Cybersecurity scientists are calling notice to a totally free-to-use browser automation framework that is currently being increasingly made use of by menace actors as element of their attack campaigns.
“The framework includes many features which we evaluate may be utilized in the enablement of destructive actions,” scientists from Crew Cymru reported in a new report revealed Wednesday.
“The technical entry bar for the framework is purposefully stored reduced, which has served to produce an energetic community of content builders and contributors, with actors in the underground economic system marketing their time for the generation of bespoke tooling.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

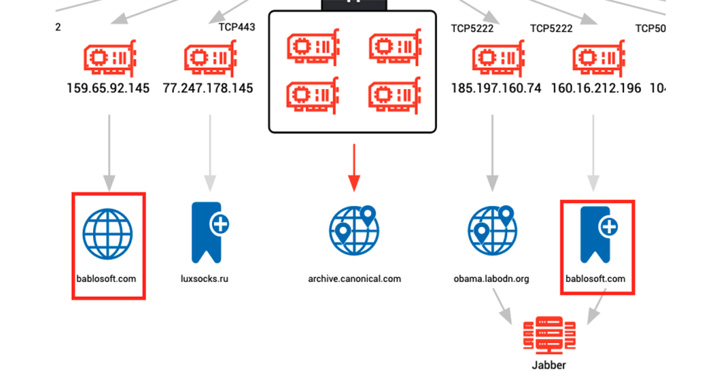
The U.S. cybersecurity company mentioned it observed command-and-command (C2) IP addresses related with malware this kind of as Bumblebee, BlackGuard, and RedLine Stealer setting up connections to the downloads subdomain of Bablosoft (“downloads.bablosoft[.]com”), the maker of the Browser Automation Studio (BAS).
Bablosoft was formerly documented by cloud security and software shipping and delivery organization F5 in February 2021, pointing to the framework’s ability to automate jobs in Google’s Chrome browser in a fashion similar to reputable developer applications like Puppeteer and Selenium.
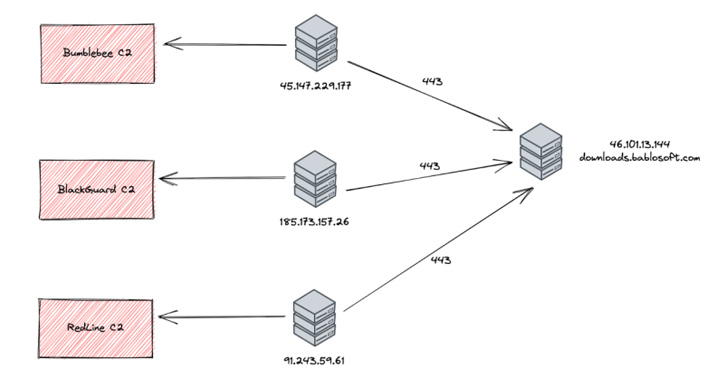
Menace telemetry for the subdomain’s IP address — 46.101.13[.]144 — reveals that a wide bulk of action is originating from locations in Russia and Ukraine, with open supply intelligence indicating that Bablosoft’s operator is allegedly based in the Ukrainian funds town of Kyiv.

It is currently being suspected that the operators of the malware campaigns connected to the Bablosoft subdomain for functions of downloading added applications for use as element of write-up-exploitation routines.
Also determined are a number of hosts affiliated with cryptojacking malware like XMRig and Tofsee speaking with a next subdomain named “fingerprints.bablosoft[.]com” to use a provider that aids the mining malware conceal its behavior.
“Centered on the selection of actors already employing equipment available on the Bablosoft site, we can only anticipate to see BAS getting a far more prevalent factor of the menace actor’s toolkit,” the scientists mentioned.
Identified this post appealing? Adhere to THN on Facebook, Twitter and LinkedIn to read extra exclusive written content we publish.
Some areas of this write-up are sourced from:
thehackernews.com