An ongoing malware campaign has been uncovered exploiting not too long ago disclosed vulnerabilities in Linux gadgets to co-choose the systems into an IRC botnet for launching dispersed denial-of-support (DDoS) attacks and mining Monero cryptocurrency.
The attacks contain a new malware variant called “FreakOut” that leverages newly patched flaws in TerraMaster, Laminas Job (formerly Zend Framework), and Liferay Portal, in accordance to Verify Level Research’s new analysis posted right now and shared with The Hacker Information.
Attributing the malware to be the operate of a lengthy-time cybercrime hacker — who goes by the aliases Fl0urite and Freak on HackForums and Pastebin as early as 2015 — the scientists explained the flaws — CVE-2020-28188, CVE-2021-3007, and CVE-2020-7961 — had been weaponized to inject and execute destructive commands in the server.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
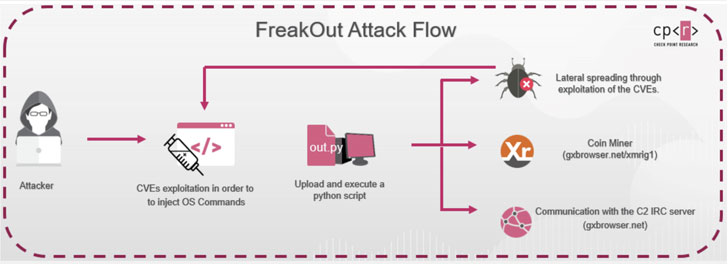
Regardless of the vulnerabilities exploited, the finish objective of the attacker seems to be to download and execute a Python script named “out.py” making use of Python 2, which arrived at finish-of-everyday living very last year — implying that the menace actor is banking on the likelihood that that victim gadgets have this deprecated model put in.
“The malware, downloaded from the web-site hxxp://gxbrowser[.]net, is an obfuscated Python script which includes polymorphic code, with the obfuscation altering each and every time the script is downloaded,” the scientists said, introducing the very first attack attempting to obtain the file was observed on January 8.
And in truth, a few times afterwards, cybersecurity business F5 Labs warned of a sequence of attacks targeting NAS products from TerraMaster (CVE-2020-28188) and Liferay CMS (CVE-2020-7961) in an endeavor to distribute N3Cr0m0rPh IRC bot and Monero cryptocurrency miner.
An IRC Botnet is a collection of equipment contaminated with malware that can be managed remotely via an IRC channel to execute destructive commands.
In FreakOut’s case, the compromised units are configured to communicate with a hardcoded command-and-management (C2) server from where by they obtain command messages to execute.
The malware also comes with in depth abilities that make it possible for it to execute numerous jobs, like port scanning, facts collecting, creation and sending of data packets, network sniffing, and DDoS and flooding.
Furthermore, the hosts can be commandeered as a part of a botnet procedure for crypto-mining, spreading laterally across the network, and launching attacks on outside targets whilst masquerading as the sufferer company.
With hundreds of equipment currently infected in days of launching the attack, the scientists warn, FreakOut will ratchet up to bigger ranges in the in close proximity to long run.
For its element, TerraMaster is expected to patch the vulnerability in model 4.2.07. In the meantime, it is really encouraged that consumers up grade to Liferay Portal 7.2 CE GA2 (7.2.1) or later on and laminas-http 2.14.2 to mitigate the risk involved with the flaws.
“What we have discovered is a reside and ongoing cyber attack campaign concentrating on particular Linux buyers,” claimed Adi Ikan, head of network cybersecurity Investigate at Check out Place. “The attacker behind this campaign is really knowledgeable in cybercrime and highly dangerous.”
“The point that some of the vulnerabilities exploited were being just revealed, gives us all a very good case in point for highlighting the importance of securing your network on an ongoing foundation with the hottest patches and updates.”
Found this report appealing? Observe THN on Facebook, Twitter and LinkedIn to examine a lot more exclusive content material we publish.
Some parts of this write-up are sourced from:
thehackernews.com

 GDPR Fines Surge 39% Over Past Year Despite #COVID19
GDPR Fines Surge 39% Over Past Year Despite #COVID19