In what is actually a new phishing strategy, it has been shown that the Software Method aspect in Chromium-based mostly web browsers can be abused to generate “sensible desktop phishing applications.”
Application Manner is developed to provide native-like experiences in a fashion that leads to the web site to be introduced in a independent browser window, when also exhibiting the website’s favicon and hiding the tackle bar.
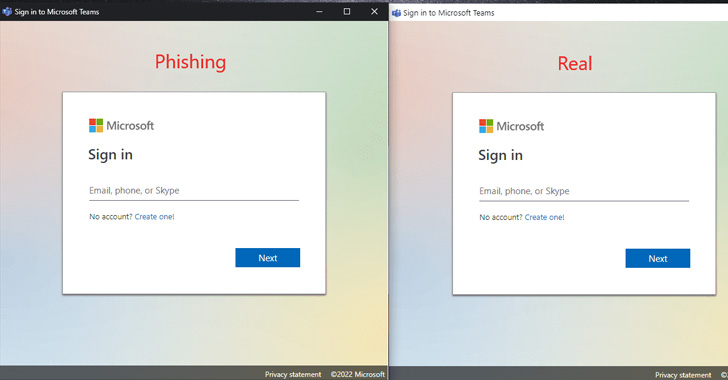
According to security researcher mr.d0x – who also devised the browser-in-the-browser (BitB) attack strategy previously this 12 months – a poor actor can leverage this behavior to vacation resort to some HTML/CSS trickery and show a fake address bar on top rated of the window and fool customers into providing up their credentials on rogue login kinds.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“Even though this technique is meant more to interior phishing, you can technically even now use it in an exterior phishing circumstance,” mr.d0x mentioned. “You can provide these faux apps independently as data files.”
This is accomplished by environment up a phishing web site with a fake deal with bar at the major, and configuring the –app parameter to level to the phishing site hosting the web site.
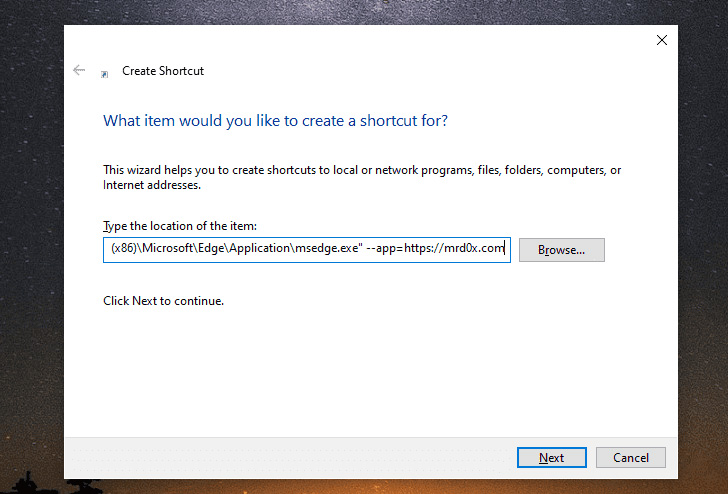
On top rated of that, the attacker-managed phishing web site can make use of JavaScript to get a lot more steps, these types of as closing the window quickly right after the consumer enters the qualifications or resizing and positioning it to obtain the wanted impact.
It can be value noting that the system performs on other running programs, these as macOS and Linux, producing it a opportunity cross-platform menace. Even so, the accomplishment of the attack is predicated on the truth that the attacker currently has entry to the target’s device.

That reported, Google is phasing out help for Chrome apps in favor of Progressive Web Applications (PWAs) and web-standard technologies, and the aspect is envisioned to be totally discontinued in Chrome 109 or later on on Windows, macOS, and Linux.
The results appear as new results Trustwave SpiderLabs clearly show that HTML smuggling attacks are a frequent event, with .HTML (11.39%) and .HTM (2.7%) data files accounting for the next most spammed file attachment kind following .JPG photos (25.29%).
Discovered this report fascinating? Abide by THN on Fb, Twitter and LinkedIn to study much more exceptional content we publish.
Some components of this article are sourced from:
thehackernews.com

 Hacker Steals Over $570m from Binance Bridge
Hacker Steals Over $570m from Binance Bridge