Each individual calendar year, billions of qualifications show up on the net, be it on the dark web, very clear web, paste internet sites, or in details dumps shared by cybercriminals. These credentials are often employed for account takeover attacks, exposing companies to breaches, ransomware, and data theft.
Though CISOs are conscious of expanding identity threats and have numerous resources in their arsenal to assist decrease the likely risk, the truth is that current methodologies have confirmed largely ineffective. According to the 2022 Verizon Data Breach Investigations Report, over 60% of breaches involve compromised qualifications.
Attackers use procedures these kinds of as social engineering, brute power, and buying leaked credentials on the dark web to compromise reputable identities and obtain unauthorized accessibility to sufferer organizations’ methods and means.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Adversaries generally leverage the fact that some passwords are shared amongst different people, making it less complicated to breach several accounts in the very same business. Some workforce reuse passwords. Others use a shared sample in their passwords amid a variety of web sites. An adversary can use cracking procedures and dictionary attacks to overcome password permutations by leveraging a shared pattern, even if the password is hashed. The most important problem to the business is that hackers only will need a one password match to split in.
To correctly mitigate their publicity, specified existing threat intelligence, companies have to have to concentrate on what is exploitable from the adversary’s perspective.
In this article are 5 measures corporations really should consider to mitigate credentials publicity:
Obtain Leaked Qualifications Knowledge
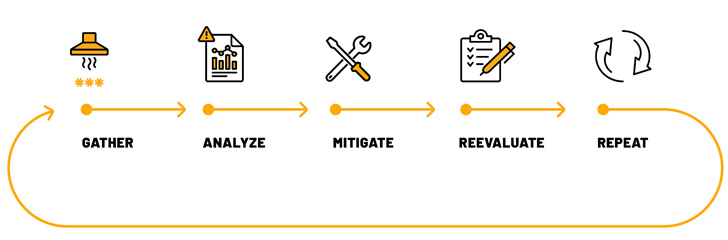
To start off addressing the dilemma, security groups need to acquire information on credentials that have been leaked externally in many places, from the open web to the dark web. This can give them an preliminary indicator of the risk to their group, as very well as the person qualifications that need to be updated.
Review the Info
From there, security teams will need to recognize the credentials that could truly lead to security exposures. An attacker would consider the username and password combinations (either cleartext or hashed), then consider to use them to entry services or devices. Security groups ought to use related strategies to evaluate their hazards. This includes:
- Checking if the qualifications make it possible for obtain to the organization’s externally uncovered belongings, this kind of as web solutions and databases
- Trying to crack captured password hashes
- Validating matches involving leaked credential details and the organization’s identity administration applications, this sort of as Energetic Listing
- Manipulating the raw information to raise the accomplished quantity of compromised identities. For instance, end users typically use the very same password styles. Even if the leaked credentials do not make it possible for obtain to external-experiencing belongings or match Energetic Directory entries, it could be probable to locate added matches by testing versions.
Mitigate Credential Exposures
Soon after validating the leaked qualifications to recognize precise exposures, businesses can acquire specific motion to mitigate the risk of an attacker accomplishing the identical. For instance, they could erase inactive leaked accounts in Active Directory or initiate password variations for lively customers.
Reevaluate Security Processes
Immediately after direct mitigation, security groups ought to consider whether their existing processes are risk-free and make improvements the place probable. For occasion, if they are dealing with many matched leaked credentials, they may well suggest changing the whole password plan throughout the corporation. In the same way, if inactive customers are discovered in Energetic Listing, it may well be effective to revisit the staff offboarding process.
Repeat Instantly
Attackers are continually adopting new techniques. Attack surfaces alter, with new identities remaining added and removed on a routine foundation. Equally, humans will usually be prone to accidental blunders. As a result, a 1-time effort to obtain, validate, and mitigate credential exposures is not enough. To obtain sustainable security in a hugely dynamic menace landscape, companies need to repeatedly repeat this approach.
Even so, useful resource-constrained security groups can not afford to pay for to manually perform all these measures on a enough cadence. The only way to correctly regulate the menace is to automate the validation course of action.
Pentera presents 1 way for companies to immediately emulate attackers’ procedures, trying to exploit leaked credentials both of those externally and within the network. To close the validation loop, Pentera supplies insights into entire attack paths, alongside with actionable remediation actions that make it possible for organizations to competently optimize their identity power.
To come across out how Pentera can support you reduce your organization’s risk of inadvertent credential exposure, get hold of us currently to request a demo.
Uncovered this short article intriguing? Follow THN on Facebook, Twitter and LinkedIn to examine far more unique information we publish.
Some parts of this post are sourced from:
thehackernews.com


 Mobile, Cloud and Email Are Top Threat Vectors For 2023
Mobile, Cloud and Email Are Top Threat Vectors For 2023