, New Zealand, the Netherlands, Norway, Sweden, the U.K. (including Scotland), and the U.S.
“A objective of the Trojan Protect investigation is to shake the self confidence in this whole industry mainly because the FBI is prepared and in a position to enter this room and observe messages,” for each the court documents.
Found this posting appealing? Follow THN on Facebook, Twitter and LinkedIn to read more distinctive articles we publish.
Some pieces of this post are sourced from:
thehackernews.com


 Horizon3.ai looks to expand NodeZero tech with new funding
Horizon3.ai looks to expand NodeZero tech with new funding