A new, innovative phishing attack has been noticed providing the AsyncRAT trojan as element of a malware campaign that is considered to have commenced in September 2021.
“By means of a basic email phishing tactic with an html attachment, risk attackers are offering AsyncRAT (a remote access trojan) developed to remotely keep an eye on and handle its infected pcs by way of a safe, encrypted link,” Michael Dereviashkin, security researcher at enterprise breach prevention company Morphisec, explained in a report.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The intrusions start with an email concept made up of an HTML attachment that is disguised as an get affirmation receipt (e.g., Receipt-
But not like other attacks that route the sufferer to a phishing domain set up explicitly for downloading the future-stage malware, the most current RAT campaign cleverly uses JavaScript to domestically make the ISO file from a Base64-encoded string and mimic the obtain process.
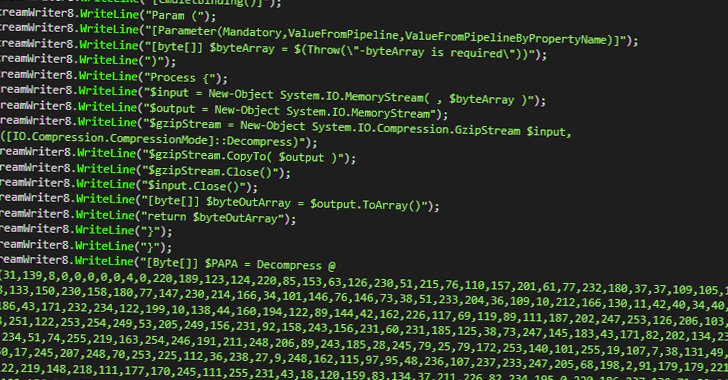
“The ISO obtain is not generated from a distant server but from in the victim’s browser by a JavaScript code that’s embedded inside the HTML receipt file,” Dereviashkin spelled out.
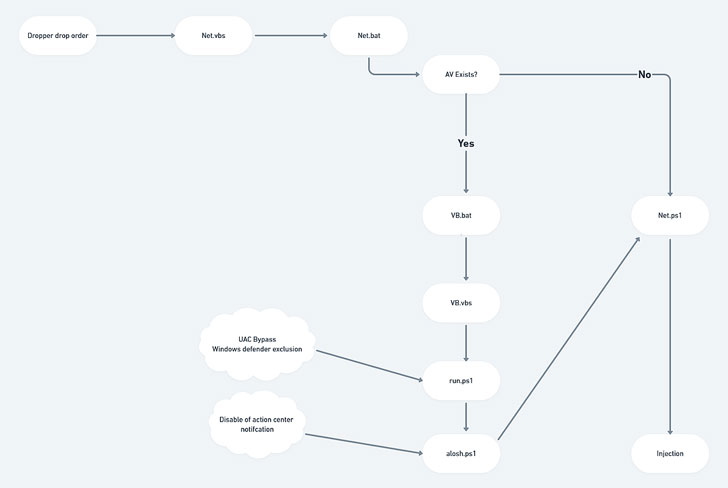
When the victim opens the ISO file, it is instantly mounted as a DVD Push on the Windows host and contains possibly a .BAT or a .VBS file, which proceeds the infection chain to retrieve a subsequent-stage ingredient by way of a PowerShell command execution.
This outcomes in the execution of a .NET module in-memory that subsequently acts as a dropper for 3 documents — one performing as a trigger for the up coming — to at last supply AsyncRAT as the last payload, whilst also checking for antivirus program and placing up Windows Defender exclusions.
RATs these kinds of as AsyncRAT are typically made use of to forge a distant website link amongst a threat actor and a target unit, steal facts, and perform surveillance by way of microphones and cameras. They present an array of innovative capabilities that give the attackers the potential to totally check and command the compromised equipment.
Morphisec also pointed out the campaign’s sophisticated practices, which it stated permitted the malware to slip by means of almost undetected by most antimalware engines inspite of the procedure currently being in effect for near to five months.
Uncovered this report interesting? Abide by THN on Fb, Twitter and LinkedIn to study much more exceptional information we publish.
Some areas of this write-up are sourced from:
thehackernews.com


 Apple Releases iOS and macOS Updates to Patch Actively Exploited 0-Day Vulnerability
Apple Releases iOS and macOS Updates to Patch Actively Exploited 0-Day Vulnerability