Google Cloud emblem on a wood track record with pedestrians going for walks on a road in front of it
Google Cloud has released a new risk detection answer for Google Cloud Platform (GCP) exclusively intended to tackle the mounting instances of cryptomining malware functioning as a result of compromised cloud occasions.
Google Cloud stated the Virtual Machine Danger Detection (VMTD) is a first-to-marketplace solution from a key cloud supplier, now available in general public preview as an extra security layer within Security Command Heart (SCC) Top quality.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Virtual device-centered computing accounts for a significant part of businesses’ operations functioning in the cloud and according to a November 2021 risk intelligence report from Google Cloud, cryptomining activity was observed in 86% of all compromised GCP circumstances, producing it the major issue affecting Google Cloud clients.
The time it took for attackers to put in this financially-determined malware was fast, way too, with additional than fifty percent of circumstances (58%) observing malware mounted in just 22 seconds of compromising the system.
Google Cloud claimed in most conditions, this was thanks to exploitation of very poor customer security practices or vulnerable third-party software package. Leveraging the power of cloud computing can enhance the effectiveness of cryptomining malware due to its scalable character, perhaps raising regular monthly cloud costs for organizations by a large sum.
“The financial system of scale enabled by the cloud can enable basically alter the way security is executed for any business functioning in today’s threat landscape,” mentioned Timothy Peacock, item manager at Google Cloud. “As far more providers adopt cloud technologies, security methods built into cloud platforms assistance deal with rising threats for a lot more and extra organisations.
“VMTD is 1 of the strategies we safeguard our Google Cloud System prospects versus escalating attacks like coin mining, facts exfiltration, and ransomware,” he included.
Now accessible in community preview, VMTD detects cryptomining attacks but as it moves closer toward basic availability, Google Cloud explained clients can expect to see a continuous launch of new detective abilities that will integrate with other components of GCP.
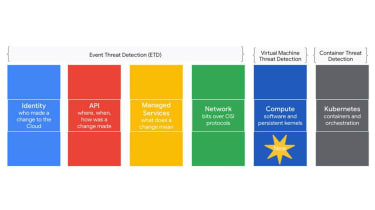
Google Cloud explained VMTD complements the current danger detection capabilities supplied by the existing Party Threat Detection and Container Risk Detection goods, offering protect for compute while the other people providers places like Kubernetes, id, managed services, networking, and API.
Agentless solution
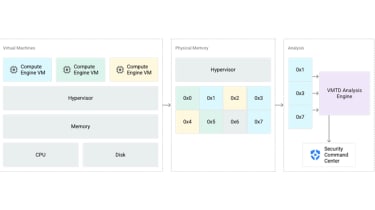
Google Cloud
Google Cloud’s VMTD provides memory scanning for consumers on an agentless foundation, which signifies GCP customers can count on a smaller sized overall performance affect, decreased operational burden, and a significantly less-exposed attack surface.
This is compared with a classic endpoint security model which involves running added program inside virtual machines to assemble indicators and telemetry. In its place, Google Cloud said it ‘instruments the hypervisor’ – the underlying software that “orchestrates” its digital machines – to contain danger detection that is tricky to tamper with.
Some pieces of this posting are sourced from:
www.itpro.co.uk


 Microsoft Takes Aim at Malicious Office Macros
Microsoft Takes Aim at Malicious Office Macros