A fork out-for each-set up (PPI) malware company identified as PrivateLoader has been spotted distributing a “quite complex” framework called NetDooka, granting attackers entire handle over the contaminated products.
“The framework is distributed through a pay back-for each-put in (PPI) provider and consists of multiple components, which include a loader, a dropper, a safety driver, and a whole-featured distant obtain trojan (RAT) that implements its personal network communication protocol,” Trend Micro claimed in a report published Thursday.
PrivateLoader, as documented by Intel 471 in February 2022, features as a downloader liable for downloading and putting in added malware on to the contaminated procedure, together with SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
That includes anti-analysis approaches, PrivateLoader is published in the C++ programming language and is claimed to be in active improvement, with the downloader malware family attaining traction among various menace actors.
PrivateLoader bacterial infections are typically propagated by way of pirated software package downloaded from rogue websites that are pushed to the top of look for results through search motor optimization (Web optimization) poisoning tactics.
“PrivateLoader is at present utilised to distribute ransomware, stealer, banker, and other commodity malware,” Zscaler mentioned last week. “The loader will probably proceed to be up-to-date with new features and performance to evade detection and proficiently produce second-stage malware payloads.”
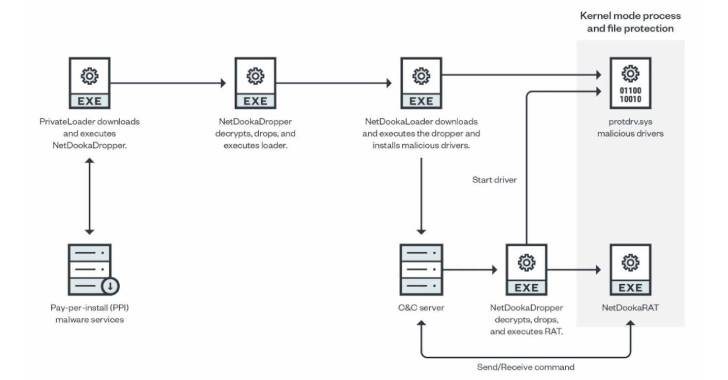
The framework, still in its progress section, contains distinct modules: a dropper, a loader, a kernel-mode method and file security driver, and a distant access trojan that takes advantage of a custom made protocol to connect with the command-and-command (C2) server.
The recently noticed established of bacterial infections involving the NetDooka framework commences with PrivateLoader performing as a conduit to deploy a dropper ingredient, which then decrypts and executes a loader that, in turn, retrieves an additional dropper from a distant server to install a full-featured trojan as effectively as a kernel driver.
“The driver component functions as a kernel-amount defense for the RAT element,” scientists Aliakbar Zahravi and Leandro Froes mentioned. “It does this by attempting to avert the file deletion and method termination of the RAT component.”
The backdoor, dubbed NetDookaRAT, is notable for its breadth of features, enabling it to operate instructions on the target’s unit, have out distributed denial-of-company (DDoS) attacks, accessibility and deliver documents, log keystrokes, and obtain and execute additional payloads.
This indicates that NetDooka’s capabilities not only allow for it to act as an entry position for other malware, but can also be weaponized to steal sensitive data and form remote-managed botnets.
“PPI malware services allow malware creators to quickly deploy their payloads,” Zahravi and Froes concluded.
“The use of a destructive driver produces a substantial attack floor for attackers to exploit, whilst also allowing for them to acquire edge of ways this sort of as preserving procedures and files, bypassing antivirus packages, and hiding the malware or its network communications from the method.”
Uncovered this article attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to go through far more exceptional information we article.
Some components of this short article are sourced from:
thehackernews.com

 Microsoft, Apple and Google Team Up on Passwordless Standard
Microsoft, Apple and Google Team Up on Passwordless Standard