The Gootkit malware is prominently heading immediately after health care and finance businesses in the U.S., U.K., and Australia, in accordance to new results from Cybereason.
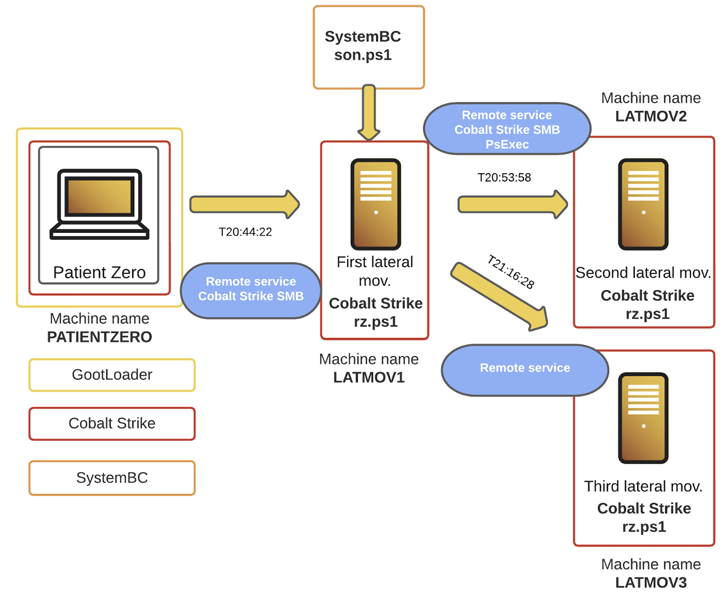
The cybersecurity company stated it investigated a Gootkit incident in December 2022 that adopted a new approach of deployment, with the actors abusing the foothold to produce Cobalt Strike and SystemBC for write-up-exploitation.
“The menace actor shown quickly-moving behaviors, rapidly heading to handle the network it infected, and receiving elevated privileges in significantly less than 4 hours,” Cybereason reported in an assessment posted February 8, 2023.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
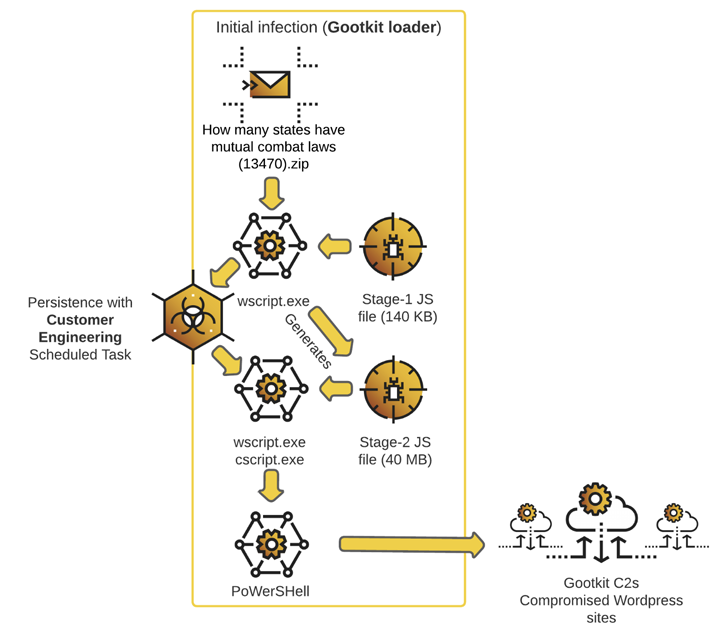
Gootkit, also known as Gootloader, is completely attributed to a risk actor tracked by Mandiant as UNC2565. Setting up its life in 2014 as a banking trojan, the malware has due to the fact morphed into a loader capable of providing subsequent-phase payloads.
The change in techniques was very first uncovered by Sophos in March 2021. Gootloader usually takes the kind of seriously-obfuscated JavaScript data files that are served through compromised WordPress web-sites rated greater in lookup motor effects by poisoning strategies.
The attack chain relies on luring victims looking for agreements and contracts on DuckDuckGo and Google to the booby-trapped web site, ultimately foremost to the deployment of Gootloader.
The hottest wave is also noteworthy for concealing the destructive code inside of legit JavaScript libraries these as jQuery, Chroma.js, Sizzle.js, and Underscore.js, which is then applied to spawn a secondary 40 MB JavaScript payload that establishes persistence and launches the malware.
In the incident examined by Cybereason, the Gootloader infection is claimed to have paved the way for Cobalt Strike and SystemBC to perform lateral motion and attainable info exfiltration. The attack was in the long run foiled.
The disclosure will come amid the ongoing development of abusing Google Ads by malware operators as an intrusion vector to distribute a wide variety of malware this sort of as FormBook, IcedID, RedLine, Rhadamanthys, and Vidar.
The evolution of Gootloader into a innovative loader is further more reflective of how danger actors are frequently trying to get new targets and approaches to improve their gains by pivoting to a malware-as-a-assistance (MaaS) model and providing that access to other criminals.
Located this article fascinating? Stick to us on Twitter and LinkedIn to go through a lot more unique content we post.
Some components of this posting are sourced from:
thehackernews.com

 Trio Arrested in COVID PPE Fraud Probe
Trio Arrested in COVID PPE Fraud Probe