The North Korea-backed Lazarus Team has been noticed leveraging the Log4Shell vulnerability in VMware Horizon servers to deploy the NukeSped (aka Manuscrypt) implant towards targets found in its southern counterpart.
“The attacker employed the Log4j vulnerability on VMware Horizon items that ended up not utilized with the security patch,” AhnLab Security Emergency Response Center (ASEC) mentioned in a new report.
The intrusions are reported to have been 1st found in April, even though many risk actors, such as these aligned with China and Iran, have employed the identical approach to additional their goals above the past handful of months.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
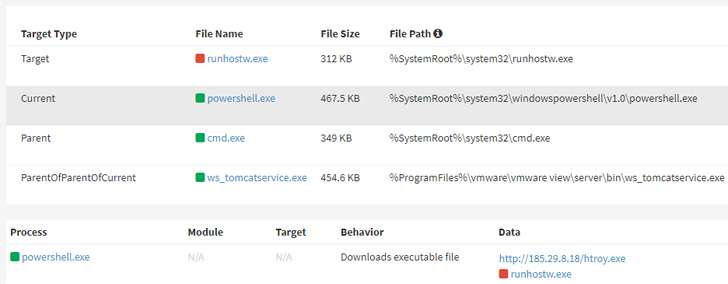
NukeSped is a backdoor that can complete a variety of destructive activities based on commands acquired from a remote attacker-controlled area. Past 12 months, Kaspersky disclosed a spear-phishing campaign aimed at thieving critical data from protection companies using a NukeSped variant identified as ThreatNeedle.
Some of the vital functions of the backdoor assortment from capturing keystrokes and getting screenshots to accessing the device’s webcam and dropping supplemental payloads these types of as information and facts stealers.

The stealer malware, a console-based mostly utility, is developed to exfiltrate accounts and passwords saved in web browsers like Google Chrome, Mozilla Firefox, Internet Explorer, Opera, and Naver Whale as properly as facts about email accounts and just lately opened Microsoft Office and Hancom information.
“The attacker collected supplemental data by utilizing backdoor malware NukeSped to mail command line instructions,” the scientists stated. “The gathered info can be utilized later on in lateral motion attacks.”
Uncovered this post intriguing? Abide by THN on Fb, Twitter and LinkedIn to read through far more distinctive articles we publish.
Some elements of this write-up are sourced from:
thehackernews.com


 QNAP NAS drives targeted by DeadBolt ransomware for the third time this year
QNAP NAS drives targeted by DeadBolt ransomware for the third time this year