Cybersecurity researchers on Tuesday took the wraps off a multi-stage espionage marketing campaign targeting large-ranking authorities officials overseeing countrywide security policy and people in the protection sector in Western Asia.
The attack is special as it leverages Microsoft OneDrive as a command-and-command (C2) server and is split into as a lot of as 6 stages to keep as hidden as attainable, Trellix, a new enterprise developed next the merger of security firms McAfee Business and FireEye, stated in a report shared with The Hacker News.
Very first indications of action related with the covert procedure are reported to have commenced as early as June 18, 2021, with two victims noted on September 21 and 29, followed by 17 a lot more in a limited span of 3 days involving Oct 6 and 8.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Trellix attributed the attacks with reasonable self-confidence to the Russia-dependent APT28 group, the risk actor at the rear of the compromise of SolarWinds in 2020, based on similarities in the source code as properly as in the attack indicators and geopolitical objectives.
“We are supremely self-confident that we are working with a extremely competent actor centered on how infrastructure, malware coding and procedure had been set up,” Trellix security researcher Marc Elias explained.
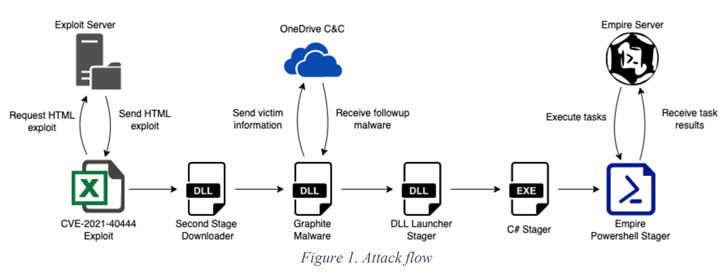
The infection chain begins with the execution of a Microsoft Excel file that contains an exploit for the MSHTML distant code execution vulnerability (CVE-2021-40444), which is made use of to run a destructive binary that functions as the downloader for a third-stage malware dubbed Graphite.
The DLL executable makes use of OneDrive as the C2 server by means of the Microsoft Graph API to retrieve more stager malware that in the end downloads and executes Empire, an open-source PowerShell-based mostly publish-exploitation framework extensively abused by menace actors for abide by-on activities.
If anything at all, the growth marks the ongoing exploitation of the MSTHML rendering motor flaw, with Microsoft and SafeBreach Labs disclosing a number of campaigns that have weaponized the vulnerability to plant malware and distribute personalized Cobalt Strike Beacon loaders.
Found this posting attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to read extra unique material we write-up.
Some parts of this article are sourced from:
thehackernews.com



 BRATA Android Trojan Updated with ‘Kill Switch’ that Wipes Devices
BRATA Android Trojan Updated with ‘Kill Switch’ that Wipes Devices