The amplified use of data technology in our daily life and small business has led to cyber-attacks turning into much more subtle and massive-scale. For corporations to prosper in this era of technology, they must build robust security strategies to detect and mitigate attacks. Protection in depth is a technique in which organizations use multiple levels of security actions to safeguard belongings. A nicely-applied defense in depth can assist companies reduce and mitigate ongoing attacks.
Defense in depth utilizes several chopping-edge security equipment to safeguard a business’s endpoints, information, applications, and networks. The objective is to reduce cyber threats, but a sturdy protection-in-depth technique also thwarts ongoing attacks and stops more hurt.
How companies can put into action protection in depth
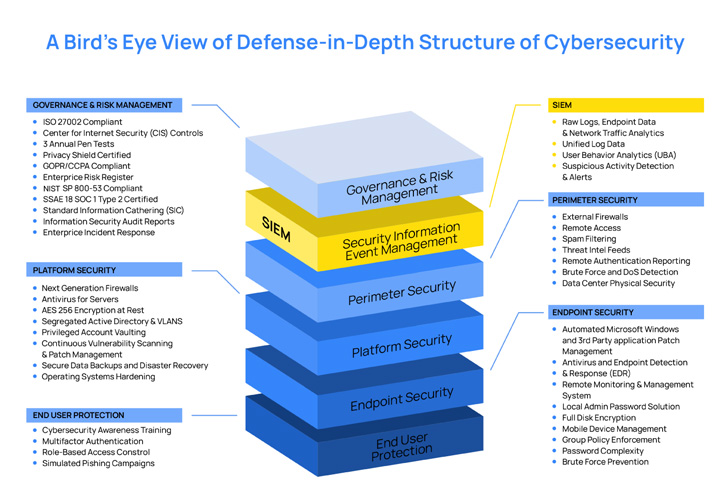 The picture over reveals the a variety of layers of security that corporations have to put into action. Beneath we describe ideas that organizations should really take into account for each layer.
The picture over reveals the a variety of layers of security that corporations have to put into action. Beneath we describe ideas that organizations should really take into account for each layer.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Governance and risk management
Governance and risk administration in cybersecurity revolves close to 3 major components governance, risk, and compliance (GRC). The overarching intent of GRC is to ensure that each member of an corporation is effective jointly to obtain established targets. They have to do this although adhering to authorized and moral suggestions, processes, and compliance specifications. These benchmarks include NIST, PCI-DSS, HIPAA, and GDPR. Institutions will have to establish the expectations that implement to them and use applications to automate and simplify the compliance method. These applications really should be in a position to detect violations and provide reviews and easy-to-comply with documentation to solve the violations.
Platform security
There are many methods organizations can guarantee the security of the equipment in their company network. Two important approaches are vulnerability administration and operating process hardening. Vulnerability administration adds a layer of protection that ensures that corporations tackle weaknesses in program prior to attackers can exploit them. On the other hand, OS hardening makes sure that security teams put into action additional actions to secure the integrity of info and configurations utilised in an operating process. They can do this by defining and imposing insurance policies for endpoints in their network. Other aspects to be certain platform security are firewalls and implementing correct network segmentation.
SIEM
A security data and occasion management (SIEM) resolution is necessary to an organization’s security method. A SIEM aggregates and correlates logs from distinctive resources and generates alerts centered on detection regulations. It also gives a central management portal for triaging and investigating incidents, and becoming ready to obtain and normalize logs from different equipment and systems is just one of the essential characteristics of a fantastic SIEM.
Perimeter security (threat intelligence)
Profitable implementation of protection in depth is not targeted only on the organization’s interior infrastructure but also on danger actor actions. Institutions ought to have a way of collecting and analyzing menace intelligence and utilizing the info to give security for their belongings. Security groups ought to also use firewalls and network segmentation to shield critical infrastructure.
Endpoint security
The endpoints in an firm are critical to its functions, primarily in the 21st century. Endpoint security is essential because attackers ordinarily find to compromise data saved on endpoints. Endpoint security has progressed more than the years from anti-virus solutions to whole-blown antimalware alternatives, and now we are in the period of prolonged detection and response (XDR) options. XDRs go over and above the restrictions of conventional antimalware alternatives by correlating alerts from various sources to give more precise detections. They also leverage SIEM and SOAR (Security Orchestration, Automation, and Response) functionalities to detect threats in many endpoints and reply uniformly and properly to any compromised endpoints.
Wazuh, the free and open resource answer
Wazuh is a totally free, open up resource security platform that features unified SIEM and XDR safety. It protects workloads throughout on-premises, virtualized, containerized, and cloud-primarily based environments. Wazuh provides assistance to security functions with effortless integration to menace intelligence feeds.
In implementing defense in depth, no one software can protect all levels of security. Having said that, Wazuh gives numerous characteristics that companies can use to improve their security infrastructure. For GRC, Wazuh presents focused dashboards that watch and investigate events brought on by PCI-DSS, HIPAA, and GDPR violations. The remedy also has a vulnerability detector module with out-of-the-box integration with vulnerability feeds, which scans working systems and apps for known vulnerabilities.
Wazuh also offers a Security Configuration Evaluation (SCA) module that allows buyers to make guidelines that the Wazuh server applies to every single endpoint in their environment. Companies can use vulnerability detector and SCA modules to fortify the security of the working systems and apps deployed on their endpoints.
As an XDR, Wazuh correlates security information from various sources to detect threats in an organization’s environment. Also, it can actively mitigate threats by working with its energetic reaction functionality.
Wazuh is one of the swiftest-developing open up source security remedies, with above 10 million downloads for every calendar year. Wazuh also presents communities exactly where users can interact Wazuh developers, share activities, and question thoughts relevant to the system. Examine out this documentation on how to get begun with Wazuh.
Discovered this short article exciting? Comply with THN on Facebook, Twitter and LinkedIn to examine additional distinctive content material we post.
Some areas of this report are sourced from:
thehackernews.com


 Google Issues Urgent Chrome Update to Patch Actively Exploited Zero-Day Vulnerability
Google Issues Urgent Chrome Update to Patch Actively Exploited Zero-Day Vulnerability