Vulnerable internet-experiencing Microsoft SQL (MS SQL) Servers are becoming targeted by danger actors as component of a new campaign to deploy the Cobalt Strike adversary simulation tool on compromised hosts.
“Attacks that concentrate on MS SQL servers involve attacks to the surroundings the place its vulnerability has not been patched, brute forcing, and dictionary attack in opposition to inadequately managed servers,” South Korean cybersecurity company AhnLab Security Crisis Reaction Middle (ASEC) explained in a report printed Monday.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
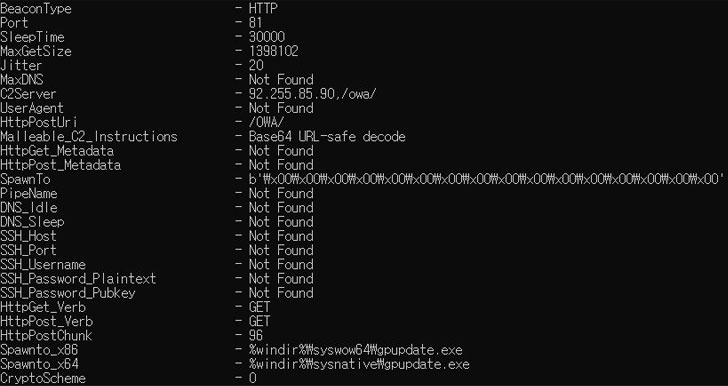
Cobalt Strike is a professional, entire-showcased penetration screening framework that makes it possible for an attacker to deploy an agent named “Beacon” on the sufferer machine, granting the operator remote obtain to the system. While billed as a red staff risk simulation system, cracked variations of the software package have been actively applied by a huge vary of threat actors.
Intrusions observed by ASEC include the unidentified actor scanning port 1433 to examine for exposed MS SQL servers to execute brute force or dictionary attacks in opposition to the procedure administrator account, i.e., “sa” account, to attempt a log in.
That’s not to say that servers not still left available more than the internet are not vulnerable, what with the threat actor guiding LemonDuck malware scanning the similar port to laterally move throughout the network.
“Controlling admin account credentials so that they are susceptible to brute forcing and dictionary attacks as earlier mentioned or failing to modify the credentials periodically may perhaps make the MS-SQL server the principal goal of attackers,” the researchers reported.
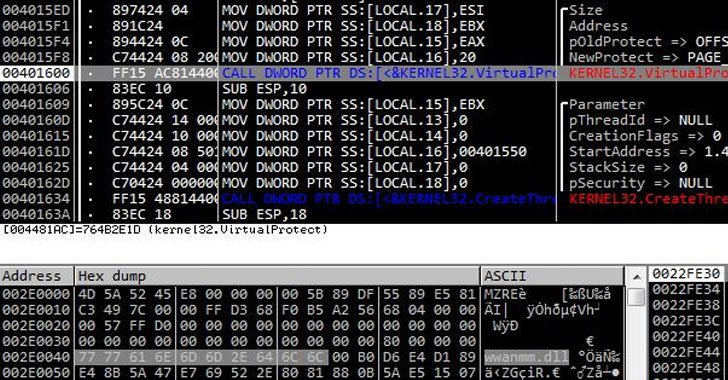
Upon productively getting a foothold, the upcoming period of the attack functions by spawning a Windows command shell via the MS SQL “sqlservr.exe” method to download the upcoming-stage payload that residences the encoded Cobalt Strike binary on to the program.
The attacks eventually culminate with the malware decoding the Cobalt Strike executable, followed by injecting it into the respectable Microsoft Make Motor (MSBuild) method, which has been formerly abused by malicious actors to filelessly produce remote entry trojans and password-stealing malware on targeted Windows programs.
Furthermore, the Cobalt Strike that is executed in MSBuild.exe will come with more configurations to evade detection of security computer software. It achieves this by loading “wwanmm.dll,” a Windows library for WWan Media Supervisor, then writing and working the Beacon in the memory spot of the DLL.
“As the beacon that gets the attacker’s command and performs the malicious behavior does not exist in a suspicious memory space and alternatively operates in the ordinary module wwanmm.dll, it can bypass memory-based mostly detection,” the researchers pointed out.
Discovered this posting attention-grabbing? Observe THN on Fb, Twitter and LinkedIn to study much more distinctive articles we submit.
Some areas of this post are sourced from:
thehackernews.com


 Teen Framed for Cybercrime Files Lawsuit
Teen Framed for Cybercrime Files Lawsuit