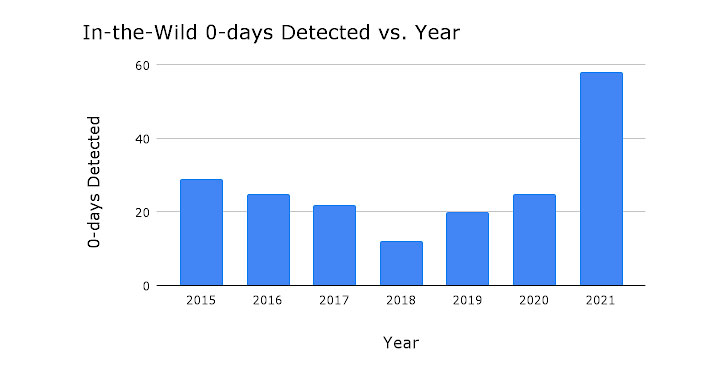
Google Undertaking Zero identified as 2021 a “record yr for in-the-wild -times,” as 58 security vulnerabilities ended up detected and disclosed in the course of the course of the 12 months.
The progress marks far more than a two-fold bounce from the former optimum when 28 -working day exploits ended up tracked in 2015. In contrast, only 25 -day exploits were being detected in 2020.
“The significant uptick in in-the-wild -days in 2021 is due to improved detection and disclosure of these -days, fairly than merely increased usage of -day exploits,” Google Challenge Zero security researcher Maddie Stone stated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Attackers are obtaining good results employing the exact bug styles and exploitation approaches and going immediately after the similar attack surfaces,” Stone additional.
The tech giant’s in-house security staff characterized the exploits as identical to past and publicly known vulnerabilities, with only two of them markedly diverse for the technical sophistication and use of logic bugs to escape the sandbox.
Both of them relate to FORCEDENTRY, a zero-click on iMessage exploit attributed to the Israeli surveillanceware corporation NSO Team. “The exploit was an impressive function of artwork,” Stone claimed.
The sandbox escape is “noteworthy for applying only logic bugs,” Google Project Zero scientists Ian Beer and Samuel Groß explained past month. “The most placing takeaway is the depth of the attack floor reachable from what would hopefully be a reasonably constrained sandbox.”
A system-intelligent breakdown of these exploits displays that most of the in-the-wild -times originated from Chromium (14), adopted by Windows (10), Android (7), WebKit/Safari (7), Microsoft Exchange Server (5), iOS/macOS (5), and Internet Explorer (4).

Of the 58 in-the-wild -times observed in 2021, 39 ended up memory corruption vulnerabilities, with the bugs stemming as a consequence of use-right after-no cost (17), out-of-bounds read and generate (6), buffer overflow (4), and integer overflow (4) flaws.
It can be also worthy of noting that 13 out of the 14 Chromium -days were being memory corruption vulnerabilities, most of which, in flip, were being use-just after-free of charge vulnerabilities.
What’s more, Google Challenge Zero pointed out the lack of public illustrations highlighting in-the-wild exploitation of zero-working day flaws in messaging services like WhatsApp, Sign, and Telegram as effectively as other parts, which include CPU cores, Wi-Fi chips, and the cloud.
“This qualified prospects to the concern of regardless of whether these -days are absent thanks to lack of detection, deficiency of disclosure, or equally?,” Stone said, incorporating, “As an market we are not creating -working day tricky.”
“-working day will be more challenging when, overall, attackers are not capable to use public strategies and approaches for building their -day exploits,” forcing them “to start out from scratch just about every time we detect a single of their exploits.”
Observed this write-up exciting? Adhere to THN on Facebook, Twitter and LinkedIn to read much more distinctive articles we post.
Some components of this article are sourced from:
thehackernews.com



 Google: 2021 was a Banner Year for Exploited 0-Day Bugs
Google: 2021 was a Banner Year for Exploited 0-Day Bugs