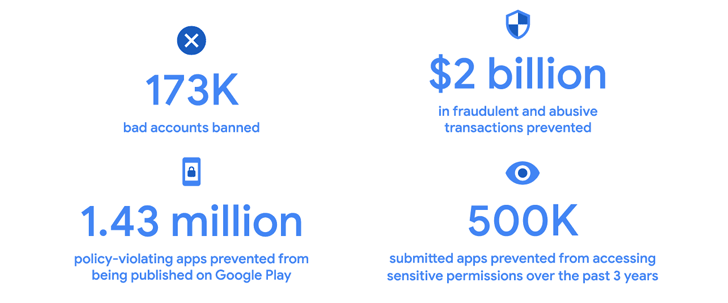
Google disclosed that its improved security functions and application critique procedures served it block 1.43 million undesirable applications from being released to the Participate in Shop in 2022.
In addition, the firm reported it banned 173,000 terrible accounts and fended off in excess of $2 billion in fraudulent and abusive transactions by developer-struggling with features like Voided Buys API, Obfuscated Account ID, and Engage in Integrity API.
The addition of id verification procedures this kind of as phone range and email tackle to be a part of Google Enjoy contributed to a reduction in accounts made use of to publish applications that go in opposition to its insurance policies, Google pointed out.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The lookup behemoth even more claimed it “prevented about 500K submitted apps from unnecessarily accessing delicate permissions about the previous 3 many years.”
“In 2022, the App Security Improvements program helped developers fix ~500K security weaknesses impacting ~300K apps with a blended put in base of somewhere around 250B installs,” it famous.
In distinction, Google blocked 1.2 million policy-violating applications from remaining revealed and banned 190,000 poor accounts in 2021.
The enhancement arrives weeks after Google enacted a new info deletion policy that involves application builders to give a “quickly discoverable alternative” to users from both equally in just an app and outside of it.
Despite these initiatives from Google, cybercriminals are continuing to find strategies around the application storefront’s security protections and publish destructive and adware apps.
Case in issue, McAfee’s Cell Analysis Workforce found out 38 video games masquerading as Minecraft and which have been mounted by no a lot less than 35 million customers worldwide, mainly found in the U.S., Canada, South Korea, and Brazil.
These gaming apps, while giving the promised operation, have been observed to incorporate the HiddenAds malware to stealthily load advertisements in the history to deliver illicit earnings for its operators.
Some of the most downloaded applications are as follows –
- Block Box Learn Diamond (com.very good.robo.sport.builder.craft.block)
- Craft Sword Mini Entertaining (com.craft.earth.fairy.fun.daily.block)
- Block Box Skyland Sword (com.skyland.pet.realm.block.rain.craft)
- Craft Monster Mad Sword (com.skyland.fun.block.match.monster.craft)
- Block Pro Forrest Diamond (com.monster.craft.block.entertaining.robo.fairy)
“1 of the most obtainable information for youthful people today using cell units is game titles,” McAfee stated. “Malware authors are also conscious of this and consider to conceal their malicious options inside of video games.”
Complicating the dilemma is the surge in Android banking malware that can be weaponized by danger actors to get access to sufferer equipment and harvest private details.
An additional rising trend is the use of binding providers to trojanize respectable purposes and conceal a rogue APK payload. This system has been adopted by lousy actors to distribute an Android botnet dubbed DAAM, Cyble stated.
Impending WEBINARLearn to Prevent Ransomware with Serious-Time Security
Join our webinar and learn how to quit ransomware attacks in their tracks with real-time MFA and provider account protection.
Save My Seat!
The malware, the moment set up, establishes connections with a remote server to carry out a wide assortment of nefarious steps, including performing as ransomware by encrypting data files saved in the gadgets working with a password retrieved from the server.
DAAM also abuses Android’s accessibility services to watch users’ action, thereby allowing for it to log keystrokes, report VoIP phone calls from instantaneous messaging apps, gather browser historical past, get in touch with logs, images, screenshots, and SMS messages, operate arbitrary code, and open phishing URLs.
“Malware authors usually leverage real purposes to distribute malicious code to avoid suspicion,” the cybersecurity organization said in an analysis released last thirty day period.
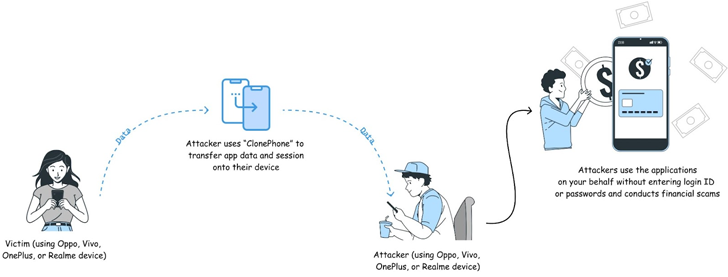
The results also comply with an advisory from CloudSEK, which uncovered that numerous well-known Android purposes like Canva, LinkedIn, Strava, Telegram, and WhatsApp do not invalidate or revalidate session cookies just after app information is transferred from just one unit to one more.
Even though this attack situation requires an adversary to have actual physical accessibility to a target’s phone, it could allow for for account takeover and attain unauthorized obtain to private knowledge.
To mitigate this sort of threats, it can be suggested to permit two-factor authentication (2FA) to add an extra layer of account protection, scrutinize app permissions, secure equipment with a password, and keep away from leaving them unattended in general public sites.
Located this article fascinating? Comply with us on Twitter and LinkedIn to read a lot more distinctive material we article.
Some parts of this posting are sourced from:
thehackernews.com


 CISA Warns of Critical Flaws in Illumina’s DNA Sequencing Instruments
CISA Warns of Critical Flaws in Illumina’s DNA Sequencing Instruments