A “persistent attacker group” with alleged ties to Hezbollah has retooled its malware arsenal with a new model of a distant entry Trojan (RAT) to break into businesses around the world and extract valuable details.
In a new report printed by the ClearSky investigate team on Thursday, the Israeli cybersecurity organization reported it discovered at least 250 general public-experiencing web servers because early 2020 that have been hacked by the danger actor to get intelligence and steal the company’s databases.
The orchestrated intrusions hit a slew of providers located in the U.S., the U.K., Egypt, Jordan, Lebanon, Saudi Arabia, Israel, and the Palestinian Authority, with a bulk of the victims symbolizing telecom operators (Etisalat, Mobily, Vodafone Egypt), internet assistance companies (SaudiNet, TE Knowledge), and hosting and infrastructure services companies (Secured Servers LLC, iomart).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Initial documented in 2015, Risky Cedar (or Lebanese Cedar) has been recognised to penetrate a large variety of targets working with various attack techniques, together with a personalized-manufactured malware implant codenamed Explosive.
Unstable Cedar has been previously suspected of Lebanese origins — specifically Hezbollah’s cyber device — in connection with a cyberespionage marketing campaign in 2015 that targeted armed service suppliers, telecom corporations, media stores, and universities.
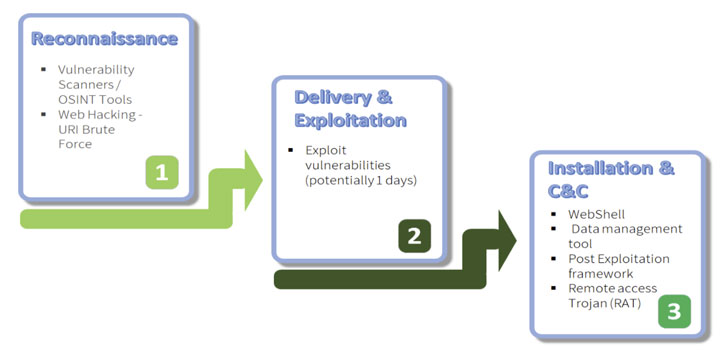
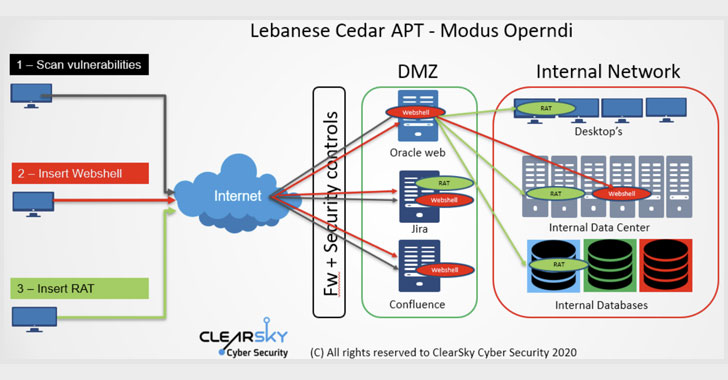
The 2020 attacks had been no diverse. The hacking action uncovered by ClearSky matched functions attributed to Hezbollah based mostly on code overlaps amongst the 2015 and 2020 variants of the Explosive RAT, which is deployed onto victims’ networks by exploiting acknowledged 1-day vulnerabilities in unpatched Oracle and Atlassian web servers.
Applying the 3 flaws in the servers (CVE-2019-3396, CVE-2019-11581, and CVE-2012-3152) as an attack vector to achieve an original foothold, the attackers then injected a web shell and a JSP file browser, equally of which were utilized to transfer laterally throughout the network, fetch supplemental malware, and download the Explosive RAT, which comes with capabilities to file keystrokes, capture screenshots, and execute arbitrary commands.
“The web shell is applied to carry out different espionage operations around the attacked web server, such as opportunity asset locale for further attacks, file installation server configuration and much more,” the researchers noted, but not prior to acquiring escalated privileges to carry out the jobs and transmit the final results to a command-and-regulate (C2) server.
In the 5 a long time due to the fact the Explosive RAT was very first seen, ClearSky said new anti-debugging attributes were being extra to the implant in its most current iteration (V4), with the communications amongst the compromised equipment and the C2 server now encrypted.
Even though it is not shocking for menace actors to hold a minimal profile, the reality that Lebanese Cedar managed to continue to be hidden given that 2015 with out attracting any notice by any means indicates the group may possibly have ceased operations for prolonged periods in amongst to keep away from detection.
ClearSky observed that the group’s use of web shell as its key hacking tool could have been instrumental in main scientists to a “lifeless-end in conditions of attribution.”
“Lebanese Cedar has shifted its concentration appreciably. In the beginning they attacked pcs as an preliminary issue of obtain, then progressed to the victim’s network then further progressing (sic) to targeting susceptible, community struggling with web servers,” the researchers additional.
Identified this post exciting? Abide by THN on Facebook, Twitter and LinkedIn to read more distinctive content material we article.
Some pieces of this report are sourced from:
thehackernews.com

 US Breach Volumes Fell 19% in 2020 as Ransomware Surges
US Breach Volumes Fell 19% in 2020 as Ransomware Surges