An exhaustive evaluation of FIN7 has unmasked the cybercrime syndicate’s organizational hierarchy, alongside unraveling its job as an affiliate for mounting ransomware attacks.
It has also exposed further associations amongst the team and the much larger danger ecosystem comprising the now-defunct ransomware DarkSide, REvil, and LockBit households.
The highly lively danger team, also acknowledged as Carbanak, is identified for employing an in depth arsenal of resources and ways to expand its “cybercrime horizons,” such as introducing ransomware to its playbook and environment up phony security companies to entice scientists into conducting ransomware attacks below the guise of penetration screening.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
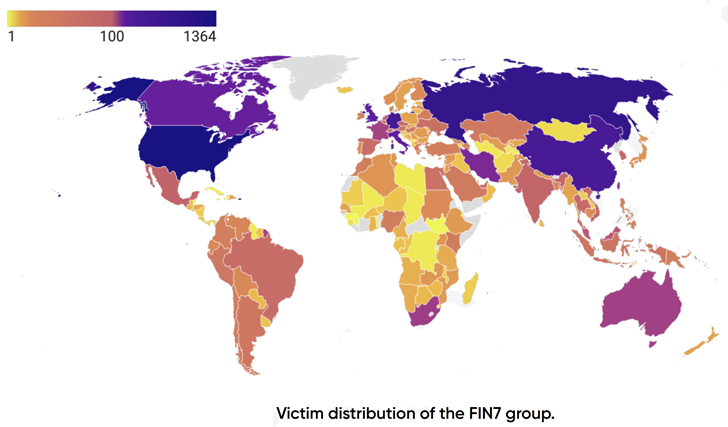
Additional than 8,147 victims have been compromised by the monetarily motivated adversary across the world, with a the vast majority of the entities situated in the U.S. Other prominent countries include things like China, Germany, Canada, Italy, and the U.K.
FIN7’s intrusion procedures, more than the several years, have even more diversified beyond classic social engineering to involve infected USB drives, application source chain compromise and the use of stolen qualifications bought from underground markets.

“Nowadays, its preliminary method is to meticulously decide large-worth organizations from the pool of now compromised company techniques and pressure them to spend substantial ransoms to restore their information or seek out special means to monetize the knowledge and remote obtain,” PRODAFT mentioned in a report shared with The Hacker News.
In accordance to the Swiss cybersecurity business, the threat actors have also been noticed to weaponize flaws in Microsoft Trade these kinds of as CVE-2020-0688, CVE-2021-42321, ProxyLogon, and ProxyShell flaws in Microsoft Exchange Server to receive a foothold into concentrate on environments.
The use of double extortion ways notwithstanding, attacks mounted by the team have deployed backdoors on the compromised systems, even in eventualities exactly where the victim has currently paid a ransom.
The notion is to resell accessibility to other ransomware outfits and re-focus on the victims as part of its illicit money-generating scheme, underscoring its makes an attempt to decrease initiatives and maximize earnings, not to point out prioritize companies centered on their once-a-year revenues, established dates, and the range of staff.
This “demonstrates a unique form of feasibility research considered a one of a kind behavior among the cybercrime teams,” the scientists explained.
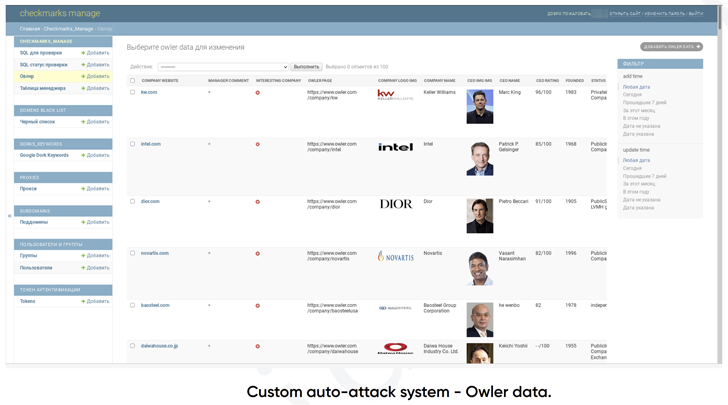
Put in a different way, the modus operandi of FIN7 boils down to this: It makes use of solutions like Dun & Bradstreet (DNB), Crunchbase, Owler, and Zoominfo to shortlist companies and companies with the greatest profits. It also takes advantage of other website analytics platforms like MuStat and Similarweb to check visitors to the victims’ sites.
Original entry is then attained by one of the a lot of intrusion vectors, adopted by exfiltrating facts, encrypting information, and sooner or later deciding the ransom volume based mostly on the company’s profits.
These infection sequences are also intended to load the distant obtain trojans such as Carbanak, Lizar (aka Tirion), and IceBot, the latter of which was initially documented by Recorded Long term-owned Gemini Advisory in January 2022.
Other applications formulated by FIN7 encompass modules to automate scans for susceptible Microsoft Exchange servers and other community-facing web programs as properly as Cobalt Strike for write-up-exploitation.
In but yet another indication that prison teams perform like common companies, FIN7 follows a workforce structure consisting of leading-degree management, builders, pentesters, affiliate marketers, and advertising and marketing groups, every single of whom are tasked with unique responsibilities.
When two users named Alex and Rash are the main players powering the procedure, a 3rd managerial member named Sergey-Oleg is responsible for delegating obligations to the group’s other associates and overseeing their execution.
Even so, it has also been observed that operators in administrator positions engage in coercion and blackmail to intimidate staff users into working much more and issue ultimatums to “harm their family members associates in circumstance of resigning or escaping from responsibilities.”
The conclusions appear extra than a month just after cybersecurity enterprise SentinelOne determined probable hyperlinks involving FIN7 and the Black Basta ransomware procedure.
“FIN7 has founded alone as an terribly versatile and very well-known APT team that targets enterprise organizations,” PRODAFT concluded.
“Their signature transfer is to totally research the organizations based mostly on their profits, worker count, headquarters and site information to pinpoint the most rewarding targets. Although they have inside issues related to the unequal distribution of obtained monetary resources and considerably questionable methods towards their members, they have managed to build a powerful presence in the cybercrime sphere.”
Discovered this write-up exciting? Stick to us on Twitter and LinkedIn to browse much more exceptional material we article.
Some components of this posting are sourced from:
thehackernews.com


 The Era of Cyber Threat Intelligence Sharing
The Era of Cyber Threat Intelligence Sharing