Google these days declared plans to implement assistance for passwordless logins in Android and the Chrome web browser to allow buyers to indication in throughout various equipment and internet websites irrespective of the platform.
“This will simplify indicator-ins throughout units, internet websites, and programs no make a difference the platform – with out the will need for a solitary password,” Google reported.
Apple and Microsoft are also envisioned to extend the guidance to iOS, macOS, and Windows functioning units as well as Safari and Edge browsers.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
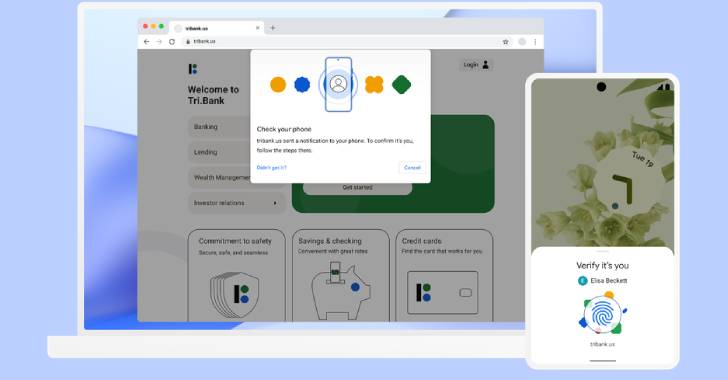
The new Rapidly Id On the web (FIDO) indicator-in procedure does absent with passwords totally in favor of exhibiting a prompt asking a consumer to unlock the phone when signing into a website or an software.
This is built achievable by storing a cryptographically secured FIDO credential called a passkey on the phone that’s used to log in to the online account after unlocking the device.
“As soon as you have done this, you would not need your phone once more and you can indicator-in by just unlocking your laptop,” Google stated.
“Even if you eliminate your phone, your passkeys will securely sync to your new phone from cloud backup, letting you to pick up appropriate where your aged machine still left off.”
In a way, the strategy can be seen as an extension of its individual Google prompts for logging into accounts secured with two-factor authentication (aka 2-Action Verification).
The advancement will come as code hosting system GitHub declared that it will “involve all users who contribute code on GitHub.com to empower one particular or much more sorts of two-factor authentication (2FA) by the stop of 2023” to avert account takeover attacks.
Observed this short article interesting? Follow THN on Facebook, Twitter and LinkedIn to read far more exclusive content material we write-up.
Some parts of this report are sourced from:
thehackernews.com

 Latest Cohort Announced for NCSC For Startups
Latest Cohort Announced for NCSC For Startups