Present day admins unquestionably have a lot on their plates, and boosting ecosystem security continues to be a prime precedence. On-premises, and especially distant, accounts are gateways for accessing critical information.
Password management helps make this possible. Following all, authentication ought to guarantee that a user is whom they assert to be. This original layer of security is critical for defending one’s entire infrastructure.
Sadly, the personalized character of passwords has its shortcomings. Passwords are simply neglected. They could also be too simplistic lots of corporations you should not enforce stringent password-creation prerequisites. This is where by the Active Listing Password Coverage arrives in.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Furthermore, the subsequent is achievable:
- Modifying user passwords
- Recording password modifications and storing them within just a historical past log
Energetic Listing accounts for any impactful adjustments across user accounts. We’ll evaluate why and how administrators could leverage these main capabilities.
Why change person passwords?
We have touched on the most innocuous purpose for many password improvements: forgetfulness. People may well fail to try to remember login credentials for a quantity of good reasons. Following verification (or a rapid help desk chat), Active Listing administrators can swiftly restore one’s account accessibility. Efficiency may or else endure.
Security is one more driver, while in a few distinctive respects. To start with, infrastructure is topic to a lot of threats. Attacks, facts leaks, and insufficient safeguards may possibly expose passwords to prying eyes. Altering compromised passwords can thwart undesirable actors.
Next, a given password may well be to some degree easy to guess, in spite of current password specifications. An worker could use conditions viewed as ‘low-hanging fruit’ for outsiders attempting to guess passwords or launch brute force attacks. For instance, Apple workers must keep away from utilizing strings containing “Apple” or “Steve Positions” in just their passwords.
Thirdly, occupation roles and work statuses modify consistently throughout corporations. These dictate what resources workforce may perhaps obtain. It is critical that staff members can’t watch non-applicable paperwork or data or benefit from particular packages. In addition, admins will need to terminate internal accounts for ex-employees. Even though not technically a password alter, in the way we imagine, this entails deletion of one’s qualifications.
Why report historic password changes?
Password changes are quite prevalent in the IT realm. However, monitoring and logging alterations can support admins detect fishy activity. Password adjustments only manifest by way of the person or Energetic Listing administrator. Any password transform by a different actor could signify a hack. These exercise logs can assist teams track suspicious occurrences or mitigate pending disaster.
Undesirable actors can steal information. They may carry out password resets—temporarily solidifying their account access while locking reputable buyers out. Password alter histories can protect against leaks and limit downtime.
How to Modify a User Password in Active Listing
Active Listing is tailor-created for Windows networks. Therefore, there are multiple techniques in which Advertisement admins can adjust person passwords.
This can be done specifically in just Energetic Directory. Password improvements are possible outside of Advert, by using strategies that right manipulate AD’s databases. We’ll initially discuss the former.
Working with Energetic Directory Users and Computers (ADUC)
ADUC is a supplemental GUI that makes it possible for directors to interact with Active Directory parts. The application allows remote item (buyers and units) administration. ADUC has been a central instrument for 20 decades now and stays a consumer-pleasant alternative for those people weary of PowerShell or if not.
ADUC isn’t really a default part that will come pre-set up on machines. Alternatively, consumers have to have to obtain and put in Distant Server Administration Tools (RSAT). The interface will come bundled with this greater package deal of applications. How do we adjust passwords just after finishing this move?
ADUC allows admins view person users within groups or domains. Microsoft states that ADUC employs Energetic Listing Services Interface (ADSI) steps for placing passwords. This takes place in two approaches: by using Light-weight Listing Obtain Protocol (LDAP) or through the NetUserChangePassword protocol. LDAP demands an SSL link to bolster conversation security among domains and consumers. When altering a password, it is necessary that the user’s previous password is recognised beforehand.
The password transform course of action is pretty easy from right here:
- This is finished by right-clicking a consumer account, deciding upon Reset Password, and creating essential alterations.
Making use of Energetic Listing Administrative Heart (ADAC)
ADAC is newer than ADUC, and though its person base is lesser, it continues to be very helpful for password alterations. ADAC’s GUI helps make this pretty uncomplicated, requiring couple methods following startup. Here is how:
As with ADUC, admins can even have to have users to reset their passwords upon their future login. You will find also a further approach for changing passwords inside ADAC. The ADAC Overview website page has a Reset Password section, which lets an admin to obtain customers in a snap.
Employing PowerShell Instructions
In certain, Windows customers can variety the Set-ADAccountPassword cmdlet and execute it. The benefits of employing PowerShell are two-fold. Sophisticated end users can operate password modifications into existing automation, allowing for for password refreshes at certain intervals. In addition, admins might alter the passwords of numerous buyers concurrently. This is unbelievably beneficial for remediation next a hack or information leak.
Take note that people ought to import their Active Listing module by making use of the Import-module ActiveDirectory command. This opens the doorway for Ad cmdlet utilization. Admins will have to have the Reset Password authorization enabled to enact these changes.
The ideal techniques are as follows, for a sample consumer named usernameX and a new password—passwordY:
Variety the adhering to cmdlet:
Set-ADAccountPassword usernameX -Reset -NewPassword (ConvertTo-SecureString – AsPlainText “passwordY” -Power -Verbose) -PassThru
This mechanically replaces the previous password with no manually inputting the details a next time.
The console will display screen the objects to reflect these changes
Admins may possibly come across the subsequent mistake as a substitute of a affirmation:
Set-ADAccountPassword: The password does not fulfill the size, complexity, or history requirement of the area.
Providers institute case and character demands for security reasons, and the new password does not satisfy those people specifications. Repeat action 1 with a revised password.
1 might allow end buyers adjust their possess passwords upon login by typing the next cmdlet:
Set-ADUser -Identification usernameX -ChangePasswordAtLogon $True
What if we want to reset a batch of passwords, for a certain crew within our business?
PowerShell allows us kind the next to realize this:
get-aduser -filter “department -eq ‘PM Dept’ -AND enabled -eq ‘True'” | Established-ADAccountPassword -NewPassword $NewPasswd -Reset -PassThru | Set-ADuser -ChangePasswordAtLogon $True
This enforces a password change for all job administration teams upon their next login. This is helpful for periodic resets or in response to a workforce-distinct security risk.
How to Examine Password Change Background
There are various external tools for auditing password alterations in Energetic Directory. On the other hand, we’ll concentrate on the indigenous route, which employs the Team Coverage Administration Console (GPMC). Immediately after working GPMC, admins ought to do the following:
A person could also see the party codes 4740 (a consumer was locked out) or 4767 (a user account was unlocked). These aren’t alarming on their possess. Nevertheless, we want to guarantee that these activities occur in live performance with a 4724 or 4723—which indicates an authentic person indeed induced these occasions, as opposed to a nefarious actor.
Audit password improvements with Specops uReset
Specops uReset is a self-services password reset remedy that also aids you maintain an eye on password changes. The Administrative reporting menu delivers statistical knowledge connected to locked accounts and password improvements.
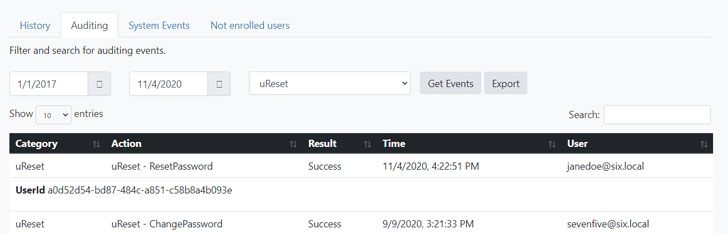
Specops uReset simplifies how you keep an eye on password improvements and can even reduce lockouts by updating the domestically cached qualifications, even when a area controller are not able to be reached.
Stop by Specopssoft to request a free trial of Specops uReset.
Discovered this post fascinating? Observe THN on Facebook, Twitter and LinkedIn to go through far more distinctive material we publish.
Some parts of this post are sourced from:
thehackernews.com


 US Shipping Giant Loses $7.5m in Ransomware Attack
US Shipping Giant Loses $7.5m in Ransomware Attack