A new email phishing marketing campaign has been spotted leveraging the tactic of conversation hijacking to supply the IceID information-thieving malware onto infected equipment by building use of unpatched and publicly-uncovered Microsoft Exchange servers.
“The email messages use a social engineering method of dialogue hijacking (also recognised as thread hijacking),” Israeli firm Intezer stated in a report shared with The Hacker Information. “A solid reply to a preceding stolen email is being utilised as a way to influence the receiver to open the attachment. This is noteworthy because it raises the reliability of the phishing email and might cause a substantial an infection price.”
The newest wave of attacks, detected in mid-March 2022, is claimed to have specific businesses within just energy, healthcare, regulation, and pharmaceutical sectors.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
IceID, aka BokBot, like its counterparts TrickBot and Emotet, is a banking trojan that has advanced to grow to be an entry issue for extra refined threats, like human-operated ransomware and the Cobalt Strike adversary simulation resource.
It’s able of connecting to a remote server and downloading future-phase implants and applications that enable attackers to carry out stick to-on things to do and transfer laterally across impacted networks to distribute added malware.
In June 2021, company security company Proofpoint disclosed an evolving tactic in the cybercrime landscape whereby initial obtain brokers had been noticed infiltrating goal networks by using initially-stage malware payloads these as IcedID to deploy Egregor, Maze, and REvil ransomware payloads.
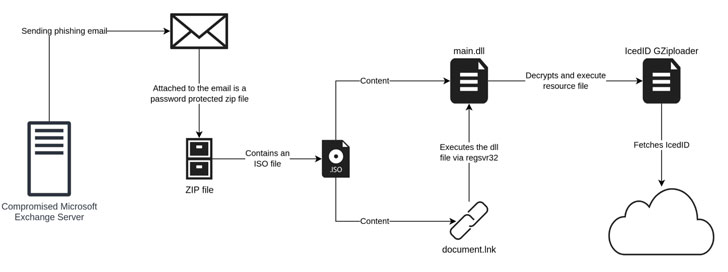
Although earlier IcedID campaigns have taken benefit of internet site speak to types to send malware-laced inbound links to corporations, the existing edition of the attacks lender on vulnerable Microsoft Trade servers to send out the entice emails from a hijacked account, indicating a even further evolution of the social engineering plan.
“The payload has also moved absent from working with Office documents to the use of ISO documents with a Windows LNK file and a DLL file,” scientists Joakim Kennedy and Ryan Robinson claimed. “The use of ISO data files enables the danger actor to bypass the Mark-of-the-Web controls, resulting in execution of the malware without the need of warning to the user.”
The strategy is to send out fraudulent replies to an currently existing email thread plundered from the victim’s account by working with the compromised individual’s email handle to make the phishing email messages show up far more legit.
“The use of dialogue hijacking is a strong social engineering approach that can boost the rate of a thriving phishing attempt,” the scientists concluded. “By applying this method, the email seems additional legit and is transported by the ordinary channels which can also contain security products and solutions.”
Discovered this article exciting? Observe THN on Fb, Twitter and LinkedIn to browse much more exclusive content material we article.
Some areas of this posting are sourced from:
thehackernews.com




 Of Cybercriminals and IP Addresses
Of Cybercriminals and IP Addresses