Cybersecurity firm Imperva on Friday claimed it not too long ago mitigated a ransom dispersed denial-of-company (DDoS) attack focusing on an unnamed web site that peaked at 2.5 million requests for every next (RPS).
“Whilst ransom DDoS attacks are not new, they surface to be evolving and turning out to be additional exciting with time and with each new period,” Nelli Klepfish, security analyst at Imperva, said. “For case in point, we’ve noticed situations where by the ransom note is incorporated in the attack itself embedded into a URL ask for.”
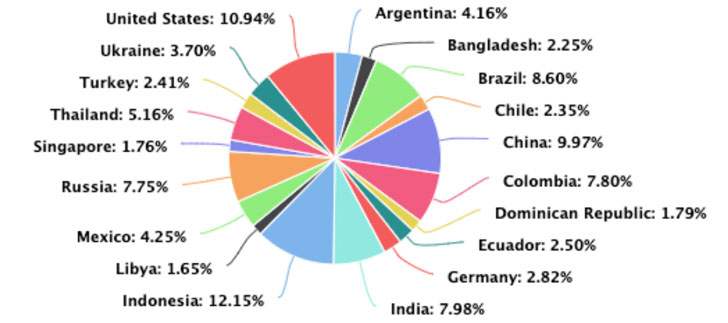
The leading sources of the attacks came from Indonesia, followed by the U.S., China, Brazil, India, Colombia, Russia, Thailand, Mexico, and Argentina.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Dispersed denial-of-service (DDoS) attacks are a subcategory of denial-of-support (DoS) attacks in which an army of connected online gadgets, identified as a botnet, is utilized to overwhelm a focus on site with pretend website traffic in an endeavor to render it unavailable to respectable end users.
The California-headquartered organization reported that the afflicted entity received multiple ransom notes provided as part of the DDoS attacks, demanding the business make a bitcoin payment to keep on line and stay away from dropping “hundreds of millions in market cap.”
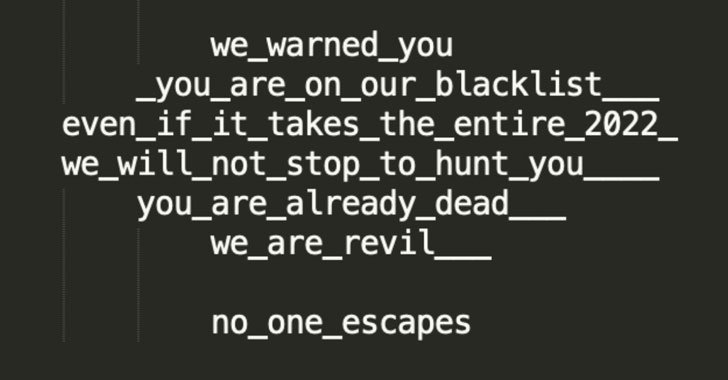
In an intriguing twist, the attackers are contacting on their own REvil, the notorious ransomware-as-a-provider cartel that experienced a important setback just after a amount of its operators were being arrested by Russian legislation enforcement authorities earlier this January.
“It is not clear even so no matter if the threats had been seriously produced by the first REvil team or by an imposter,” Klepfish mentioned.
The 2.5 million RPS attack is said to have lasted less than a minute, with 1 of the sister web pages operated by the exact business sustaining a identical attack that lasted somewhere around 10 minutes, even as the methods used ended up consistently adjusted to avert feasible mitigation.
Proof collected by Imperva details to the DDoS attacks originating from the Mēris botnet, which has continued to leverage a now-tackled security vulnerability in Mikrotik routers (CVE-2018-14847) to strike targets, like Yandex.
“The kinds of web-sites the threat actors are following show up to be business web-sites focusing on sales and communications,” Klepfish mentioned. “Targets have a tendency to be U.S.- or Europe-primarily based with the 1 detail they all have in frequent being that they are all exchange-shown providers and the menace actors use this to their advantage by referring to the likely problems a DDoS attack could do to the enterprise inventory price.”
The findings arrive as destructive actors have been spotted weaponizing a new amplification approach identified as TCP Middlebox Reflection for the quite very first time in the wild to hit banking, journey, gaming, media, and web hosting industries with a flood of fake traffic.
The ransom DDoS attack is also the second botnet-connected action averted by Imperva due to the fact the start of the year, what with the firm detailing a web scraping attack that qualified an unidentified career listing system in late January.
“The attacker utilized a massive-scale botnet, making no much less than 400 million bot requests from practically 400,000 distinctive IP addresses in excess of 4 days with the intent of harvesting job seekers’ profiles,” the security firm reported.
Found this article intriguing? Comply with THN on Fb, Twitter and LinkedIn to examine more special articles we publish.
Some pieces of this posting are sourced from:
thehackernews.com



 CISA Adds Another 95 Flaws to its Actively Exploited Vulnerabilities Catalog
CISA Adds Another 95 Flaws to its Actively Exploited Vulnerabilities Catalog