A risk actor, likely Chinese in origin, is actively making an attempt to exploit a zero-working day vulnerability in the Zimbra open-source email system as component of spear-phishing campaigns that commenced in December 2021.
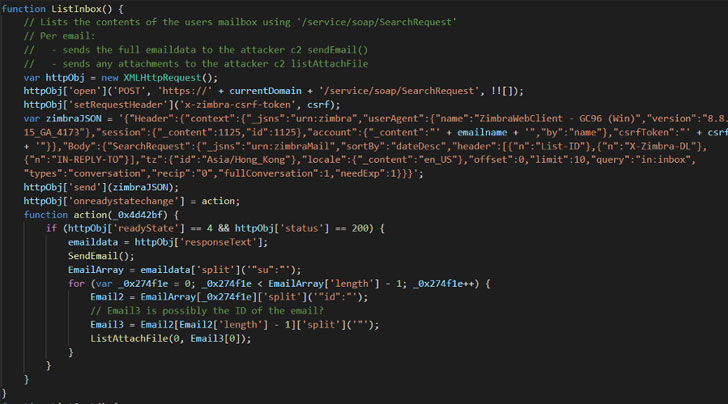
The espionage operation — codenamed “EmailThief” — was in depth by cybersecurity enterprise Volexity in a technical report published Thursday, noting that profitable exploitation of the cross-internet site scripting (XSS) vulnerability could outcome in the execution of arbitrary JavaScript code in the context of the user’s Zimbra session.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
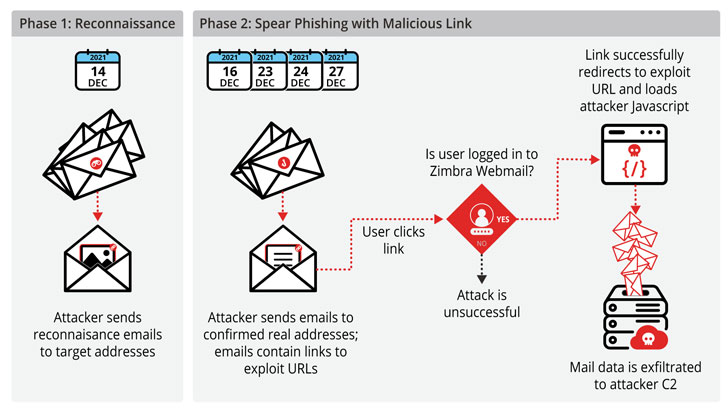
Volexity attributed the intrusions, which commenced on December 14, 2021, to a beforehand undocumented hacking group it is really tracking beneath the moniker TEMP_HERETIC, with the assaults aimed at European government and media entities. The zero-day bug impacts the most the latest open up-resource version of Zimbra operating edition 8.8.15.
The attacks are thought to have happened in two phases the 1st phase aimed at reconnaissance and distributing emails made to retain tabs if a concentrate on obtained and opened the messages. In the subsequent phase, numerous waves of email messages were broadcasted to trick the recipients into clicking a destructive website link.
“For the attack to be productive, the focus on would have to visit the attacker’s backlink whilst logged into the Zimbra webmail client from a web browser,” Steven Adair and Thomas Lancaster pointed out. “The url alone, on the other hand, could be launched from an application to consist of a thick client, such as Thunderbird or Outlook.”
The unpatched flaw, should really it be weaponized, could be abused to exfiltrate cookies to let persistent accessibility to a mailbox, send phishing messages from the compromised email account to widen the an infection, and even aid the down load of more malware.
“None of the infrastructure identified […] particularly matches infrastructure used by formerly classified risk teams,” the scientists mentioned. “Even so, centered on the focused firm and particular men and women of the qualified firm, and given the stolen details would have no monetary value, it is very likely the attacks had been undertaken by a Chinese APT actor.”
“End users of Zimbra should really contemplate upgrading to model 9.., as there is now no protected edition of 8.8.15,” the organization extra.
Uncovered this posting exciting? Comply with THN on Facebook, Twitter and LinkedIn to browse much more special content we article.
Some components of this posting are sourced from:
thehackernews.com



 Kronos Still Dragging Itself Back From Ransomware Hell
Kronos Still Dragging Itself Back From Ransomware Hell