New investigation has uncovered that it is possible for menace actors to abuse a legitimate characteristic in GitHub Codespaces to deliver malware to victim programs.
GitHub Codespaces is a cloud-dependent configurable growth ecosystem that will allow buyers to debug, manage, and commit variations to a given codebase from a web browser or via an integration in Visual Studio Code.
It also will come with a port forwarding attribute that can make it doable to accessibility a web software that is operating on a certain port inside the codespace instantly from the browser on a area equipment for screening and debugging uses.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“You can also forward a port manually, label forwarded ports, share forwarded ports with associates of your organization, share forwarded ports publicly, and insert forwarded ports to the codespace configuration,” GitHub clarifies in its documentation.
It is really critical to be aware right here that any forwarded port that is created community will also permit any party with information of the URL and port selection to view the jogging software sans any authentication.
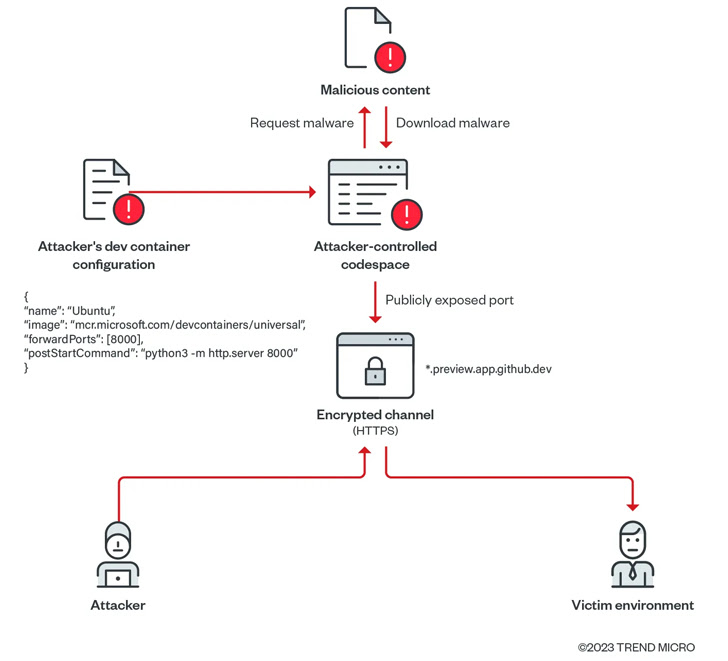
GitHub Codespaces takes advantage of HTTP for port forwarding. Need to the publicly seen port be updated to use HTTPS or eradicated and re-included, the port’s visibility is routinely modified to personal.
Cybersecurity company Development Micro uncovered that these types of publicly-shared forwarded ports could be exploited to create a malicious file server applying a GitHub account.
“In the method, these abused environments will not be flagged as malicious or suspicious even as it serves malicious written content (these as scripts, malware, and ransomware, amid other individuals), and businesses could take into consideration these gatherings as benign or fake positives,” scientists Nitesh Surana and Magno Logan claimed.
In a proof-of-thought (PoC) exploit shown by Craze Micro, a threat actor could create a codespace and obtain malware from an attacker-controlled domain to the ecosystem, and established the visibility of the forwarded port to general public, fundamentally reworking the software to act as a web server hosting rogue payloads.
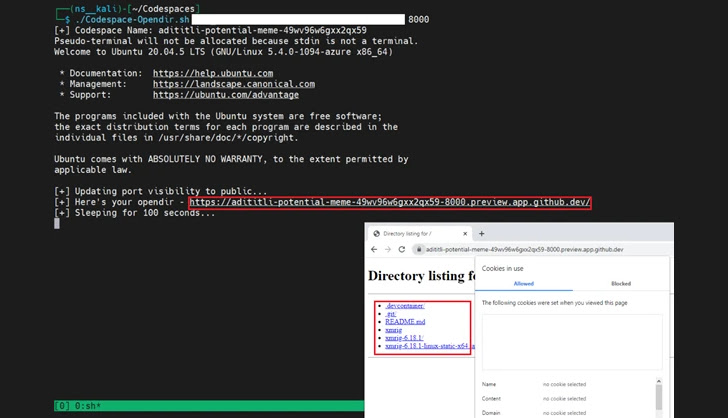
Even extra troublingly, the adversary can increase this technique to deploy malware and compromise a victim’s natural environment considering that each codespace domain related with the uncovered port is exclusive and unlikely to be flagged by security resources as a malicious domain.
“Utilizing this sort of scripts, attackers can very easily abuse GitHub Codespaces in serving destructive information at a immediate amount by exposing ports publicly on their codespace environments,” the scientists defined.
When the strategy is yet to be observed in the wild, the conclusions are a reminder as to how menace actors could weaponize cloud platforms to their gain and carry out an array of illicit actions.
“Cloud companies offer rewards to genuine consumers and attackers alike,” the scientists concluded. “The features offered to genuine subscribers also become readily available to menace actors as they just take advantage of the sources furnished by the [cloud service provider].”
Found this post interesting? Observe us on Twitter and LinkedIn to go through a lot more special written content we put up.
Some elements of this posting are sourced from:
thehackernews.com


 4 Places to Supercharge Your SOC with Automation
4 Places to Supercharge Your SOC with Automation