An preliminary access broker group tracked as Prophet Spider has been linked to a set of malicious pursuits that exploits the Log4Shell vulnerability in unpatched VMware Horizon Servers.
In accordance to new investigation printed by BlackBerry Investigate & Intelligence and Incident Response (IR) groups nowadays, the cybercrime actor has been opportunistically weaponizing the shortcoming to download a 2nd-phase payload onto the victimized programs.
The payloads noticed incorporate cryptocurrency miners, Cobalt Strike Beacons, and web shells, corroborating a former advisory from the U.K. Nationwide Health Service (NHS) that sounded the alarm on active exploitation of the vulnerabilities in VMware Horizon servers to fall destructive web shells and build persistence on impacted networks for stick to-on attacks.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Log4Shell is a moniker applied to refer to an exploit impacting the well known Apache Log4j library that success in remote code execution by logging a specifically crafted string. Considering the fact that community disclosure of the flaw past month, threat actors have been swift to operationalize this new attack vector for a assortment of intrusion campaigns to get full manage of impacted servers.
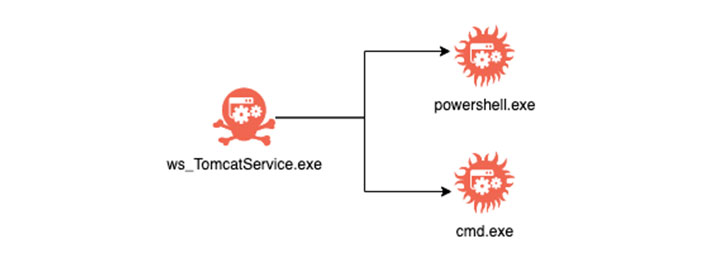
BlackBerry claimed it noticed occasions of exploitation mirroring tactics, techniques, and methods (TTPs) beforehand attributed to the Prophet Spider eCrime cartel, together with the use of “C:WindowsTemp7fde” folder path to store destructive files and “wget.bin” executable to fetch more binaries as nicely as overlaps in infrastructure utilized by the team.
“Prophet Spider primarily gains access to victims by compromising vulnerable web servers, and makes use of a variety of minimal-prevalence applications to attain operational objectives,” CrowdStrike mentioned in August 2021, when the team was spotted actively exploiting flaws in Oracle WebLogic servers to get initial obtain to target environments.
Like with a lot of other initial access brokers, the footholds are sold to the highest bidder on underground community forums positioned in the dark web, who then exploit the accessibility for ransomware deployment. Prophet Spider is recognized to be active considering that at minimum May well 2017.
This is far from the to start with time internet-facing techniques running VMware Horizon have arrive below attack applying Log4Shell exploits. Before this month, Microsoft identified as out a China-based operator tracked as DEV-0401 for deploying a new ransomware strain referred to as NightSky on the compromised servers.
The onslaught versus Horizon servers has also prompted VMware to urge its clients to utilize the patches promptly. “The ramifications of this vulnerability are significant for any technique, especially ones that acknowledge visitors from the open up Internet,” the virtualization expert services service provider cautioned.
“When an entry broker group usually takes curiosity in a vulnerability whose scope is so unknown, it’s a great indication that attackers see significant benefit in its exploitation,” Tony Lee, vice president of world wide companies complex operations at BlackBerry, stated.
“It really is likely that we will carry on to see legal groups checking out the possibilities of the Log4Shell vulnerability, so it really is an attack vector versus which defenders require to exercise regular vigilance,” Lee extra.
.
Observed this article interesting? Stick to THN on Fb, Twitter and LinkedIn to examine a lot more exclusive content material we article.
Some areas of this write-up are sourced from:
thehackernews.com



 Vodafone: Personal data might become new currency by 2030
Vodafone: Personal data might become new currency by 2030