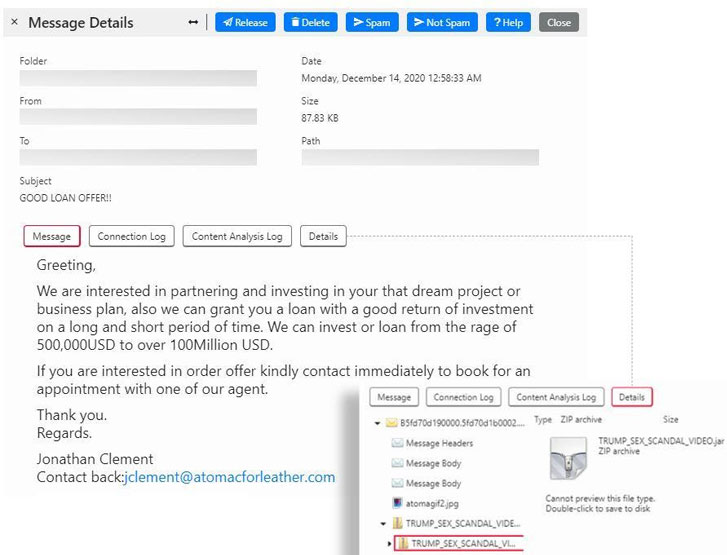
Cybesecurity researchers currently unveiled a new malspam marketing campaign that distributes a distant access Trojan (RAT) by purporting to have a intercourse scandal video of U.S. President Donald Trump.
The e-mail, which carry with the subject matter line “Great Personal loan Offer you!!,” arrive connected with a Java archive (JAR) file named “TRUMP_Sexual intercourse_SCANDAL_Online video.jar,” which, when downloaded, installs Qua or Quaverse RAT (QRAT) onto the infiltrated method.
“We suspect that the poor guys are attempting to trip the frenzy brought about by the recently concluded Presidential elections since the filename they used on the attachment is absolutely unrelated to the email’s concept,” Trustwave’s Senior Security Researcher Diana Lopera reported in a create-up posted now.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The newest campaign is a variant of the Windows-based QRAT downloader Trustwave researchers discovered in August.
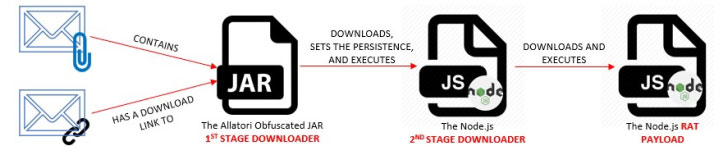
The infection chain starts with a spam concept made up of an embedded attachment or a website link pointing to a destructive zip file, possibly of which retrieves a JAR file (“Spec#0034.jar”) that’s scrambled using the Allatori Java obfuscator.
This to start with stage downloader sets up the Node.Js system onto the technique and then downloads and executes a 2nd-stage downloader called “wizard.js” that is accountable for acquiring persistence and fetching and running the Qnode RAT (“qnode-win32-ia32.js”) from an attacker-controlled server.
QRAT is a common remote accessibility Trojan with several attributes together with, acquiring process info, performing file functions, and acquiring qualifications from purposes this kind of as Google Chrome, Firefox, Thunderbird, and Microsoft Outlook.
What is improved this time about is the inclusion of a new pop-up inform that informs the victim that the JAR becoming operate is a distant access program applied for penetration tests. This also usually means the sample’s destructive habits only starts to manifest at the time the person clicks the “Alright, I know what I am doing.” button.
“This pop-up is a small odd and is most likely an try to make the software glimpse genuine, or deflect accountability from the primary software package authors,” Lopera famous.
Also, the malicious code of the JAR downloader is break up-up into unique randomly-numbered buffers in an try to evade detection.
Other alterations consist of an total raise in the JAR file sizing and the elimination of the second-phase downloader in favor of an up-to-date malware chain that immediately fetches the QRAT payload now named “boot.js.”
For its section, the RAT has been given its possess share of updates, with the code now encrypted with base64 encoding, in addition to getting cost of persisting on the concentrate on technique by way of a VBS script.
“This danger has been noticeably increased around the earlier number of months because we initial examined it,” Topera concluded, urging administrators to block the incoming JARs in their email security gateways.
“Whilst the attachment payload has some advancements more than previous versions, the email marketing campaign alone was rather amateurish, and we feel that the probability this menace will be delivered successfully is bigger if only the email was much more refined.”
Discovered this article appealing? Abide by THN on Fb, Twitter and LinkedIn to read through extra distinctive content material we article.
Some areas of this report are sourced from:
thehackernews.com


 BlueVoyant Enters Strategic Partnership with Third Party Risk Management Consultancy
BlueVoyant Enters Strategic Partnership with Third Party Risk Management Consultancy