An sophisticated persistent risk (APT) group with ties to Iran has refreshed its malware toolset to include things like a new backdoor dubbed Marlin as aspect of a lengthy-jogging espionage campaign that started in April 2018.
Slovak cybersecurity business ESET attributed the attacks — code named Out to Sea — to a menace actor known as OilRig (aka APT34), while also conclusively connecting its routines to a 2nd Iranian team tracked beneath the title Lyceum (Hexane aka SiameseKitten).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
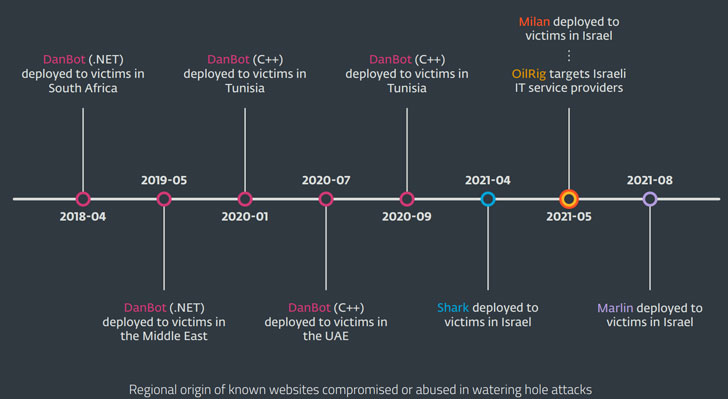
“Victims of the campaign incorporate diplomatic businesses, technology providers, and clinical companies in Israel, Tunisia, and the United Arab Emirates,” ESET pointed out in its T3 2021 Threat Report shared with The Hacker Information.
Active due to the fact at the very least 2014, the hacking group is acknowledged to strike Middle Eastern governments and a wide range of business enterprise verticals, such as chemical, vitality, economic, and telecommunications. In April 2021, the actor specific a Lebanese entity with an implant called SideTwist, while strategies earlier attributed to Lyceum have singled out IT organizations in Israel, Morocco, Tunisia, and Saudi Arabia.
The Lyceum an infection chains are also notable for the simple fact that they have advanced to fall multiple backdoors since the campaign came to light-weight in 2018 — commencing with DanBot and transitioning to Shark and Milan in 2021 — with attacks detected in August 2021 leveraging a new details collection malware named Marlin.
The adjustments never finish there. In what is actually a important departure from classic OilRig TTPs, which have involved the use of DNS and HTTPS for command-and-regulate (C&C) communications, Marlin tends to make use of Microsoft’s OneDrive API for its C2 operations.
ESET, noting that first accessibility to the network was accomplished by signifies of spear-phishing as very well as remote access and administration software program like ITbrain and TeamViewer, cited similarities in resources and tactics in between OilRig’s backdoors and that of Lyceum as “far too various and precise.”
“The ToneDeaf backdoor mainly communicated with its C&C in excess of HTTP/S but included a secondary process, DNS tunneling, which does not functionality correctly,” the researchers explained. “Shark has similar indications, in which its main communication strategy works by using DNS but has a non-functional HTTP/S secondary solution.”
ToneDeaf, which supports gathering process information, uploading and downloading of documents, and arbitrary shell command execution, is a malware family that was deployed by the APT34 actor targeting a broad selection of industries functioning in the Center East in July 2019.
Furthermore, the results also pointed out the overlapping use of DNS as a C&C conversation channel, although also utilizing HTTP/S as a secondary interaction method and the use of various folders in a backdoor’s operating directory for uploading and downloading documents from the C&C server.
Discovered this short article fascinating? Abide by THN on Fb, Twitter and LinkedIn to examine a lot more exclusive content we put up.
Some elements of this write-up are sourced from:
thehackernews.com




 Microsoft’s Patch Tuesday fixes 70 vulnerabilities after a troublesome January update
Microsoft’s Patch Tuesday fixes 70 vulnerabilities after a troublesome January update