DevOps system GitLab has launched software package updates to deal with a critical security vulnerability that, if most likely exploited, could allow an adversary to seize control of accounts.
Tracked as CVE-2022-1162, the issue has a CVSS rating of 9.1 and is said to have been found internally by the GitLab crew.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“A hardcoded password was set for accounts registered utilizing an OmniAuth service provider (e.g., OAuth, LDAP, SAML) in GitLab CE/EE versions 14.7 prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to most likely take about accounts,” the business stated in an advisory printed on March 31.
GitLab, which has resolved the bug with the most up-to-date release of variations 14.9.2, 14.8.5, and 14.7.7 for GitLab Community Version (CE) and Company Edition (EE), also explained it took the action of resetting the password of an unspecified number of consumers out of an abundance of caution.
“Our investigation exhibits no indicator that consumers or accounts have been compromised,” it added.
The firm has also released a script that directors of self-managed cases can run to one out accounts possibly impacted by CVE-2022-1162. Just after the impacted accounts are recognized, a password reset has been suggested.
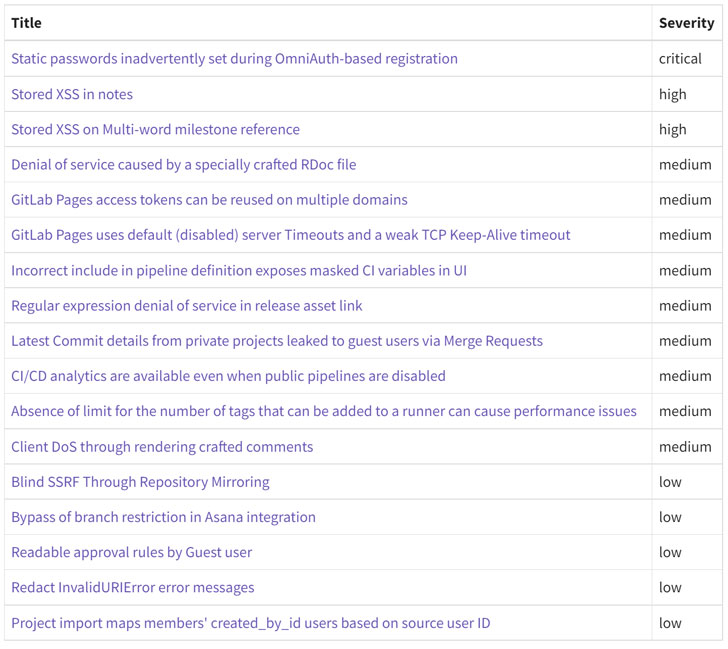
Also resolved by GitLab as section of the security update are two large-severity stored cross-web-site scripting (XSS) bugs (CVE-2022-1175 and CVE-2022-1190) as very well as nine medium-severity flaws and five issues that are rated reduced in severity.
In light-weight of the criticality of some of the issues, consumers functioning afflicted installations are really recommended to enhance to the most current edition as before long as probable.
Observed this post appealing? Adhere to THN on Facebook, Twitter and LinkedIn to read far more special content material we write-up.
Some parts of this post are sourced from:
thehackernews.com



 House Passes Better Cybercrime Metrics Act
House Passes Better Cybercrime Metrics Act