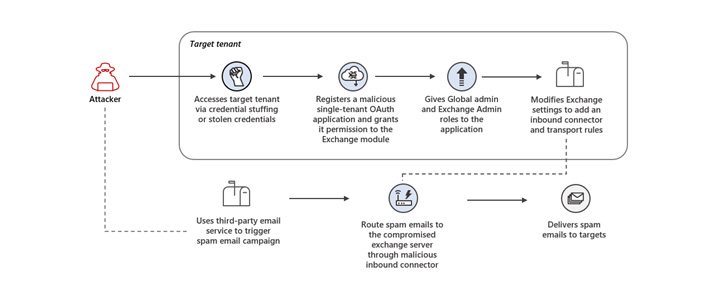
Microsoft on Thursday warned of a consumer-facing attack that manufactured use of rogue OAuth purposes on compromised cloud tenants to in the end seize handle of Exchange servers and unfold spam.
“The danger actor released credential stuffing attacks in opposition to higher-risk accounts that didn’t have multi-factor authentication (MFA) enabled and leveraged the unsecured administrator accounts to gain initial accessibility,” the Microsoft 365 Defender Exploration Crew claimed.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The unauthorized entry to the cloud tenant permitted the adversary to sign-up a malicious OAuth application and grant it elevated permissions, and ultimately modify Trade Server settings to make it possible for inbound e-mails from particular IP addresses to be routed by the compromised email server.
“These modifications to the Trade server settings permitted the menace actor to accomplish their primary intention in the attack: sending out spam emails,” Microsoft mentioned. “The spam email messages ended up sent as portion of a misleading sweepstakes scheme meant to trick recipients into signing up for recurring compensated subscriptions.”
The email messages urged the recipients to click on a link to obtain a prize, carrying out so which redirected the victims to a landing website page that questioned the victims to enter their credit rating card information for a smaller shipping and delivery fee to obtain the reward.
The threat actor further carried out a selection of ways to evade detection and carry on its functions for extended periods of time, together with employing the malicious OAuth application weeks or even months right after it was deployed and deleting the modifications produced to the Trade Server right after each individual spam marketing campaign.

Microsoft’s risk intelligence division reported that the adversary has been actively running spam email strategies for numerous years, ordinarily sending higher volumes of spam emails in short bursts by a variety of solutions.
While the primary aim of the attack seems to be to trick unwitting customers into signing up for undesired subscription products and services, it could have posed a far far more really serious risk experienced the same method been made use of to steal credentials or distribute malware.
“When the abide by-on spam marketing campaign targets shopper email accounts, this attack targets enterprise tenants to use as infrastructure for this marketing campaign,” Microsoft reported. “This attack as a result exposes security weaknesses that could be used by other danger actors in attacks that could directly effect afflicted enterprises.”
Identified this post appealing? Observe THN on Facebook, Twitter and LinkedIn to go through extra distinctive information we put up.
Some sections of this posting are sourced from:
thehackernews.com


 Optus Hit By Cyber-Attack, Breach Affects Nearly 10 Million Customers
Optus Hit By Cyber-Attack, Breach Affects Nearly 10 Million Customers