The Uyghur group found in China and Pakistan has been the issue of an ongoing espionage marketing campaign aiming to trick the targets into downloading a Windows backdoor to amass sensitive info from their units.
“Significant effort and hard work was place into disguising the payloads, irrespective of whether by building supply documents that appear to be originating from the United Nations applying up to day related themes, or by location up internet sites for non-present organizations declaring to fund charity groups,” according to joint research printed by Check Place Investigate and Kaspersky today.
The Uyghurs are a Turkic ethnic minority group originating from Central and East Asia and are identified as native to the Xinjiang Uyghur Autonomous Region in Northwest China. At the very least considering the fact that 2015, government authorities have positioned the location under tight surveillance, placing hundreds of thousands into prisons and internment camps that the govt calls “Vocational Schooling and Training Centers.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Over the yrs, the neighborhood has also been at the obtaining stop of a series of sustained cyberattacks that have leveraged exploit chains and watering holes to install spyware intended to harvest and exfiltrate delicate details from email and messaging apps as nicely as plunder photos and login credentials.

Previously this March, Facebook disclosed that it disrupted a network of terrible actors using its system to concentrate on the Uyghur group and entice them into downloading malicious software program that would allow for surveillance of their products, attributing the “persistent procedure” to a China-centered threat actor acknowledged as Evil Eye.
The newest cyber offensive follows a equivalent modus operandi in that the attacks contain sending UN-themed decoy documents (“UgyhurApplicationList.docx”) to the targets underneath the pretext of talking about human rights violations. The purpose of the phishing concept is to lure the recipients into putting in a backdoor on the Windows devices.
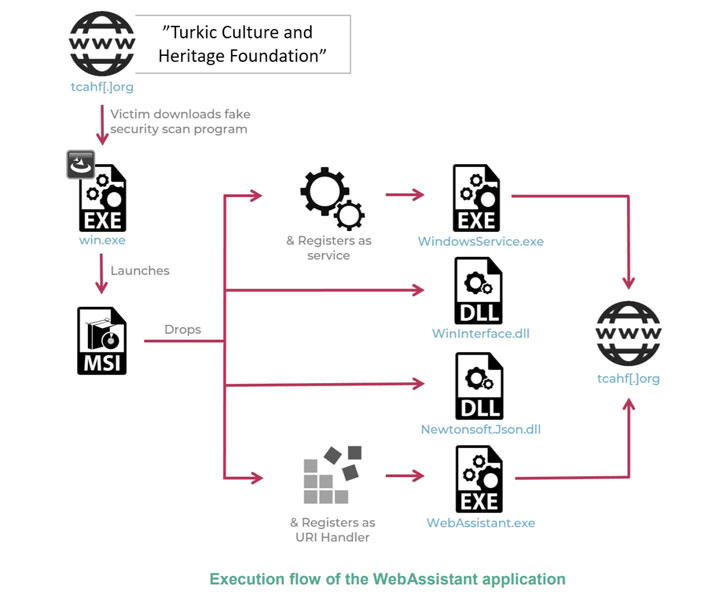
In an different an infection vector observed by the scientists, a bogus human rights basis identified as the “Turkic Tradition and Heritage Foundation” (“tcahf[.]org”) — with its written content copied from George Soros-launched Open up Society Foundations — was utilised as a bait to down load a .NET backdoor that purports to be a security scanner, only to hook up to a remote server and transmit the gathered knowledge, which incorporates procedure metadata and a listing of installed applications and operating procedures.
“The malicious performance of the TCAHF site is properly disguised and only seems when the sufferer tries to implement for a grant,” the researchers claimed. “The web-site then claims it will have to make certain the functioning procedure is safe before coming into delicate information for the transaction, and therefore asks the victims to download a software to scan their environments.”
At least two distinct versions of the Windows implants have been detected to day, just one called “WebAssistant” that was out there for obtain from the rogue website in May 2020 and a next variant dubbed “TcahfUpdate” that was readily available in October 2020.
The two cybersecurity firms did not attribute the attacks to a acknowledged threat team but pinned the intrusions on a Chinese-speaking adversary with reduced to medium self-assurance centered on overlaps in the VBA code embedded in the Phrase document. Only a handful of victims in China and Pakistan have been discovered so much, dependent on telemetry information compiled during the evaluation.
Unsurprisingly, the attackers driving the marketing campaign continue on to keep on being lively and evolve its infrastructure, with the group registering two new domains in 2021, both equally of which redirect to the site of a Malaysian federal government entire body referred to as the “Terengganu Islamic Basis,” suggesting the risk actor may possibly have set its sights on targets in Malaysia and Turkey.
“We consider that these cyber-attacks are enthusiastic by espionage, with the conclude-activity of the procedure remaining the set up of a backdoor into the desktops of higher-profile targets in the Uyghur group,” claimed Lotem Finkelsteen, Test Point’s head of danger intelligence. “The attacks are developed to fingerprint infected gadgets … [and] from what we can notify, these attacks are ongoing, and new infrastructure is currently being designed for what seems to be like long run attacks.”
Uncovered this write-up attention-grabbing? Stick to THN on Facebook, Twitter and LinkedIn to go through more exceptional written content we submit.
Some elements of this report are sourced from:
thehackernews.com


 DHS issues cyber order to pipeline operators in first move to regulate critical infrastructure sectors
DHS issues cyber order to pipeline operators in first move to regulate critical infrastructure sectors