Google’s cyber security study division has unearthed particulars of first obtain brokers (IABs) doing the job on behalf of some of the most significant ransomware gangs in existence.
IABs are teams of cyber criminals that exploit vulnerabilities in organisations and provide that obtain to the greatest bidder so they can start meaningful cyber attacks without conducting the preliminary leg operate.
The Risk Evaluation Team (TAG) observed the Exotic LILY IAB running from at minimum as far again as September 2021 and has delivered entry to providers for the likes of Conti and FIN12 so they can start lucrative ransomware attacks.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
These types of IAB groups have been functioning for some time but have gained level of popularity in recent yrs and are approaching the peak of their operational maturity, in accordance to the latest reviews.
FIN12 and the now-shuttered Conti are among the most notorious ransomware operators of modern instances. They have equally indiscriminately qualified organisations for economic get and, not like other groups, screen few moral boundaries, the two getting specific hospitals and health care organisations in the previous.
The effectively-resourced Unique LILY team, at the peak of its action, is reported to have specific upwards of 5,000 emails a day throughout 650 global organisations, trying to exploit a Microsoft zero-day vulnerability (CVE-2021-40444) to obtain first entry.
Uniquely private approach
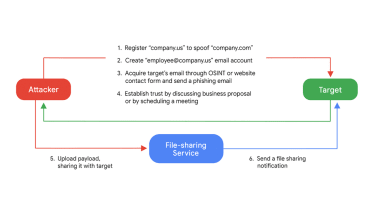
Google’s TAG explained Exotic LILY shown targeted attack techniques such as spoofing organizations and staff members as a means to attaining trust via email strategies but “rather uniquely” devoted a significant amount of time to each and every focus on in an attempt to build rely on.
Like the large-scale ransomware gangs it will work for, Unique LILY is comprised of a lot of people today so they can commit time to every focus on. TAG stated the “level of human-interaction is rather unconventional for cyber criminal offense groups focused on mass-scale operations”.
TAG claimed Exotic LILY would customise organization proposal templates when very first making contact with organisations fairly than relying on just a single, a method demanding extra energy than commonly observed with these types of groups.
The IAB also managed extra communications with the victims in buy to establish have faith in sending a website link to a malicious payload working with reputable file-sharing providers.
The likes of WeTransfer, TransferNow, and OneDrive have been applied to deliver the payload that exploited the Microsoft zero-day, which was a different system the attackers applied to evade detection mechanisms, TAG reported.
Unique LILY’s attack chain remained dependable through TAG’s investigation and can be broken down into just a few techniques:
The team to start with utilized faux on the web profiles with AI-generated faces to impersonate personnel at a spoofed organization, but later resorted to thieving authentic employees’ facts and harvesting more from databases like CrunchBase and RocketReach.
The use of a legitimate file-sharing service turned a impressive system of preventing detection, as not only are they familiar firms, but the concentrate on also gets a genuine file-sharing notification from that service provider to raise the perceived authenticity.
Exotic LILY initial used files containing an exploit for a Microsoft zero-day but later on adjusted strategy to providing ISO documents with concealed BazarLoader DLLs – a fileless attack process also widespread with ransomware teams.
Microsoft shortcut information, regarded as LNK shortcuts, had been also delivered in these ISO documents, with samples indicating they ended up custom-manufactured by Unique LILY instead than off-the-shelf exploit kits, TAG explained.
Some elements of this report are sourced from:
www.itpro.co.uk


 NCSC Launches Awareness Campaign to Strengthen Password Practices
NCSC Launches Awareness Campaign to Strengthen Password Practices