The operators of the Glupteba botnet resurfaced in June 2022 as component of a renewed and “upscaled” marketing campaign, months after Google disrupted the destructive exercise.
The ongoing attack is suggestive of the malware’s resilience in the experience of takedowns, cybersecurity corporation Nozomi Networks stated in a generate-up. “In addition, there was a tenfold improve in TOR concealed solutions getting made use of as C2 servers due to the fact the 2021 campaign,” it noted.
The malware, which is distributed through fraudulent advertisements or software package cracks, is also equipped to retrieve more payloads that help it to steal qualifications, mine cryptocurrencies, and extend its attain by exploiting vulnerabilities in IoT gadgets from MikroTik and Netgear.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
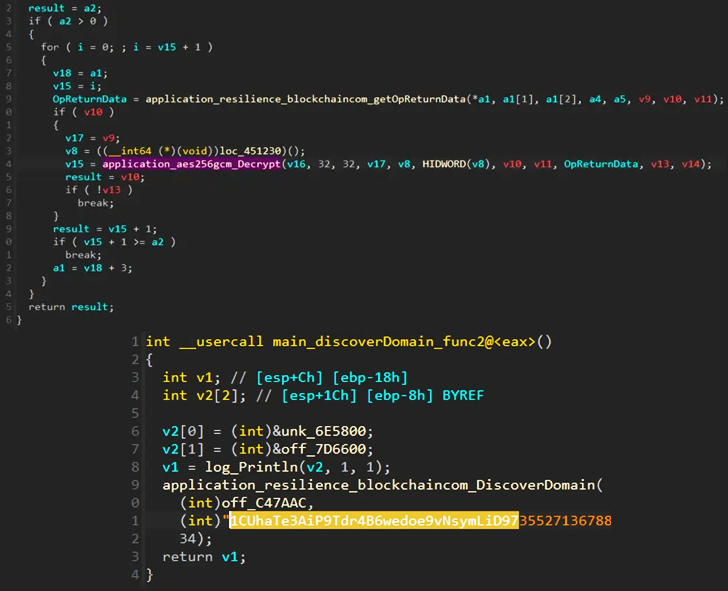
It really is also an occasion of an uncommon malware that leverages blockchain as a system for command-and-handle (C2) given that at the very least 2019, rendering its infrastructure resistant to takedown endeavours as in the scenario of a traditional server.

Particularly, the botnet is developed to look for the general public Bitcoin blockchain for transactions related to wallet addresses owned by the menace actor so as to fetch the encrypted C2 server tackle.
“This is created doable by the OP_RETURN opcode that permits storage of up to 80 bytes of arbitrary details inside of the signature script,” the industrial and IoT security business explained, adding the system also can make Glupteba really hard to dismantle as “there is no way to erase nor censor a validated Bitcoin transaction.”
The strategy also would make it practical to substitute a C2 server must it be taken down, as all that is essential for the operators is to publish a new transaction from the actor-managed Bitcoin wallet handle with the encoded up to date server.
In December 2021, Google managed to induce a significant dent to its functions, alongside submitting a lawsuit towards two Russian nationals who oversaw the botnet. Final thirty day period, a U.S. courtroom ruled in favor of the tech big.
“Whilst Glupteba operators have resumed exercise on some non-Google platforms and IoT gadgets, shining a authorized highlight on the team would make it much less attractive for other criminal operations to operate with them,” the internet behemoth pointed out in November.
Nozomi Networks, which examined over 1,500 Glupteba samples uploaded to VirusTotal, reported it was ready to extract 15 wallet addresses that have been set to use by the danger actors relationship all the way back again to June 19, 2019.
The ongoing campaign that commenced in June 2022 is also possibly the greatest wave in the earlier number of a long time, what with the range of rogue bitcoin addresses leaping to 17, up from 4 in 2021.
One particular of people addresses, which was initial energetic on June 1, 2022, has transacted 11 moments to day and is utilized in as numerous as 1,197 artifacts, building it the most commonly used wallet address. The final transaction was recorded on November 8, 2022.
“Danger actors are significantly leveraging blockchain technology to start cyberattacks,” the scientists mentioned. “By having advantage of the dispersed and decentralized nature of blockchain, destructive actors can exploit its anonymity for a selection of attacks, ranging from malware propagation to ransomware distribution.”
Observed this posting interesting? Follow us on Twitter and LinkedIn to study more unique content material we publish.
Some areas of this report are sourced from:
thehackernews.com


 Cybercrime (and Security) Predictions for 2023
Cybercrime (and Security) Predictions for 2023