The infamous cybercrime team recognised as FIN7 has diversified its original obtain vectors to include software supply chain compromise and the use of stolen credentials, new analysis has revealed.
“Data theft extortion or ransomware deployment pursuing FIN7-attributed exercise at several companies, as very well as complex overlaps, suggests that FIN7 actors have been linked with numerous ransomware functions about time,” incident reaction organization Mandiant said in a Monday evaluation.
The cybercriminal group, considering the fact that its emergence in the mid-2010s, has acquired notoriety for significant-scale malware strategies targeting the stage-of-sale (POS) systems aimed at cafe, gambling, and hospitality industries with credit card-stealing malware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

FIN7’s shift in monetization approach in direction of ransomware follows an Oct 2021 report from Recorded Future’s Gemini Advisory unit, which observed the adversary environment up a phony entrance firm named Bastion Protected to recruit unwitting penetration testers in a lead up to a ransomware attack.
Then previously this January, the U.S. Federal Bureau of Investigation (FBI) issued a Flash Warn warning companies that the financially enthusiastic gang was sending malicious USB drives (aka BadUSB) to U.S. organization targets in the transportation, insurance policies, and defense industries to infect methods with malware, including ransomware.
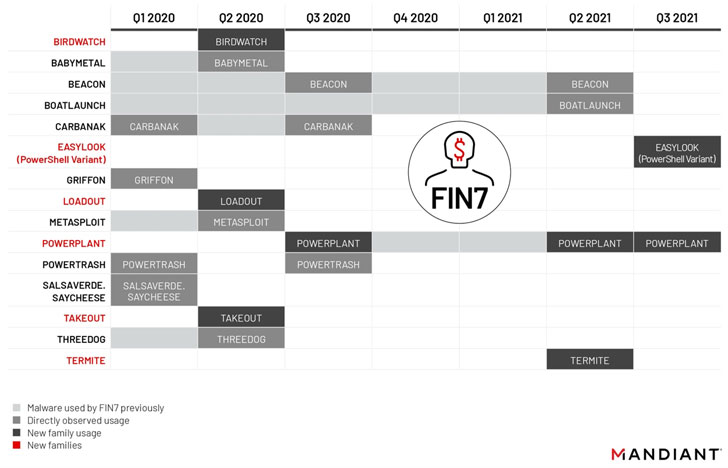
Current intrusions staged by the actor because 2020 have involved the deployment of a wide PowerShell backdoor framework termed POWERPLANT, continuing the group’s penchant for applying PowerShell-centered malware for its offensive functions.
“There is no doubt about it, PowerShell is FIN7’s love language,” Mandiant scientists claimed.
In one particular of the attacks, FIN7 was noticed compromising a site that sells electronic products in order to tweak multiple down load inbound links to make them level to an Amazon S3 bucket hosting trojanized versions that contained Atera Agent, a authentic remote management software, which then shipped POWERPLANT to the victim’s program.
The supply chain attack also marks the group’s evolving tradecraft for preliminary entry and the deployment of very first-stage malware payloads, which have normally centered all around phishing techniques.
Other resources utilized by the group to aid its infiltrations contain EASYLOOK, a reconnaissance utility BOATLAUNCH, a helper module created to bypass Windows AntiMalware Scan Interface (AMSI) and BIRDWATCH, a .NET-based mostly downloader used to fetch and execute next-phase binaries been given above HTTP.
“Even with indictments of members of FIN7 in 2018 and a linked sentencing in 2021 declared by the U.S. Section of Justice, at minimum some customers of FIN7 have remained active and keep on to evolve their prison operations more than time,” Mandiant researchers stated.
“Throughout their evolution, FIN7 has amplified the pace of their operational tempo, the scope of their concentrating on, and even probably their associations with other ransomware functions in the cybercriminal underground.”
Observed this posting interesting? Follow THN on Fb, Twitter and LinkedIn to study additional distinctive articles we article.
Some components of this write-up are sourced from:
thehackernews.com


 Battling Cybersecurity Risk: How to Start Somewhere, Right Now
Battling Cybersecurity Risk: How to Start Somewhere, Right Now